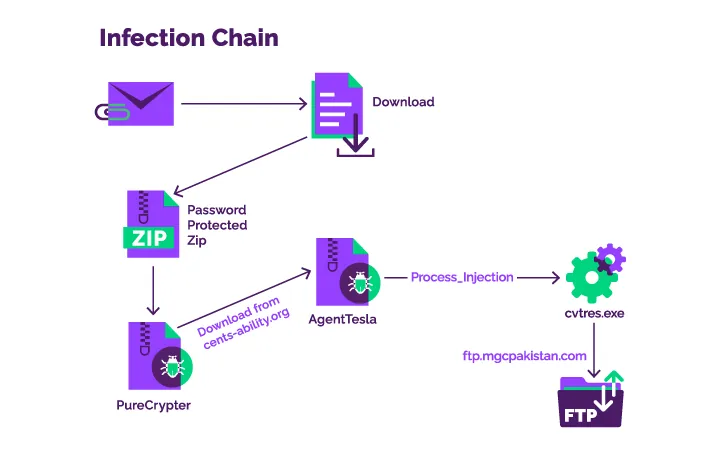
Authorities entities in Asia-Pacific and North America are being focused by an unknown risk actor with an off-the-shelf malware downloader often called PureCrypter to ship an array of knowledge stealers and ransomware.
“The PureCrypter marketing campaign makes use of the area of a compromised non-profit group as a command-and-control (C2) to ship a secondary payload,” Menlo Safety researcher Abhay Yadav stated.
The several types of malware propagated utilizing PureCrypter embody RedLine Stealer, Agent Tesla, Eternity, Blackmoon (aka KRBanker), and Philadelphia ransomware.
First documented in June 2022, PureCrypter is marketed on the market by its creator for $59 for one-month entry (or $245 for a one-off lifetime buy) and is able to distributing a mess of malware.
In December 2022, PureCoder – the developer behind this system – expanded the slate of choices to incorporate a logger and data stealer often called PureLogs, which is designed to siphon information from internet browsers, crypto wallets, and electronic mail shoppers. It prices $99 a yr (or $199 for lifetime entry).
The an infection sequence detailed by Menlo Safety commences with a phishing electronic mail containing a Discord URL that factors to the first-stage element, a password-protected ZIP archive that, in flip, masses the PureCrypter malware.
The loader, for its half, reaches out to the web site of the breached non-profit entity to fetch the secondary payload, which is a .NET-based keylogger named Agent Tesla.
The backdoor then establishes a connection to an FTP server situated in Pakistan to exfiltrate the harvested information, indicating that compromised credentials might have been used to carry out the exercise.