In a unbroken signal that menace actors are adapting effectively to a post-macro world, it has emerged that the usage of Microsoft OneNote paperwork to ship malware by way of phishing assaults is on the rise.
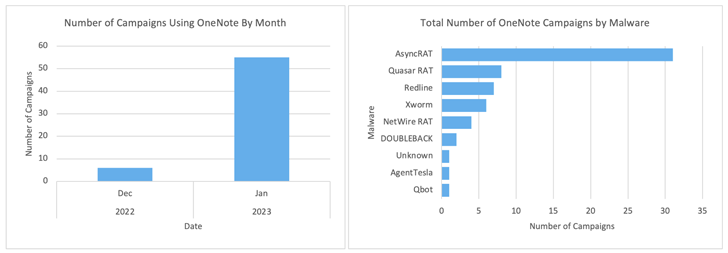
A number of the notable malware households which can be being distributed utilizing this technique embody AsyncRAT, RedLine Stealer, Agent Tesla, DOUBLEBACK, Quasar RAT, XWorm, Qakbot, BATLOADER, and FormBook.
Enterprise agency Proofpoint stated it detected over 50 campaigns leveraging OneNote attachments within the month of January 2023 alone.
In some cases, the e-mail phishing lures include a OneNote file, which, in flip, embeds an HTA file that invokes a PowerShell script to retrieve a malicious binary from a distant server.
Different eventualities entail the execution of a rogue VBScript that is embedded inside the OneNote doc and hid behind a picture that seems as a seemingly innocent button. The VBScript, for its half, is designed to drop a PowerShell script to run DOUBLEBACK.
“You will need to be aware, an assault is barely profitable if the recipient engages with the attachment, particularly by clicking on the embedded file and ignoring the warning message displayed by OneNote,” Proofpoint stated.
The an infection chains are made potential owing to a OneNote characteristic that enables for the execution of choose file varieties immediately from inside the note-taking software in what’s a case of a “payload smuggling” assault.
“Most file varieties that may be processed by MSHTA, WSCRIPT, and CSCRIPT may be executed from inside OneNote,” TrustedSec researcher Scott Nusbaum stated. “These file varieties embody CHM, HTA, JS, WSF, and VBS.”
As remedial actions, Finnish cybersecurity agency WithSecure is recommending customers block OneNote mail attachments (.one and .onepkg information) and preserve shut tabs on the operations of the OneNote.exe course of.
The shift to OneNote is seen as a response to Microsoft’s resolution to disallow macros by default in Microsoft Workplace purposes downloaded from the web final yr, prompting menace actors to experiment with unusual file varieties resembling ISO, VHD, SVG, CHM, RAR, HTML, and LNK.
The purpose behind blocking macros is two-fold: To not solely cut back the assault floor but additionally enhance the trouble required to tug off an assault, whilst e-mail continues to be the prime supply vector for malware.
However these should not the one choices which have grow to be a preferred technique to conceal malicious code. Microsoft Excel add-in (XLL) information and Writer macros have additionally been put to make use of as an assault pathway to skirt Microsoft’s protections and propagate a distant entry trojan known as Ekipa RAT and different backdoors.
The abuse of XLL information hasn’t gone unnoticed by the Home windows maker, which is planning an replace to “block XLL add-ins coming from the web,” citing an “rising variety of malware assaults in current months.” The choice is predicted to be accessible someday in March 2023.
When reached for remark, Microsoft instructed The Hacker Information that it had nothing additional to share presently.
“It is clear to see how cybercriminals leverage new assault vectors or less-detected means to compromise consumer units,” Bitdefender’s Adrian Miron stated. “These campaigns are prone to proliferate in coming months, with cybercrooks testing out higher or improved angles to compromise victims.”