I got here throughout this python script that may carry out SSH login bruteforce assaults and determined I’d share it with you guys. The perfect factor about this device is that it’s going to not flagged by an AV as Hydra would. The straightforward Python script gained’t be detected as a software program device, permitting for a lot simpler evasion. It really works as a wrapper round PuTTY SSH shoppers and may be ran in a graphical surroundings or in a command line interface.
Listed here are a listing of options listed on the InfosecMatter web site:
- Performs SSH login assaults utilizing both putty.exe or plink.exe
- Written in pure PowerShell – no extra modules wanted
- Non-malicious – undetected by any antivirus or endpoint safety resolution
- Sensible and good design:
- Helps a single password assault or a dictionary assault
- Permits performing password spraying throughout a number of SSH servers
- Helps resuming, if interrupted
- Avoids re-trying the identical credentials
- Skips already compromised SSH account
The script has been examined on Home windows 10, PuTTY releases 0.68 and 0.73 and Powershell variations 4 and 5. As a single-threaded loop, it exams every account individually so pace is compromised on the expense of usability. To make use of the device, one or each executables should be added to PATH or the present listing.
How SSH Bruteforce Works
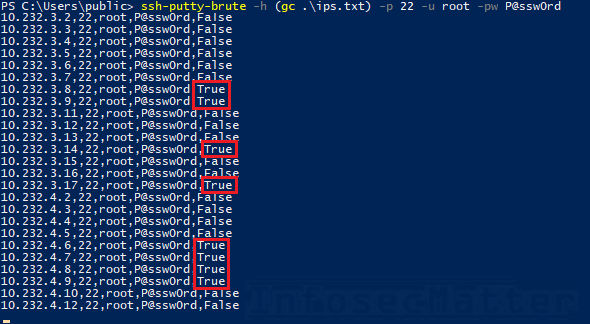
ssh-putty-brute.ps1 makes use of numerous command line parameters of PuTTY shoppers by making an attempt to login one after the other and observing output of the chosen consumer to inform if the try was profitable or not. You’ll be able to retrieve outcomes from the log file created within the working listing. The device additionally makes use of this log file to maintain observe of the whole lot because it checks this file after each login try to find out success or failure. Due to this characteristic the script won’t ever examine the identical mixture greater than as soon as.
Utilization is straightforward. Under are just a few utilization examples:
import-module .ssh-putty-brute.ps1
# Utilization:
ssh-putty-brute [-h ip|ips.txt] [-p port] [-u user|users.txt] [-pw pass|pwdlist.txt]
# Examples:
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw [email protected]
ssh-putty-brute -h 10.10.5.11 -p 22 -u root -pw (Get-Content material .pwdlist.txt)Conclusion
InfosecMatter pulled a rabbit out of a hat with this one. I examined this device on a community and was capable of evade detection from Defender and Cisco. We charge this one 4/5 bunnies because of its ease of use and applicability in addition to its skill to discourage AV. Add this device to your arsenal right here GitHub




Need to study extra about moral hacking?
We’ve got a networking hacking course that’s of the same stage to OSCP, get an unique low cost right here
Assist assist LHN by shopping for a T-shirt or a mug?
Take a look at our choice right here
Are you aware of one other GitHub associated hacking device?
Get in contact with us by way of the contact type if you need us to have a look at every other GitHub moral hacking instruments.