Cryptocurrency corporations are being focused as a part of a brand new marketing campaign that delivers a distant entry trojan referred to as Parallax RAT.
The malware “makes use of injection methods to cover inside authentic processes, making it troublesome to detect,” Uptycs stated in a brand new report. “As soon as it has been efficiently injected, attackers can work together with their sufferer through Home windows Notepad that probably serves as a communication channel.”
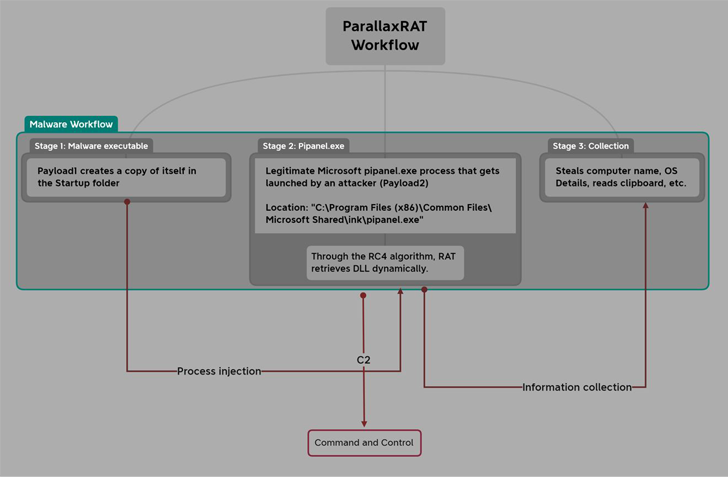
Parallax RAT grants attackers distant entry to sufferer machines. It comes with options to add and obtain information in addition to file keystrokes and display screen captures.
It has been put to make use of since early 2020 and was beforehand delivered through COVID-19-themed lures. In February 2022, Proofpoint detailed a cybercrime risk actor dubbed TA2541 focusing on aviation, aerospace, transportation, manufacturing, and protection industries utilizing completely different RATs, together with Parallax.
The primary payload is a Visible C++ malware that employs the course of hollowing method to inject Parallax RAT right into a authentic Home windows part referred to as pipanel.exe.
Parallax RAT, apart from gathering system metadata, can be able to accessing knowledge saved within the clipboard and even remotely rebooting or shutting down the compromised machine.
One notable side of the assaults is the usage of the Notepad utility to provoke conversations with the victims and instructing them to connect with an actor-controlled Telegram channel.
Uptycs’ evaluation of the Telegram chat reveals that the risk actor has an curiosity in crypto corporations corresponding to funding companies, exchanges, and pockets service suppliers.
The modus operandi entails looking public sources like DNSdumpster for figuring out mail servers belonging to the focused corporations through their mail exchanger (MX) information and sending phishing emails bearing the Parallax RAT malware.
The event comes as Telegram is more and more changing into a hub for prison actions, enabling risk actors to prepare their operations, distribute malware, and facilitate the sale of stolen knowledge, and different unlawful items partially owing to the platform’s lax moderation efforts.
“One cause why Telegram is enticing to cybercriminals is its alleged built-in encryption and the power to create channels and huge, non-public teams,” KELA disclosed in an exhaustive evaluation printed final month.
“These options make it troublesome for regulation enforcement and safety researchers to observe and monitor prison exercise on the platform. As well as, cybercriminals typically use coded language and different spellings to speak on Telegram, making it much more difficult to decipher their conversations.”