ACM.61 Including customized route tables with names to our AWS VPCs
It is a continuation of my collection of posts on Automating Cybersecurity Metrics.
We created a primary VPC within the final put up on this collection.
Should you tried to deploy an EC2 occasion in that VPC we created you wouldn’t be capable to connect with it utilizing SSH or RDP even when opened the right ports (22 and 3389 respectively and an upcoming subject should you’re not acquainted). That reality is one thing that usually journeys new AWS customers up. That’s why this is likely one of the first subjects I cowl in my AWS cloud safety class and I added that idea to class labs for one more firm.
The explanation you wouldn’t be capable to connect with your VPC is that at present the VPC we deployed within the final put up has no path to the Web. As a way to present a path to and from the Web for sources in our VPC we have to create a route desk with a route pointing to an Web Gateway.
Routes Tables and Routes
With out that route, visitors destined to the Web out of your VPC can’t get there, and something attempting to ship visitors to the IP addresses of sources in your VPC can’t get there both. Routes outline allowed locations between networks. If no route exists to get to a specific vacation spot, the visitors can’t get there.
A route desk is a group of routes. Route tables are usually present in community units that assist your connect with different networks, like while you join from your property community to your ISP. You may be utilizing a community system that has a route desk.
We are able to outline a route desk on AWS utilizing CloudFormation:
I’ve created a separate route desk template as a result of though I’m going to have my subnets use the VPC route desk for now, I forsee needing to override subnet route tables sooner or later. The route desk for the VPC controls the routing for subnets until overridden.
I’m additionally going to provide my route desk identify through tags like we did for our VPC.

Web Gateways
While you strive to hook up with an EC2 occasion in AWS, your community visitors goes to journey on a path on the Web (usually) to get there. Because the packets you ship to your VM traverse this path they may get despatched to varied units that perceive what to do with the packets and ahead them to the following system till lastly they attain your host.
An Web Gateway is a kind of units. If a path to an Web Gateway (IGW) exists in your VPC route desk, the visitors can get to the Web Gateway and it is aware of the best way to deal with packets from the Web and get them to the right endpoint or host in your VPC. While you ship outbound visitors to the Web, the Web gateway is aware of the best way to ahead the visitors to the Web to get it to the right vacation spot. With out one, your Web visitors isn’t attending to your VPC or going wherever out of your VPC.

Route
Lastly, we want a route in our route desk that sends visitors to the Web Gateway if we wish to enable visitors to and from the Web.
Should you take a look at the choices for a route desk you’ll see fairly a number of:

There are lots of alternative ways to limit visitors with route tables. While you’re troubleshooting community connectivity on AWS, don’t overlook to test route tables. Moreover, pay attention to broad entry that may have unintended side-effects. I wish to say, if a path exists, visitors will circulation there.
As soon as on AWS my QA engineer was sending visitors to the manufacturing VPC for some purpose. Once I requested him why he was doing that he was very stunned and stated, “I’m not doing that!” The issue was {that a} route desk will ship visitors the place it might probably and prioritizes by probably the most restrictive route. All issues being equal, the visitors would possibly find yourself going to the fallacious place. Chances are you’ll want a mixture of route tables and visitors guidelines to maintain visitors the place you need it to be. Site visitors guidelines will probably be coated in a later put up.
Explaining all the above choices is past this weblog put up collection for the second. I positively cowl them in courses however we don’t want all these choices for what we’re doing proper now. In a big group, you’d in all probability be establishing some issues in a different way than I’m going to do right here.
Right here’s what we have to create our route:
RouteTableID: Our route desk the place we're going to add the route.
GatewayID: The route vacation spot which is our IGW.
DestinationCidrBlock: 0.0.0.0/0 which specifies we're permitting visitors to any IPv4 deal with on the Web.
Notice that this error message that you just get should you fail to specify both a DestinationCidrBlock or a DestinationIpv6CidrBlock is inaccurate.
Precisely certainly one of DestinationCidrBlock and DestinationIpv6CidrBlock should be specified and never empty.
You may specify solely a DestinationCidrBlock should you don’t wish to enable IPv6 visitors. I like to recommend that you just solely allow IPv6 should you perceive the best way to accurately safe and monitor it as a result of it really works fairly in a different way than IPv4. Massive organizations may have IPv6 most definitely to keep away from IP exhaustion. Smaller organizations could not. The entire purpose IPv6 happened was to beat a restricted variety of IPv4 addresses. In case you are not dealing with that downside and nobody is forcing you to make use of IPv6 you do not want it.
I additionally lately examine how somebody performing a penetration check in a Home windows atmosphere bought area administrator entry utilizing a flaws IPv6 configuration. It was the solely downside he might discover to realize further entry. Each time I put up one thing about the best way to disable or disallow IPv6 on Twitter I get attacked by IPv6 zealots. I’m not saying you shouldn’t use IPv6. I’m saying you must know the best way to safe and monitor it correctly earlier than you do and the best way to rapidly replace units if an IPv6 vulnerability is found because it has been in use a a lot shorter time than IPv4.
VPC Gateway Attachment
Now should you tried to run our CloudFormation template we’ve created up thus far you’ll get the next error:
route desk rtb-xxxxx and community gateway igw-xxxxx belong to totally different networks (Service: AmazonEC2; Standing Code: 400; Error Code: InvalidParameterValue; Request ID: xxxx; Proxy: null)
That’s as a result of in we have to affiliate or “connect” the IGW to the VPC. We are able to try this in CloudFormation utilizing the VPCGatewayAttachment useful resource.
This useful resource permits us to connect various kinds of gateways to a VPC, because the identify suggests, specifically Web gateways an a VPN Gateway, which I’d cowl later if time permits.
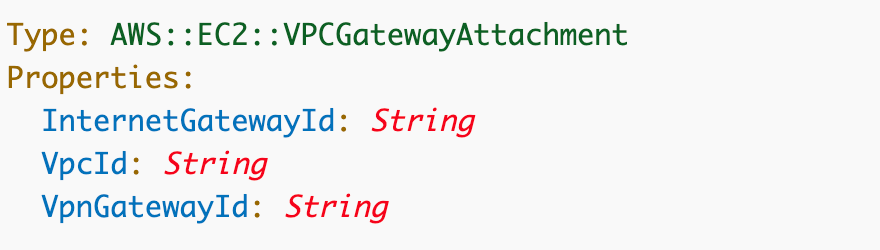
Right here’s what we have to add to our template:

Now there’s one different fascinating factor about these sources. Usually while you use CloudFormation it kinds out all of the dependencies for you and it gained’t deploy a useful resource till all its dependencies are met. Nevertheless, after including the VPC Attachment to my template I bought the identical route desk error. We are able to repair that with the CloudFormation DependsOn attribute:
We merely add a line that signifies that our Route useful resource depends upon our VPCAttachment useful resource:

After making that change the template deploys efficiently.
All the time Test Your Work
So I forgot one thing about route tables and at this level I thought what I did was appropriate however went to double test. Once I went to my VPC and clicked on the route desk there was no route for the Web Gateway. Hmm. Oh yeah. I went to the route tables checklist and My route desk was there, with the right routes, related to the IGW. While you add a route desk with CloudFormation and affiliate it with a VPC it doesn’t add the route desk as the first route desk. This may nonetheless work however now we’ve bought a route desk with no identify in our route desk checklist and that’s sort of annoying. I’ll repair that in a separate put up.
Public and Non-public VPCs and Networking
You might have heard the phrases public VPC, personal VPC, public subnet, or personal subnet prior to now. The truth that a VPC is called a non-public cloud means that you may put restrictions on it so nobody else can entry it however you or your group. It is just opened as much as the Web should you select to configure it that approach.
A public community useful resource is uncovered to the Web.A personal community useful resource will not be.You primarily management whether or not a useful resource is public or personal through the route desk by both giving the community a path to the Web or not.
Modifying our template to create private and non-private VPCs
Our VPC above was created for builders that must entry VMs on AWS from the Web. We additionally want one other kind of VPC for our personal sources on AWS that we don’t need uncovered to the Web. We might merely create a brand new template however then we’re creating further work for ourselves and extra potential bugs. Principally we both deploy the route and IGW if we wish a public VPC and we don’t if we wish a non-public VPC.
As a way to obtain this goal, we will use a CloudFormation situation, to not be confused with IAM Coverage circumstances we mentioned in prior posts.
The way in which we’re going to use a situation in our template:
Go in a parameter that signifies whether or not we're deploying a public or personal VPC. Create a Situation that resolves to IsPublic (true/false)Solely deploy the IGW, VPCAttachment, and Route if we're deploying a public VPC.
Notice that I anticipate extra VPC sorts so I’m not utilizing a real or false parameter which might enable us to skip the situation. I solely wish to enable task of 1 kind so we want one parameter to keep up integrity.

Add a situation that resolves IsPublic to true or false.

Add the situation to the IGW, VPCAttachment, and Route:

Notice that I left the route desk alone so we’ve got route tables related to VPCs with specific names through the tags. Additionally, you may make this template extra versatile should you want utilizing related constructs.
A perform to implement a VPC Naming conference
Subsequent we’re going to create a perform that enforces a constant naming conference. We would like the VPC identify to finish with PublicVPC or PrivateVPC.
Create a brand new network_functions.sh file in the identical folder as deploy.sh and add this perform:
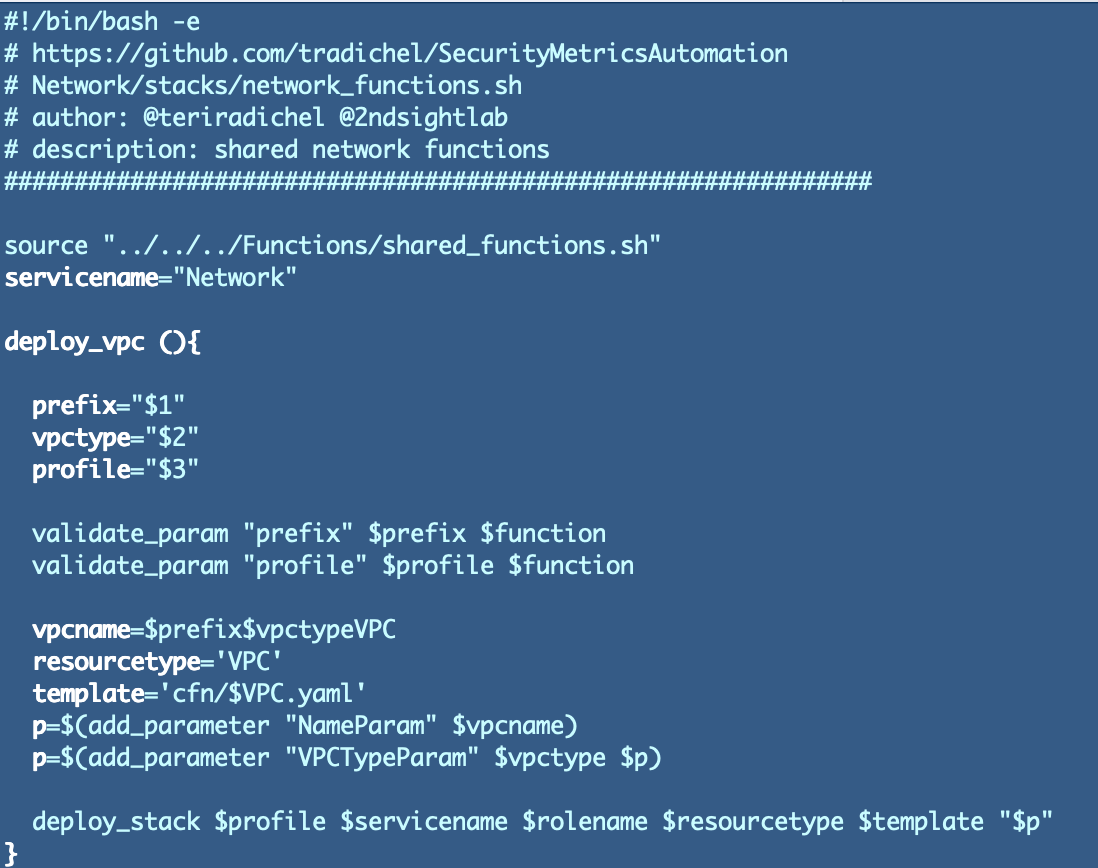
Now use the above to deploy one public and one personal VPC.

Now go to the VPC console and confirm that your two new VPCs exist. Confirm that two new route tables exist. The Distant Entry VPC route desk can have a route for the IGW making and the route desk for the BatchJobs is not going to have an Web route.
Teri Radichel
Should you appreciated this story please clap and observe:
Medium: Teri Radichel or Electronic mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts


