 When push-based multifactor authentication (MFA) first got here out, I used to be a giant fan. I promoted it as a powerful and secure MFA choice in my e-book, Hacking Multifactor Authentication. That was earlier than I spotted {that a} non-small proportion of customers would willingly approve logins they in any other case had nothing to do with, as soon as once more undermining the most effective intentions of the newest expertise with sudden human conduct. That is the unstoppable, repeatable story of cybersecurity.
When push-based multifactor authentication (MFA) first got here out, I used to be a giant fan. I promoted it as a powerful and secure MFA choice in my e-book, Hacking Multifactor Authentication. That was earlier than I spotted {that a} non-small proportion of customers would willingly approve logins they in any other case had nothing to do with, as soon as once more undermining the most effective intentions of the newest expertise with sudden human conduct. That is the unstoppable, repeatable story of cybersecurity.
Since then, I’ve written so much about push-based MFA, the way it works, and the nice and unhealthy of it, methods to enhance it, together with right here:
Push-Based mostly MFA
Push-based MFA sends an approval message to a person’s system, often a cellular phone, which they need to manually approve in an effort to efficiently log into push-based-protected websites. The push-based message is commonly despatched by way of SMS textual content or to a phone-based/device-based app (see Google instance beneath).
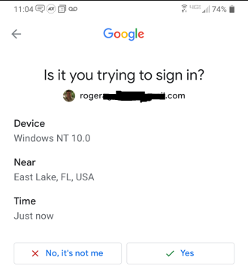
Quantity Match MFA Answer
In April of this 12 months, I wrote a few new characteristic, commonly known as “quantity matching MFA” that promised to enhance the safety of push-based authentication. Initially, carried out as a part of Microsoft’s and Google’s push-based MFA “beta” options, Duo Safety and different distributors even have it or plan so as to add it as a characteristic.
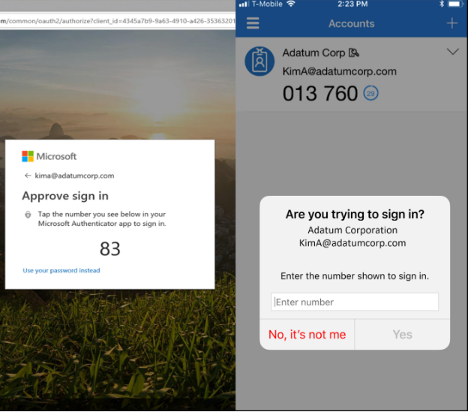
In a nutshell, quantity match adjustments the push-based-protected login display screen to show a quantity, often two digits between one and 99, throughout a login. The person getting a push-based login message to evaluate, should know the quantity and sort it or accurately choose it on the push-based login approval display screen, to have the ability to approve the concerned login.
Right here is an instance (proven beneath) from Microsoft:
Some options ask the person to pick the fitting quantity as an alternative of typing it in (instance from Google proven beneath).
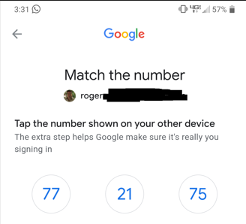
The latter message might be going to have much less errors as a result of there may be much less of an opportunity for a person to kind within the improper digits and it solely takes one motion as an alternative three (as indicated within the former instance). The second instance’s GUI is best. Much less person friction.
The quantity match will increase the percentages that the person concerned in approving the login has really seen the login display screen through the associated login try.
It’s a good suggestion. Even CISA has come out to help quantity matching push-based MFA.
Whereas it’s a good suggestion, it isn’t an ideal concept. In case you have or plan to implement push-based MFA, you must allow this characteristic whether it is accessible. However it doesn’t cease all the assaults towards push-based MFA. In the event you suppose it does, you’ll possible find yourself hacked.
Quantity matching will increase the percentages that the approver is sitting in entrance of the login display screen, nevertheless it doesn’t assure it. Lots of the most infamous hacks involving push-based MFA have occurred as a result of the attacker referred to as the sufferer, pretending to be from IT, and informed the sufferer they wanted to approve the login. That attacker can simply as simply add, “And the quantity match is 21.” If the sufferer is incentivized and going to approve the fraudulent login anyway, why would quantity match cease them from a decided adversary who’s social engineering them over the cellphone?
Quantity matching will forestall a person from approving a bunch of sudden prompts, at the very least with out having to have somebody inform them the quantity or from seeing it themselves. I’m not positive how a lot of push-based MFA phishing entails simply the login immediate showing versus the sufferer being contacted by the attacker, however it’s sure to be a decrease proportion of the latter. How a lot decrease? It’s anybody’s guess. But when I needed to guess, I guess quantity matching would put down 50% to 75% of push-based MFA assaults. That’s fairly good. However which means 25% to 50% of assaults will nonetheless succeed.
I count on as quantity matching turns into extra the norm within the push-based MFA world, that hackers will merely adapt. The hackers who by no means used to fret about and work round quantity matching will merely begin doing so. And due to this fact, the quantity of safety supplied by quantity matching will lower over time. Nonetheless, it helps so much, and so, you must allow it. It’s simply not good.
MFA Hacking Protection
Are you aware what is best? What would work near 100% of the time?
Schooling.
As you hand out push-based MFA to your customers, educate them concerning the widespread sorts of assaults towards push-based MFA, whether or not quantity matching is enabled or not. Inform them that you simply and nobody working in your group will ever ask them to approve a immediate that they themselves, the person, didn’t provoke. Inform them that official IT won’t ever contact them and ask them to approve an issue. Inform them that if anybody contacts them and claims to have the authority to drive them to approve a login that they themselves, the potential sufferer, didn’t provoke, that they’re allowed…no…required…to disclaim that login request. After which they need to instantly contact IT/IT Safety to report the doable breach try. Inform them that there isn’t a believable situation the place they are going to be requested to approve a login that they themselves didn’t provoke. It really works higher than a quantity match.
Somewhat schooling goes a great distance. New-school safety consciousness coaching can allow your staff to thwart evolving MFA-based assaults.


