The Python Bundle Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing marketing campaign that goals to steal developer credentials and inject malicious updates to authentic packages.
“That is the primary identified phishing assault towards PyPI,” the maintainers of the official third-party software program repository stated in a sequence of tweets.
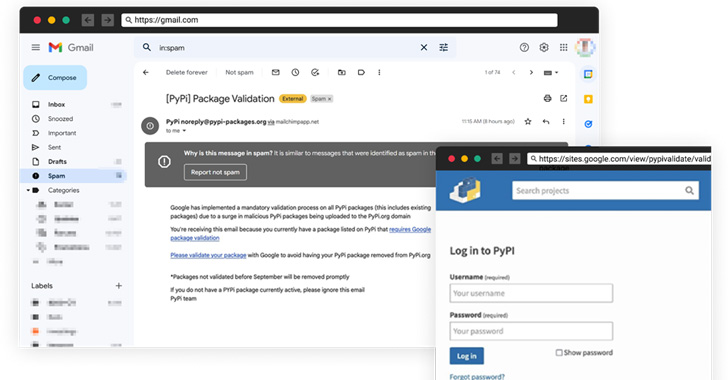
The social engineering assault entails sending security-themed messages that create a false sense of urgency by informing recipients that Google is implementing a compulsory validation course of on all packages and that they should click on on a hyperlink to finish the validation earlier than September, or threat getting their PyPI modules eliminated.
Ought to an unsuspecting developer fall for the scheme, customers are directed to a lookalike touchdown web page that mimics PyPI’s login web page and is hosted on Google Websites, from the place the entered credentials are captured and abused to unauthorizedly entry the accounts and compromise the packages to incorporate malware.
The modifications, for his or her half, are designed to obtain a file from a distant server. “This malware is untypically giant, ~63MB, (presumably in an try and evade [antivirus] detection) and has a legitimate signature (signed on August twenty third, 2022),” Checkmarx researcher Aviad Gershon famous.
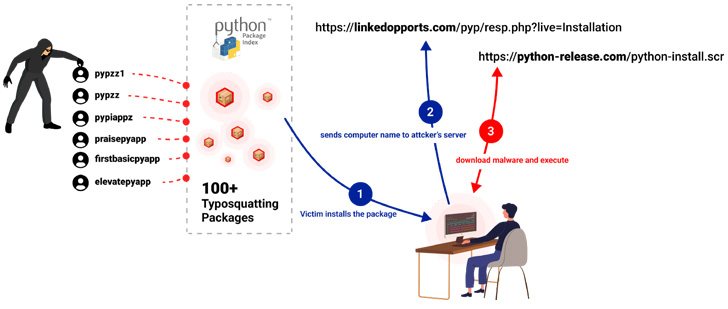
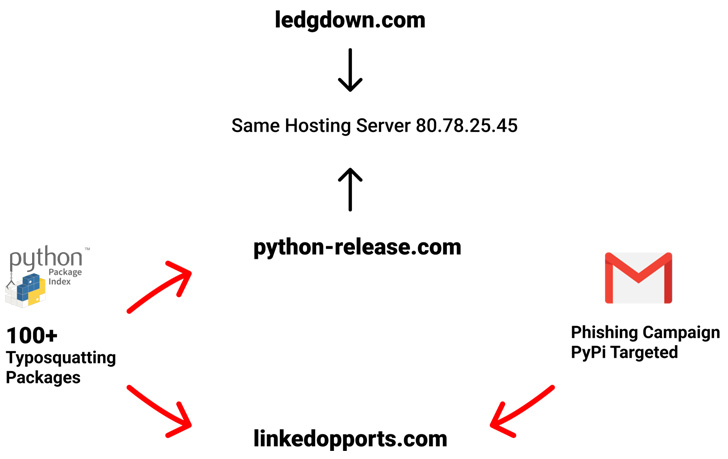
“These releases have been faraway from PyPI and the maintainer accounts have been quickly frozen,” PyPI stated. Two of the affected packages to this point embrace “exotel” and “spam.” Moreover, a number of hundred typosquats are stated to have been eliminated.
PyPI additionally stated it is actively monitoring stories of latest rogue packages and making certain their elimination. Builders who imagine they could have been compromised ought to reset their passwords with fast impact, reset 2FA restoration codes, and evaluation PyPI account logs for anomalous exercise.
The phishing assault is one more signal of how the open supply ecosystem is more and more in danger from menace actors, who’re capitalizing on libraries and tasks which are woven into the material of a number of functions to mount provide chain assaults that may have cascading results.
Earlier this month, researchers from Checkmarx disclosed two malicious Python packages – typing-unions and aiogram-types – that impersonated common packages typing and aiogram to trick builders into downloading them and infecting their machines with Cobalt Strike.
One other large-scale assault concerned a menace actor publishing a dozen typosquatted packages below the names of common tasks with slight permutations to put in a multi-stage persistent malware on compromised methods.
The event additionally arrived over two months after the registry started imposing a compulsory two-factor authentication (2FA) requirement for tasks deemed “vital.”