Talking of which, Twilio, a significant communications platform that companies Voice over Web Protocol (VoIP) integrations, introduced over the weekend that it was hit by a phishing assault. The risk actors behind the assault had been capable of achieve entry to a few of Twilio’s inside methods and look at buyer knowledge. In accordance with Twilio, the info implicated on this breach is said to a restricted variety of buyer accounts.
The corporate has partnered with an unnamed forensics agency to conduct an investigation into the incident. The investigation remains to be ongoing. Twilio is reaching out to affected prospects to inform them of the info breach and work with them to handle any issues as extra particulars are uncovered within the investigation. Twilio prospects in a roundabout way contacted and notified by the corporate weren’t affected by the breach, as far as the proof revealed by the investigation exhibits.
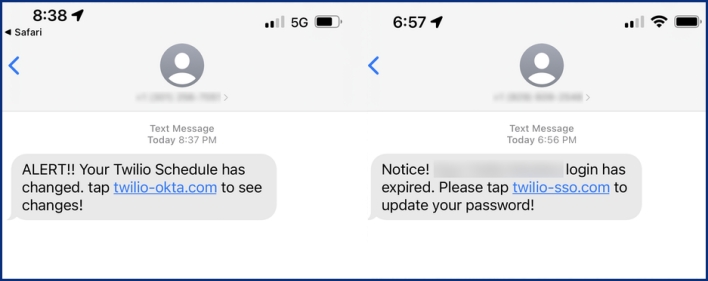
The messages falsely knowledgeable workers of expired passwords, schedule modifications, or different related notices that will require workers to login to view or deal with the trigger for the discover. The messages prompted Twilio workers to open hyperlinks to URLs that contained phrases corresponding to “Twilio,” “SSO” (single sign-on), and “Okta,” which is an identification platform utilized by Twilio. Workers who visited these URLs had been met by a webpage that mimicked Twilio’s sign-in web page.
Evidently, some workers had been duped by this smishing assault and entered their login credentials into the pretend sign-in pages managed by the attackers. The smishing messages had been despatched from cellphone numbers belonging to the US service networks, and Twilio labored with the carriers, in addition to the internet hosting suppliers serving the URLs used within the assault, to close down the malicious marketing campaign. The Twilio Safety Incident Response Group has dedicated to posting extra updates to the Twilio weblog if there are any modifications prospects ought to concentrate on.


