Researchers have discovered greater than 50 completely different safety vulnerabilities affecting a whole lot of commercial units. Recognized as OT:ICEFALL, these vulnerabilities primarily exist in operational know-how (OT) industrial units from 10 completely different distributors. Therefore, industries utilizing susceptible OT units should apply mitigation methods to keep away from potential exploits.
About OT:ICEFALL Vulnerabilities Threatening Industrial Gadgets
In response to a latest report from Forescout Vedere Labs, quite a few operational units from the next ten distributors are riddled with OT:ICEFALL vulnerabilities. The researchers named the failings “Icefall” after the second cease on Everest after Base Camp.
Relating to the susceptible units and distributors, the researchers have shared the next record. It mentions solely 9 distributors, because the tenth vendor uncovered to 4 vulnerabilities remains to be underneath disclosure.
- Bently Nevada: 3700, TDI gear (situation displays)
- Emerson: DeltaV and Ovation (distributed management system), OpenBSI (engineering workstation), ControlWave, BB 33xx, ROC (distant terminal unit), Fanuc, PACsystems (programmable logic controller)
- Honeywell: Development IQ (constructing controller), Security Supervisor FSC (security instrumented system), Experion LX (distributed management system), ControlEdge (distant terminal unit), Saia Burgess PCD (programmable logic controller)
- JTEKT: Toyopuc (programmable logic controller)
- Motorola: MOSCAD, ACE IP gateway (distant terminal unit), MDLC (protocol), ACE1000 (distant terminal unit), MOSCAD Toolbox STS (engineering workstation)
- Omron: SYSMAC Cx collection, Nx collection (programmable logic controller)
- Phoenix Contact: ProConOS (logic runtime)
- Siemens: WinCC OA (SCADA)
- Yokogawa: STARDOM (programmable logic controller)
The researchers have shared an in depth technical report sharing their evaluation. Briefly, they found 56 completely different vulnerabilities that predominantly fall into the next classes.
- Distant code execution
- Denial of service (DoS)
- File/firmware/configuration manipulation
- Authentication bypass
- Compromise of credentials
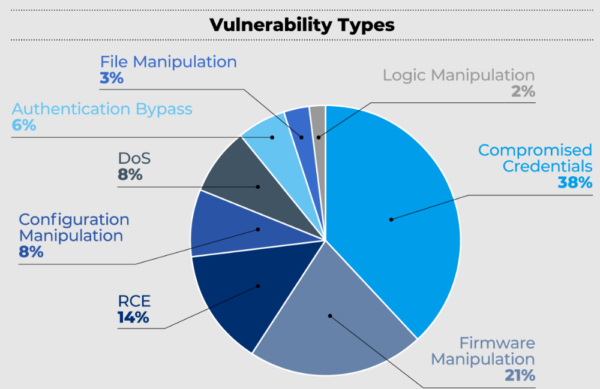
Supply: Forescout
These “insecure-by-design” vulnerabilities demand utmost consideration because the felony hackers are all the time trying to find such bugs to compromise industries by way of malware, reminiscent of TRITON, Industroyer2, and others. As said of their put up,
Abusing a lot of these insecure-by-design, native capabilities of OT gear is the popular modus operandi of real-world industrial management system (ICS)… These vulnerabilities, and the confirmed want for attackers to use them, reveal the necessity for sturdy, OT-aware community monitoring and deep-packet-inspection (DPI) capabilities.
Really useful Mitigations
The susceptible units have an effect on the commercial management techniques globally. Therefore, industries should scan their infrastructure to detect the existence of susceptible gear and patch the bugs. Some mitigation methods that researchers advocate embody,
- Uncover and stock susceptible units
- Implement segmentation controls and correct community hygiene
- Monitor progressive patches launched by affected gadget distributors
- Monitor all community site visitors for malicious packets
Furthermore, the researchers additionally spotlight the numerous downside of certifying insecure-by-design merchandise that may impart a false sense of innate safety. Thus, companies should attempt their finest to obtain secure-by-design merchandise. On the identical time, distributors ought to enter most efforts towards product safety. Collectively, all entities should work in direction of creating an surroundings specializing in “sturdy” as a substitute of “merely purposeful” safety controls.


