Safety researchers have shared particulars a few now-addressed safety flaw in Apple’s macOS working system that might be probably exploited to run malicious functions in a fashion that may bypass Apple’s safety measures.
The vulnerability, tracked as CVE-2022-32910, is rooted within the built-in Archive Utility and “may result in the execution of an unsigned and unnotarized software with out displaying safety prompts to the person, by utilizing a specifically crafted archive,” Apple gadget administration agency Jamf mentioned in an evaluation.
Following accountable disclosure on Could 31, 2022, Apple addressed the problem as a part of macOS Massive Sur 11.6.8 and Monterey 12.5 launched on July 20, 2022. The tech big, for its half, additionally revised the earlier-issued advisories as of October 4 so as to add an entry for the flaw.
Apple described the bug as a logic subject that might enable an archive file to get round Gatekeeper checks, which is designed in order to make sure that solely trusted software program runs on the working system.
The safety know-how achieves this by verifying that the downloaded package deal is from a professional developer and has been notarized by Apple – i.e., given a stamp of approval to make sure it isn’t been maliciously tampered with.
“Gatekeeper additionally requests person approval earlier than opening downloaded software program for the primary time to ensure the person hasn’t been tricked into operating executable code they believed to easily be a knowledge file,” Apple notes in its help documentation.
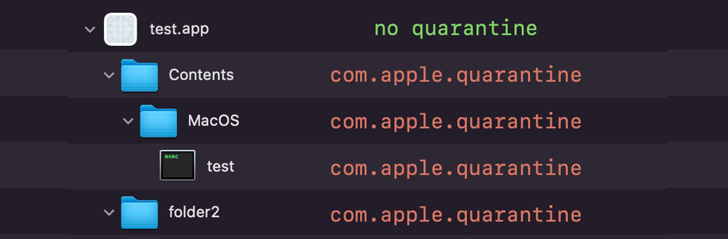
It is also value noting archive recordsdata downloaded from the web are tagged with the “com.apple.quarantine” prolonged attribute, together with the objects inside the file, in order to set off a Gatekeeper verify previous to execution.
However in a peculiar quirk found by Jamf, the Archive Utility fails so as to add the quarantine attribute to a folder “when extracting an archive containing two or extra recordsdata or folders in its root listing.”
Thus by creating an archive file with the extension “exploit.app.zip,” it results in a state of affairs the place an unarchival ends in the creation of a folder titled “exploit.app,” whereas additionally missing the quarantine attribute.
This software “will bypass all Gatekeeper checks permitting an unnotarized and/or unsigned binary to execute,” Jamf researcher Ferdous Saljooki, who found the flaw, mentioned. Apple mentioned it resolved the vulnerability with improved checks.
The findings come greater than six months after Apple addressed one other related flaw in macOS Catalina, Massive Sur 11.6.5, and Monterey 12.3 (CVE-2022-22616) that might enable a malicious ZIP archive to bypass Gatekeeper checks.