Bear in mind when malicious actors have been spreading Nerbian RAT via pretend WHO Security emails on COVID-19? Properly, When you imagine that menace actors and scammers have given up on COVID-19-related scams, then you’re flawed as Punisher ransomware is on the market with the assistance of pretend COVID-19 monitoring apps.
New Rip-off on the Block
It’s simply as necessary now to entry dependable sources for COVID-related updates because it was again when the pandemic was at its peak. That’s as a result of researchers at Cyble Analysis and Intelligence Labs (CRIL) have found a brand-new variant of Punisher ransomware that’s being distributed via a bogus COVID-19 tracker app out there on a COVID-19-theme-based web site (covid19digitalhealthconsultingcl).
Assault Evaluation
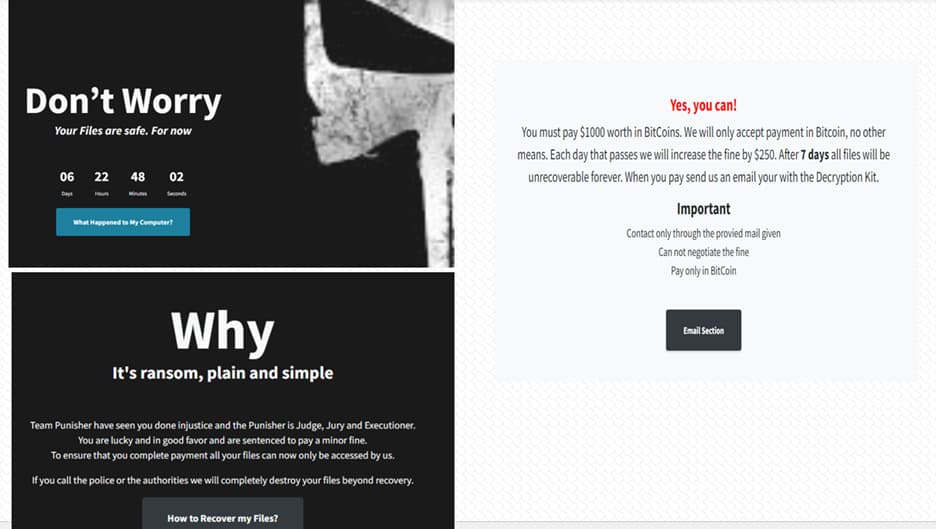
Since this COVID-19 rip-off entails ransomware, the malicious actions begin proper after the malware infiltrates the system. It shortly appends information to ransom notes, together with the victims’ distinctive ID, system ID, BTC handle, an infection date, and JavaScript codes.
After that is completed, the timer is began to make sure the ransom quantity retains growing as time passes. the ransom notice is displayed on the Desktop, Startup, and Begin menus as a shortcut to a file titled “unlock your information.ink.” Punisher encrypts the next information on the focused machine:
- AlertingUser
- RetrieveFiles
- CheckConnection
- GeneratePassword
- GenerateSystemID
- MakeConnection
Who’re the Targets?
The attackers are focusing on people in Chile on this marketing campaign, and for file decryption, they’re demanding $1000 in bitcoin. Researchers imagine the attackers are focusing on people and never firms for this rip-off.
Their evaluation relies on the modus operandi, using Punisher ransomware, and the malware’s use of the AES-128 symmetric algorithm to encrypt information.
The way to Keep Protected?
It’s essential to train warning when accessing or downloading COVID-19-related apps or websites. Desire downloading functions from genuine sources. Furthermore, it’s essential to conduct common backups, allow auto-updates, and set up the very best antivirus options. Additionally, keep away from clicking on attachments in emails from unverified or unknown sources.
When you suspect your machine could also be affected by the ransomware, instantly detach all different gadgets sharing the community and exterior storage (if any), and preserve monitoring the system logs for suspicious actions.
Associated Information
- Classes from COVID-19 Cyberattacks: The place Do We Go Subsequent?
- Feds seize fraud area claiming to supply COVID-19 vaccine
- Pretend govt COVID-19 monitoring app spreads Android ransomware
- Ransomware assault on well being tech agency disrupted COVID-19 trials
- Darkish internet scammers promoting ventilators & MP3 information to kill Coronavirus