Containers are thought-about to be a regular method of deploying these microservices to the cloud. Containers are higher than digital machines in nearly all methods besides safety, which can be the primary barrier to their widespread adoption.
This text will present a greater understanding of container safety and out there strategies to safe them.
A Linux container will be outlined as a course of or a set of processes working within the userspace that’s/are remoted from the remainder of the system by totally different kernel instruments.
Containers are nice alternate options to digital machines (VMs). Despite the fact that containers and digital machines present the identical isolation advantages, they differ in the best way that containers present working system virtualization as a substitute of {hardware}. This makes them light-weight, quicker to begin, and consumes much less reminiscence.
As a number of containers share the identical kernel, the answer is much less safe than the VMs, the place they’ve their copies of OS, libraries, devoted sources, and functions. That makes VM excellently safe however due to their excessive storage measurement and diminished efficiency, it creates a limitation on the entire variety of VMs which will be run concurrently on a server. Additional VMs take plenty of time as well.
The introduction of microservice structure has modified the best way of growing software program. Microservices permit the event of software program in small self-contained unbiased companies. This makes the applying simpler to scale and gives agility.
If part of the software program must be rewritten it might simply be executed by altering solely that a part of the code with out interrupting another service, which wasn’t doable with the monolithic kernel.
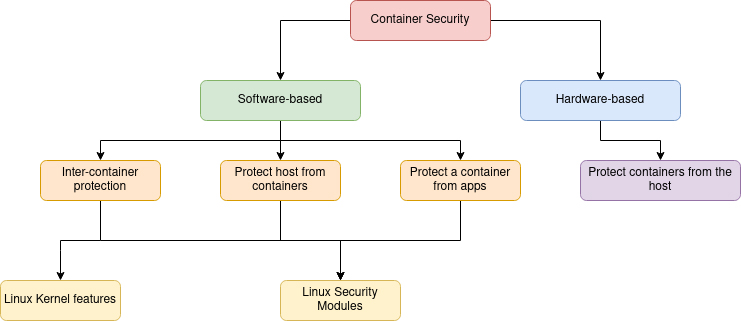
1) Linux Kernel Options
a. Namespaces
Namespaces make sure the isolation of sources for processes working in a container to that of others. They partition the kernel sources for various processes. One set of processes in a separate namespace will see one set of sources whereas one other set of processes will see one other. Processes in several see totally different course of IDs, hostnames, consumer IDs, file names, names for community entry, and a few interprocess communication. Therefore, every file system namespace has its non-public mount desk and root listing.
This isolation will be prolonged to the kid course of working inside a container. For eg., if there’s a PID 1 assigned to a course of in a container, the identical PID 1 may also be assigned to another youngster course of utilizing the PID namespace.
Equally, different namespaces like community, mount, PID, Person, UTS, IPC, and time may very well be utilized to isolate totally different sources in a container.
Nevertheless, one limitation with namespaces is that some sources are nonetheless not namespace-aware. For instance units.
b. Management Teams (CGroups)
They restrict and isolate the useful resource utilization like CPU runtime, reminiscence, disk I/O and community amongst user-defined teams of processes working on a system.
In distinction to namespaces, cgroups restrict what number of sources can be utilized, whereas namespaces management what sources a container can see.
c. Capabilities
Linux implementations distinguish two classes of processes: privileged processes (superuser or root), and unprivileged processes. Privileged processes bypass all kernel permission checks, whereas unprivileged processes are topic to full permission checking based mostly on the method’s credentials.
However within the case of containers, these binary choices will be troublesome as a result of offering the entire container to have full root privilege will be harmful.
Capabilities flip this dichotomy into fine-grained entry management. A set of capabilities will be assigned to the container which might scale back the container’s root operational threats.
d. Safe Computation Mode (Seccomp)
Seccomp can be utilized to limit the actions out there throughout the container. It restricts the method to make some specific predefined syscalls from consumer house to kernel house. If the method makes an attempt another system calls, it’s terminated by the kernel. A lot of syscalls are uncovered to each user-space course of, with a lot of them not required. Proscribing them reduces the entire kernel floor uncovered to the applying.
seccomp-bpf is an extension to seccomp that permits filtering of system calls utilizing a configurable coverage. The mix of restricted and allowed calls are organized in profiles, and totally different profiles will be handed to totally different containers. It gives extra fine-grained management than capabilities, giving an attacker a restricted variety of syscalls from the container throughout a safety compromise.
2) Linux Safety Modules (LSMs)
To grasp the working of LSMs, let’s check out kernel objects.
Kernel Objects
Every kernel object is just a reminiscence block allotted by the kernel. It retains the details about the objects in an information construction which may solely be accessed by the kernel. The system creates and manipulates a number of sorts of kernel objects, these embody entry token objects, occasion objects, file objects, file-mapping objects, I/O completion port objects, job objects, mailslot objects, mutex objects, pipe objects, course of objects, semaphore objects, thread objects, and waitable timer objects.
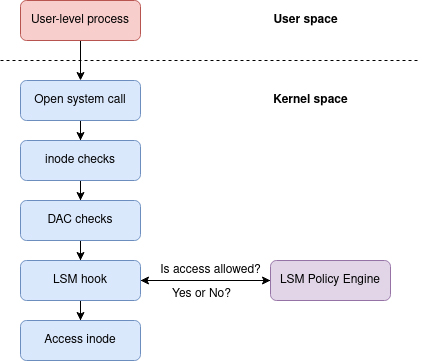
LSMs
LSM interface mediates entry to inside kernel objects by putting hooks within the kernel simply earlier than their entry. It basically solutions the query: “Might <topic> do <motion> to <object>”, for instance: “Might an internet server entry recordsdata in customers’ house directories?”. Forms of objects protected embody recordsdata, inodes, activity buildings, credentials, and interprocess communication objects. Manipulating these objects represents the first method processes work together with their atmosphere, and by rigorously specifying allowable interactions, a safety administrator could make it harder for an attacker to take advantage of a flaw in a single program to pivot to different areas of the system.
Linux Safety Module (LSM) gives MAC-based controls with minimal modifications to the kernel itself. LSM permits modules to mediate entry to kernel objects by putting hooks within the kernel code simply earlier than the entry. The LSM framework gives a mechanism for numerous safety checks to be hooked by new kernel extensions. The identify “module” is a little bit of a misnomer since these extensions are usually not loadable kernel modules however chosen throughout construct time.
Some generally used LSMs are:
SELinux (Safety Enhanced Linux) – is the default MAC implementation on RedHat-based Linux Distributions. It’s recognized for being highly effective and complicated. SELinux is attribute-based which suggests the safety identifiers for recordsdata are saved in prolonged file attributes within the file system. SELinux defines entry controls for the functions, processes, and recordsdata on a system. It makes use of safety insurance policies, that are a algorithm that inform SELinux what can or can’t be accessed, to implement the entry allowed by a coverage.
AppArmor – It implements a task-centered coverage, with activity “profiles” being created and loaded from userspace. Profiles can permit capabilities like community entry and uncooked socket entry. AppArmor safety insurance policies utterly outline what system sources particular person functions can entry, and with what privileges. Duties on the system that would not have a profile outlined run in an unconfined state equal to plain Linux DAC permissions.
There are hardware-based container safety mechanisms that shield the containers from different containers and a malicious or compromised host. This text targeted on the software-based container safety facet.
It was a short introduction to container safety and was primarily associated to Linux containers. If you wish to have a extra detailed look, please comply with the hyperlinks within the reference part.
Reference:
Container Safety: Points, Challenges, and the Highway Forward
LSM Design: Mediate Entry to Kernel Objects

