A malicious marketing campaign leveraged seemingly innocuous Android dropper apps on the Google Play Retailer to compromise customers’ gadgets with banking malware.
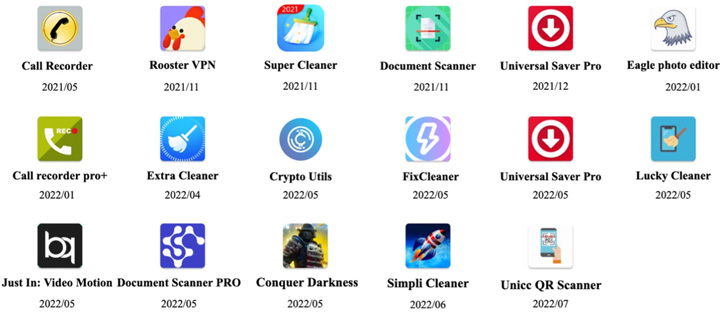
These 17 dropper apps, collectively dubbed DawDropper by Development Micro, masqueraded as productiveness and utility apps equivalent to doc scanners, QR code readers, VPN companies, and name recorders, amongst others. All these apps in query have been faraway from the app market.
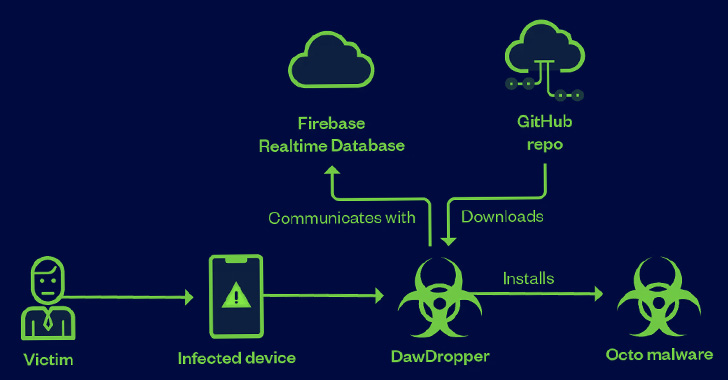
“DawDropper makes use of Firebase Realtime Database, a third-party cloud service, to evade detection and dynamically acquire a payload obtain tackle,” the researchers mentioned. “It additionally hosts malicious payloads on GitHub.”
Droppers are apps designed to sneak previous Google’s Play Retailer safety checks, following which they’re used to obtain stronger and intrusive malware on a tool, on this case, Octo (Coper), Hydra, Ermac, and TeaBot.
Assault chains concerned the DawDropper malware establishing connections with a Firebase Realtime Database to obtain the GitHub URL essential to obtain the malicious APK file.
The checklist of malicious apps beforehand obtainable from the app retailer is under –
- Name Recorder APK (com.caduta.aisevsk)
- Rooster VPN (com.vpntool.androidweb)
- Tremendous Cleaner- hyper & good (com.j2ca.callrecorder)
- Doc Scanner – PDF Creator (com.codeword.docscann)
- Common Saver Professional (com.virtualapps.universalsaver)
- Eagle photograph editor (com.techmediapro.photoediting)
- Name recorder professional+ (com.chestudio.callrecorder)
- Further Cleaner (com.casualplay.leadbro)
- Crypto Utils (com.utilsmycrypto.mainer)
- FixCleaner (com.cleaner.fixgate)
- Simply In: Video Movement (com.olivia.openpuremind)
- com.myunique.sequencestore
- com.flowmysequto.yamer
- com.qaz.universalsaver
- Fortunate Cleaner (com.luckyg.cleaner)
- Simpli Cleaner (com.scando.qukscanner)
- Unicc QR Scanner (com.qrdscannerratedx)
Included among the many droppers is an app named “Unicc QR Scanner” that was beforehand flagged by Zscaler earlier this month as distributing the Coper banking trojan, a variant of the Exobot cell malware.
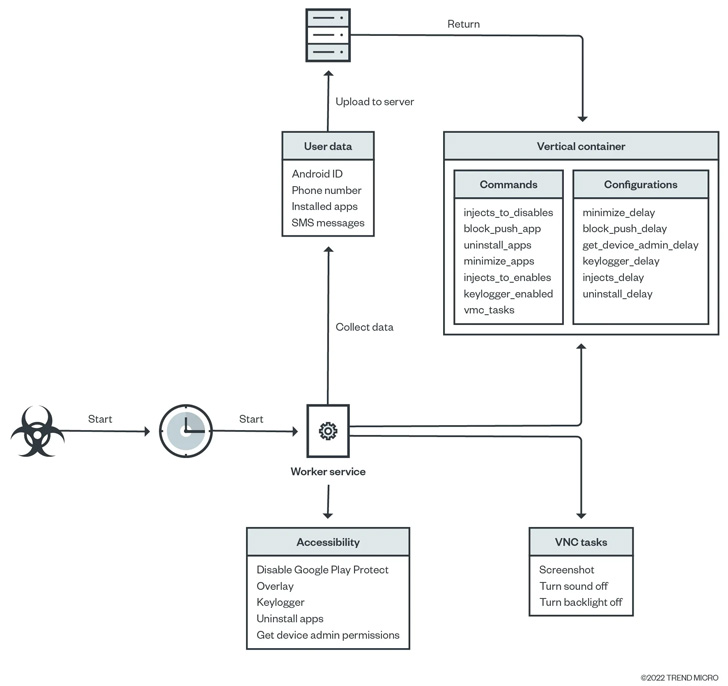
Octo can also be identified to disable Google Play Defend and use digital community computing (VNC) to report a sufferer system’s display screen, together with delicate data equivalent to banking credentials, e mail addresses and passwords, and PINs, all of that are subsequently exfiltrated to a distant server.
Banking droppers, for his or her half, have advanced for the reason that begin of the yr, pivoting away from hard-coded payload obtain addresses to utilizing an middleman to hide the tackle internet hosting the malware.
“Cybercriminals are always discovering methods to evade detection and infect as many gadgets as doable,” the researchers mentioned.
“Moreover, as a result of there’s a excessive demand for novel methods to distribute cell malware, a number of malicious actors declare that their droppers may assist different cybercriminals disseminate their malware on Google Play Retailer, leading to a dropper-as-a-service (DaaS) mannequin.”