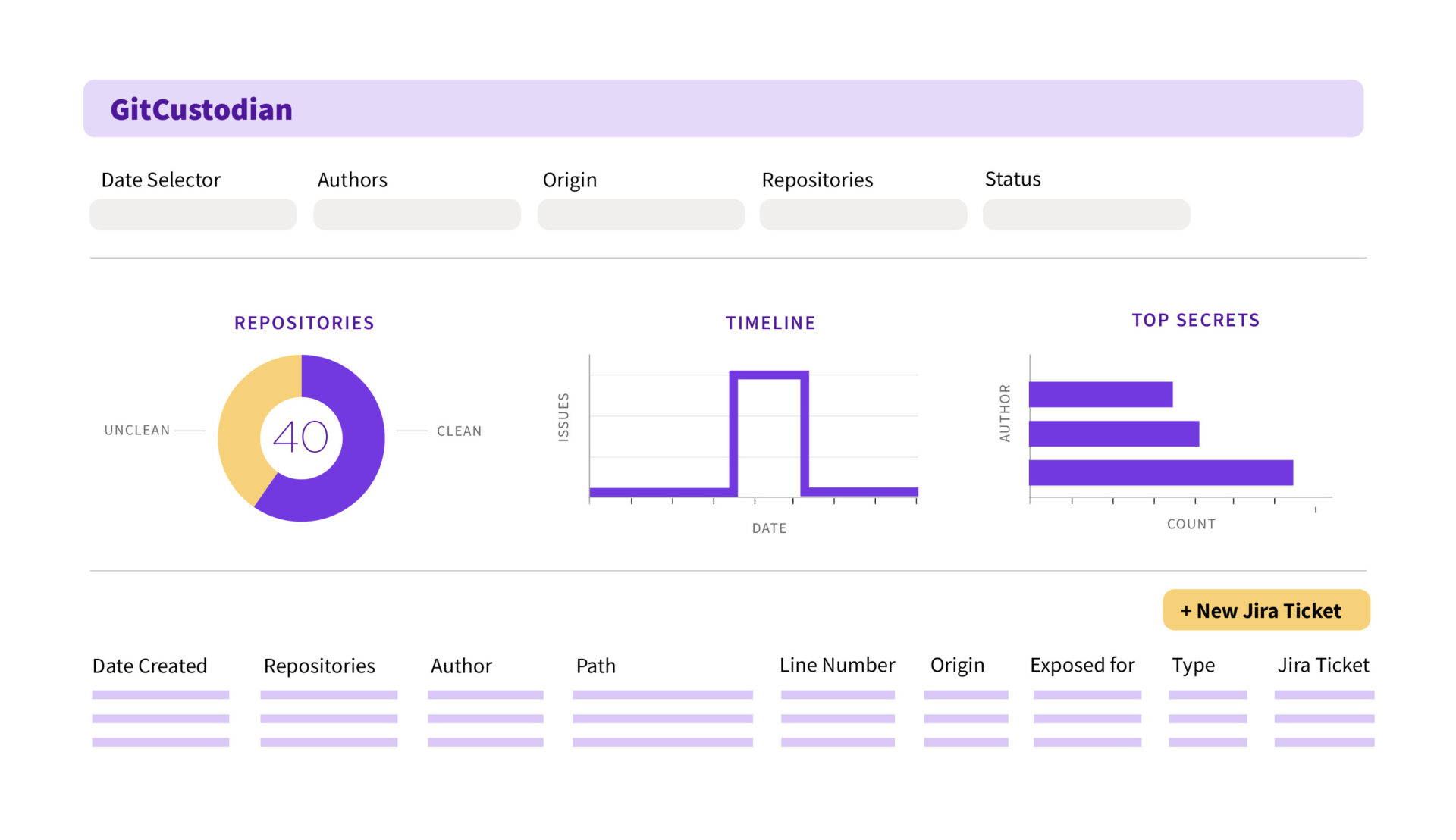
The staff at Opsera, the Steady Orchestration platform for DevOps, at present introduced the discharge of Opsera GitCustodian. This new resolution is meant to alert safety and DevOps groups of susceptible knowledge present in supply code repositories in order that they will forestall vulnerabilities from making it to manufacturing.
GitCustodian additionally works to automate the remediation course of for any uncovered secrets and techniques or different delicate artifacts as soon as vulnerabilities are detected.
“Supply code vulnerabilities have the potential to price organizations a whole lot of hundreds of thousands and even billions of {dollars} a yr attributable to breaches from cyberattackers. That is the place Opsera GitCustodian is available in,” stated Gilbert Martin, VP of buyer success and options at Opsera. “It scans and alerts safety groups of susceptible secrets and techniques lurking in supply code repositories earlier than it’s too late. These groups at the moment are empowered to proactively implement safe software program growth lifecycle greatest practices via orchestrated secrets and techniques governance making supply code vulnerabilities a factor of the previous.”
Key highlights of this launch embrace:
- Extremely correct and complete secrets and techniques safety detection as a way to uncover a big selection of secrets and techniques and different delicate knowledge in supply code
- The flexibility to scan current supply code repositories and acquire a centralized snapshot of any susceptible secrets and techniques throughout imaginative and prescient management programs
- The addition of proactive secrets and techniques governance into current CI/CD workflows to assist the consumer go from detection to remediation to verification with built-in alerting and trouble-ticketing for full incident lifecycle administration
- The flexibility to securely retailer secrets and techniques and keys with a built-in vault that works to eradicate the friction of following secrets and techniques administration greatest practices
- Collaboration enablement that notifies impacted groups to take motion with out altering how or the place they work
- Full insights and analytics to supply customers a full image of the well being and safety of all the lifecycle with actionable insights and compliance reporting.
“The complexity of recent purposes brings with it a number of challenges round managing dependencies and configuration data, safety tokens, username/passwords and different secrets and techniques,” stated Jon Collins, VP of analysis and lead analyst at GigaOM, a know-how analysis firm. “It’s an excessive amount of to anticipate builders to maintain on high of all of the potential points, equivalent to inadvertently lacking a .gitignore file and publishing confidential data into Git. In addition to CI/CD automation, enterprises additionally have to undertake instruments that may scan software program code and dependencies proactively, and in addition forestall the unintended leakage of delicate knowledge.”