 Recent knowledge on knowledge breach prices from IBM present phishing, enterprise e mail compromise, and stolen credentials are the longest knowledge breaches to determine and include.
Recent knowledge on knowledge breach prices from IBM present phishing, enterprise e mail compromise, and stolen credentials are the longest knowledge breaches to determine and include.
There are tangible repercussions of permitting your group to succumb to an information breach that begins with phishing, social engineering, enterprise e mail compromise, or stolen credentials – based on IBM’s just-released 2022 Value of a Knowledge Breach report. Phishing and social engineering go hand-in-hand, with enterprise e mail compromise and stolen credentials being outcomes of assaults, used as launch factors for additional malicious actions.
In accordance with the IBM report, the typical value of a knowledge breach in 2022 is $4.35 million, with a median of 277 days to determine the breach and include it. That’s really the excellent news. Why you ask? As a result of whenever you issue within the preliminary assault vector, it will get worse.
In accordance with IBM, the next are the typical knowledge breach prices primarily based on the preliminary assault vector:
- Phishing – $4.91 million
- Enterprise Electronic mail Compromise – $4.89 million
- Stolen Credentials – $4.50 million
- Social Engineering – $4.10 million
Why a lot? Plenty of it has to do with how lengthy menace actors act undetected as they transfer laterally inside your setting, acquire entry to credentials and knowledge, and exfiltrate your beneficial knowledge.
In accordance with the report, the longest instances revolve round assaults that contain your customers:
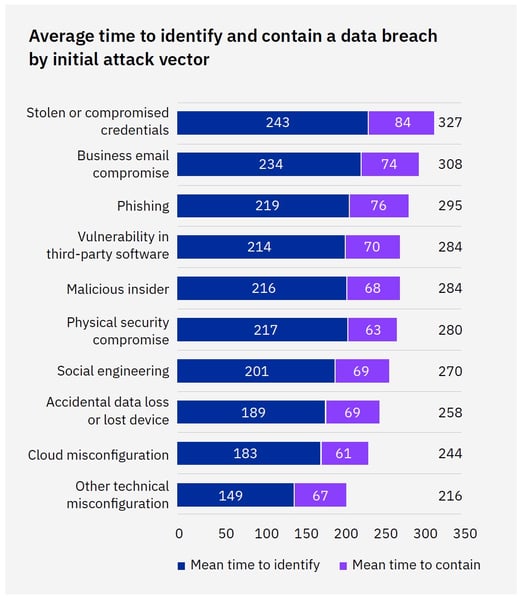
Supply: IBM
With the typical variety of days to detection and containment is 277, it’s evident that stolen credentials, phishing, and enterprise e mail compromise (the assault vectors your customers play a job in!) push these “rookie numbers” up, giving attackers an extra 1-2 month’s time to proceed their malicious actions.
We already know that phishing and BEC assaults deal with both stealing credentials or infecting endpoints, placing the person receiving the malicious e mail, cellphone name, textual content, and so on. squarely in the course of the dialogue that ends in these large knowledge breach prices. Customers must play a job in your safety technique to assist mitigate the danger of profitable assaults by means of continuous Safety Consciousness Coaching that teaches them find out how to determine suspicious content material in e mail and on the internet, serving to to keep away from any interplay that will end in a knowledge breach.


