The pay-per-install (PPI) malware downloader service often known as PrivateLoader is getting used to distribute a beforehand documented information-stealing malware dubbed RisePro.
Flashpoint noticed the newly recognized stealer on December 13, 2022, after it found “a number of units of logs” exfiltrated utilizing the malware on a bootleg cybercrime market known as Russian Market.
A C++-based malware, RisePro is claimed to share similarities with one other info-stealing malware known as Vidar stealer, itself a fork of a stealer codenamed Arkei that emerged in 2018.
“The looks of the stealer as a payload for a pay-per-install service might point out a menace actor’s confidence within the stealer’s skills,” the menace intelligence firm famous in a write-up final week.
Cybersecurity agency SEKOIA, which launched its personal evaluation of RisePro, additional recognized partial supply code overlaps with PrivateLoader. This encompasses the string scrambling mechanism, HTTP methodology and port setup, and the HTTP message obfuscation methodology.
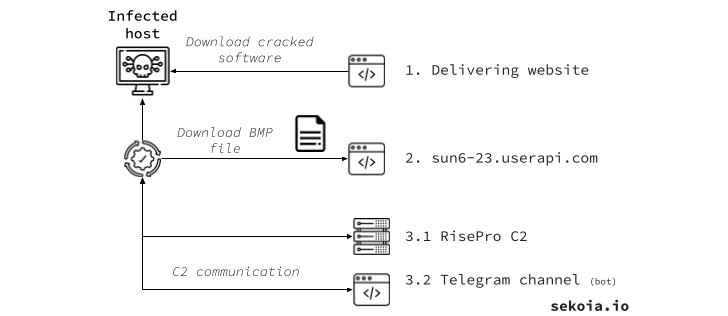
PrivateLoader, because the title signifies, is a obtain service that permits its subscribers to ship malicious payloads to focus on hosts.
It has been used prior to now to ship Vidar Stealer, RedLine Stealer, Amadey, DanaBot, and NetDooka, amongst others, whereas masquerading as pirated software program hosted on decoy websites or compromised WordPress portals that seem prominently on search outcomes.
RisePro isn’t any totally different from different stealers in that it is able to stealing a variety of information from as many as 36 net browsers, together with cookies, passwords, bank cards, crypto wallets, in addition to gathering information of curiosity and loading extra payloads.
It is supplied on the market on Telegram, with the malware’s developer additionally making obtainable a Telegram channel that permits legal actors to work together with contaminated methods by offering a bot ID created by the stealer and despatched to a distant server submit a profitable breach.
Additionally a part of the malware’s infrastructure is an administration panel hosted at a site named my-rise[.]cc that permits entry to stolen knowledge logs, however solely after signing into an account with a sound set of credentials.
It is presently not clear if RisePro is authored by the identical set of menace actors behind PrivateLoader, and if it is completely bundled alongside the PPI service.
“PrivateLoader continues to be lively and comes with a set of recent capabilities,” SEKOIA mentioned. “Similarities between the stealer and PrivateLoader can’t be ignored and gives extra perception into the menace actor growth.”