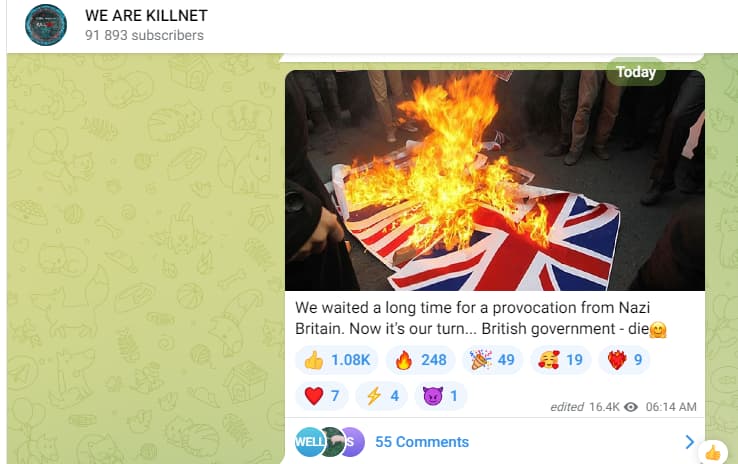
On November twenty second, within the early hours of the morning, Prince William’s web site was reportedly attacked by a Russian hacking group Killnet. In a message posted on Telegram, Killnet said the rationale for the assault to be UK’s continued help for Ukraine.
Killnet stated it had carried out the assault “because of the provide of high-precision missiles to Ukraine.”
Though the web site is now functioning, there are further safety checks on the connection by Cloudflare (the corporate that gives safe net connections) which weren’t current earlier than.
The assault gave the impression to be a distributed denial-of-service assault (DDoS assault) which causes a server to be overwhelmed by quite a few bogus requests, often from bot servers – one thing Killnet is well-known for. Nonetheless, this info has not been confirmed.
Killnet additionally declared in a message on Telegram that “all medical establishments, Authorities providers, and on-line providers” may quickly be attacked as properly. In additional posts, the group stated it was concentrating on the web sites of the London Inventory Trade, the British Military, and the Bankers’ Automated Clearing System (Bacs).
At present, all three web sites are purposeful nonetheless, the British Military web site displayed present process “deliberate upkeep” message on Tuesday, November twenty second.

In a dialog with Hackread.com, Muhammad Yahya Patel, Safety Evangelist at Verify Level Software program stated “Killnet is a prolific political pro-Russian hacking group that strikes targets each few weeks primarily based on geopolitical developments. As a significant participant within the hacktivism area, in addition they recommend and outline the targets for different pro-Russian teams. We’ve got seen a 42% international enhance in cyberattacks because the begin of the Russia-Ukraine battle, with a major rise in state-sponsored teams. These DDoS assaults are the most recent efforts from hacktivists to disrupt high-profile web sites, together with these of the Royal family, as a part of their political agenda.”
DDoS assaults are unlikely to compromise information or techniques as a result of they merely flood the online server with too many requests in order that it can’t reply in time. Throughout the assault, the lack of connection is prone to be short-lived since net operators can establish quite a few IP connections originating from the identical block.
Subsequently, menace actors using this system are unlikely to attain any actual injury as a result of this system is just not very profitable lately and most corporations these days make use of applied sciences to offset such assaults.
This isn’t the primary time Killnet has taken it upon itself to wage a cyber battle because of the ongoing political state of affairs between Ukraine and Russia. Beforehand, they tried to take down the Eurovision music contest. As a result of not being invited, they tried to trigger chaos in Italy (the host nation) however had been thwarted and Ukraine went on to win the competitors.
The group additionally tried to take down the net voting servers all through the ultimate however was unable to interrupt by the “wide selection of safety measures” that Eurovision officers promised. As a substitute, they selected to assault a number of Italian establishments within the semi-final and ultimate in Turin.
Associated Information
- 34 Russian Hacking Teams Stole 50 Million Person Passwords
- New DDoS Malware ‘Chaos’ Hits Linux and Home windows Units
- RapperBot malware targets gaming servers with DDoS assaults
- Anti-Russian OldGremlin Ransomware Gang Launches Linux Malware
- DDoS App Meant to Hit Russia Contaminated Telephones of Ukrainian Activists