Supply code auditing and static code evaluation
Aura is a static evaluation framework developed as a response to the ever-increasing risk of malicious packages and weak code printed on PyPI.
Venture objectives:
- present an automatic monitoring system over uploaded packages to PyPI, alert on anomalies that may both point out an ongoing assault or vulnerabilities within the code
- allow a company to conduct automated safety audits of the supply code and implement safe coding practices with a give attention to auditing third get together code comparable to python package deal dependencies
- enable researches to scan code repositories on a big scale, create datasets and carry out evaluation to additional advance analysis within the space of weak and malicious code dependencies
Function record:
- Appropriate for analyzing malware with a assure of a zero-code execution
- Superior deobfuscation mechanisms by rewriting the AST tree – fixed propagations, code unrolling, and different soiled tips
- Recursive scanning mechanically unpacks archives comparable to zips, wheels, and many others.. and scans the content material
- Help scanning additionally non-python information – plugins can work in a “raw-file” mode such because the built-in Yara integration
- Scan for hardcoded secrets and techniques, passwords, and different delicate data
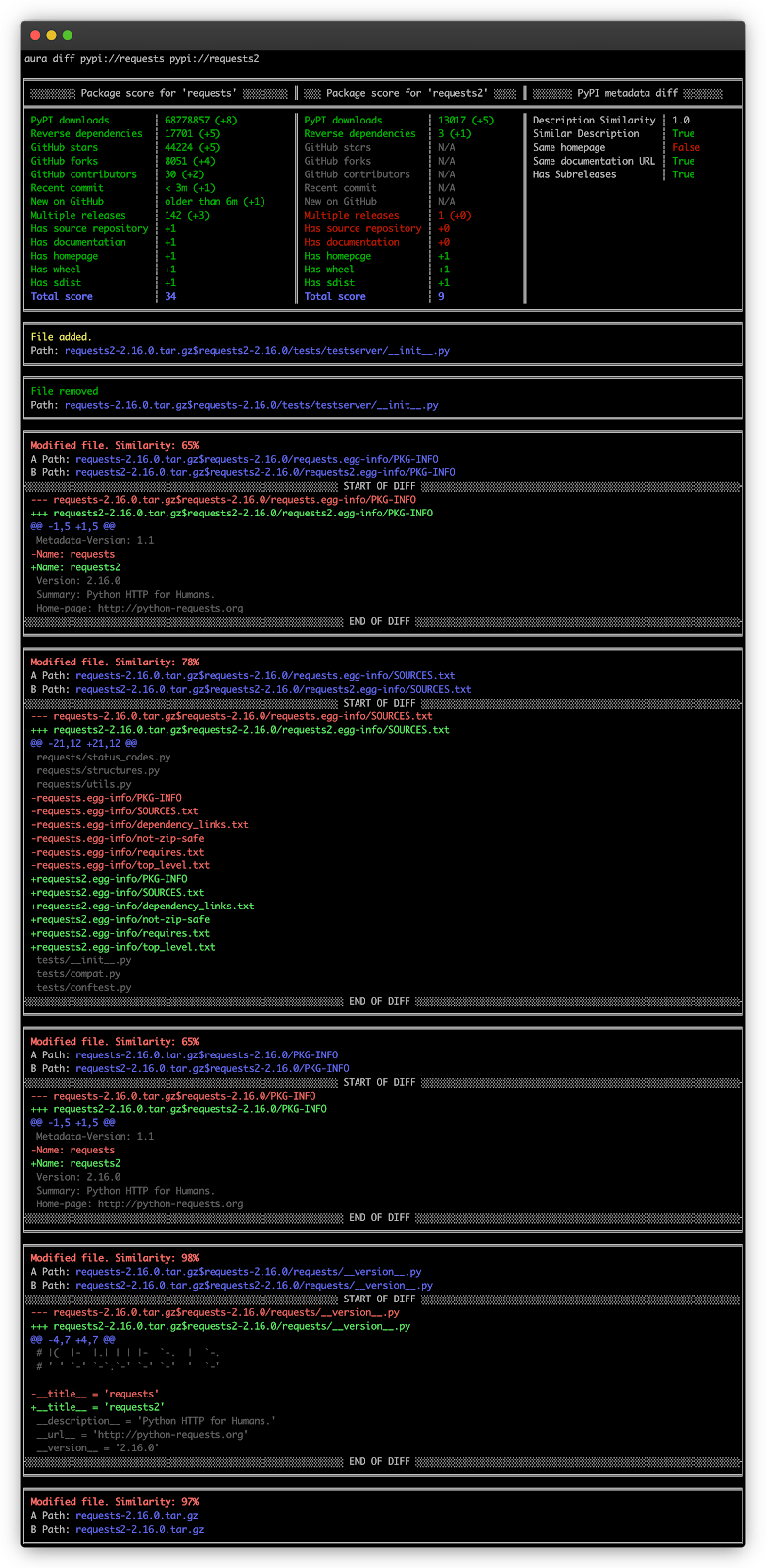
- Customized diff engine – you possibly can examine modifications between completely different information sources comparable to typosquatting PyPI packages to what modifications had been made
- Works for each Python 2.x and Python 3.x supply code
- Excessive efficiency, designed to scan the entire PyPI repository
- Output in quite a few codecs comparable to fairly plain textual content, JSON, SQLite, SARIF, and many others…
- Examined on over 4TB of compressed python supply code
- Aura is ready to report on code conduct comparable to community communication, file entry, or system command execution
- Compute the “Aura rating” telling you ways reliable the supply code/enter information is
- and far far more…
Did not discover what you might be in search of? Aura’s structure is predicated on a sturdy plugin system, the place you possibly can customise virtually something, starting from a set of information analyzers, transport protocols to customized out codecs.
Set up
# Through pip:
pip set up aura-security[full]
# or construct from supply/git
poetry set up --no-dev -E full
Or simply use a prebuild docker picture sourcecodeai/aura:dev
Operating Aura
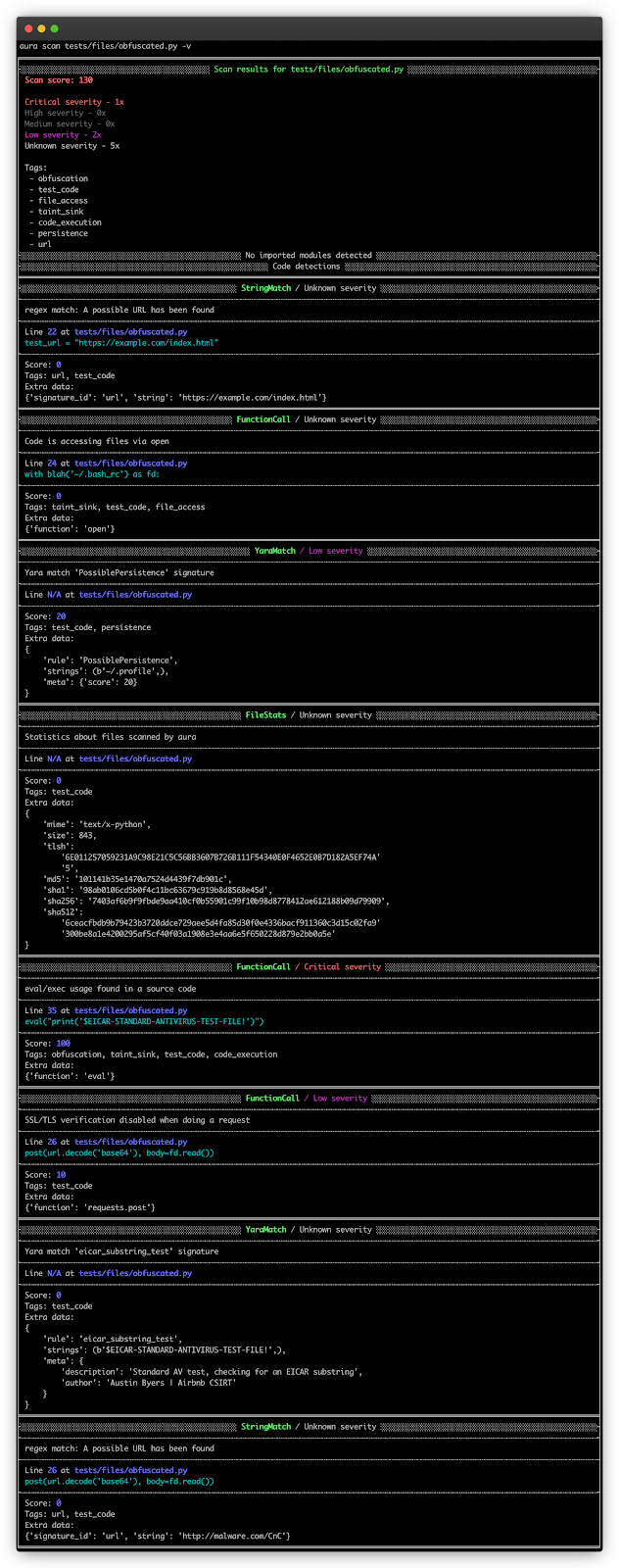
docker run -ti --rm sourcecodeai/aura:dev scan pypi://requests -v
Aura makes use of a so-called URIs to determine the protocol and placement to scan, if no protocol is used, the scan argument is handled as a path to the file or listing on a neighborhood system.
Diff packages:
docker run -ti --rm sourcecodeai/aura:dev diff pypi://requests pypi://requests2
Discover hottest typosquatted packages (it’s essential to name aura replace to obtain the dataset first):
aura find-typosquatting --max-distance 2 --limit 10
Why Aura?
Whereas there are different instruments with performance that overlaps with Aura comparable to Bandit, dlint, semgrep and many others. the main target of those alternate options is completely different which impacts the performance and the way they’re getting used. These alternate options are primarily meant for use in an identical technique to linters, built-in into IDEs, continuously run through the improvement which makes it vital to decrease false positives and reporting with clear actionable explanations in splendid instances.
Aura then again reviews on ** conduct of the code**, anomalies, and vulnerabilities with as a lot data as potential at the price of false optimistic. There are loads of issues reported by aura that aren’t essentially actionable by a consumer however they inform you a large number in regards to the conduct of the code comparable to doing community communication, accessing delicate information, or utilizing mechanisms related to obfuscation indicating a potential malicious code. By amassing this type of information and aggregating it collectively, Aura could be in contrast in performance to different safety programs comparable to antivirus, IDS, or firewalls which can be basically doing the identical evaluation however on a special sort of information (community communication, operating processes, and many others).
Here’s a fast overview of variations between Aura and different comparable linters and SAST instruments:
-
- enter information:
-
- Different SAST instruments – normally restricted to solely python (goal) supply code and python model beneath which the instrument is put in.
- Aura can analyze each binary (or non-python code) and python supply code as nicely. Capable of analyze a mix of python code suitable with completely different python variations (py2k & py3k) utilizing the identical Aura set up.
-
- reporting:
-
- Different SAST instruments – Goals at integrating nicely with different programs comparable to IDEs, CI programs with actionable outcomes whereas attempting to attenuate false positives to stop overwhelming customers with too many non-significant alerts.
- Aura – reviews as a lot data as potential that isn’t instantly actionable comparable to behavioral and anomaly evaluation. The output format is designed for straightforward machine processing and aggregation fairly than human readable.
-
- configuration:
-
- Different SAST instruments – The instruments are fine-tuned to the goal challenge by customizing the signatures to focus on particular applied sciences utilized by the goal challenge. The overriding configuration is usually potential by inserting feedback contained in the supply code comparable to
# nosecthat can suppress the alert at that place - Aura – it’s anticipated that there’s little to no information upfront in regards to the applied sciences utilized by code that’s being scanned comparable to auditing a brand new python package deal for approval for use as a dependency in a challenge. Usually, it isn’t even potential to switch the scanned supply code comparable to utilizing feedback to point to linter or aura to skip detection at that location as a result of it’s scanning a duplicate of that code that’s hosted at some distant location.
- Different SAST instruments – The instruments are fine-tuned to the goal challenge by customizing the signatures to focus on particular applied sciences utilized by the goal challenge. The overriding configuration is usually potential by inserting feedback contained in the supply code comparable to
Authors & Contributors
Donate
LICENSE
Aura framework is licensed beneath the GPL-3.0. Datasets produced from world scans utilizing Aura are launched beneath the CC BY-NC 4.0 license. Use the next quotation when utilizing Aura or information produced by Aura in analysis:
@misc{Carnogursky2019thesis,
AUTHOR = "CARNOGURSKY, Martin",
TITLE = "Assaults on package deal managers [online]",
YEAR = "2019 [cit. 2020-11-02]",
TYPE = "Bachelor Thesis",
SCHOOL = "Masaryk College, College of Informatics, Brno",
SUPERVISOR = "Vit Bukac",
URL = "Accessible at WWW <https://is.muni.cz/th/y41ft/>",
}