Firms which have an open supply software program (OSS) safety coverage in place are likely to carry out a lot better in self-assessed measures of readiness. In addition they are likely to have devoted groups in control of driving software program safety, based on a survey revealed on June 21.
The survey — revealed by software-security agency Snyk and the Linux Basis on Tuesday — discovered that seven out of 10 firms which have an OSS safety coverage in place think about their software growth to be extremely or considerably safe. Comparatively, simply 45% of firms that did not institute such a coverage think about themselves at the very least considerably safe.
Open supply software program has important advantages for software growth, however firms even have to acknowledge and put together for the downsides, says Matt Jarvis, director of developer relations for Snyk.
“Whereas open supply is a confirmed mechanism for innovation and constructing high-quality software program, it is changing into considerably a sufferer of its personal success in that its ubiquity has made it a goal for supply-chain assaults,” he says. “Firms have to construct a stronger understanding of each the mechanisms by which open supply works, and this contains governance in addition to code, and strengthen their strategy to provide chain administration by adopting developer-first safety tooling and methodologies.”
Smaller Corporations Lag in OSS Insurance policies
Total, solely about half of companies have an open supply safety coverage in place to information builders in the usage of elements and frameworks, with a higher variety of small firms, 60%, both having no insurance policies or not understanding whether or not they have one, based on the report.
The economics of safety tends to cut back the precedence of making a proper coverage for startups and smaller companies, the report states.
“Small organizations have small IT staffs and budgets, and the useful wants of the enterprise usually take priority in order that the enterprise can stay aggressive,” the report states. “Lack of sources and time have been the main the explanation why organizations weren’t addressing OSS safety greatest practices.”
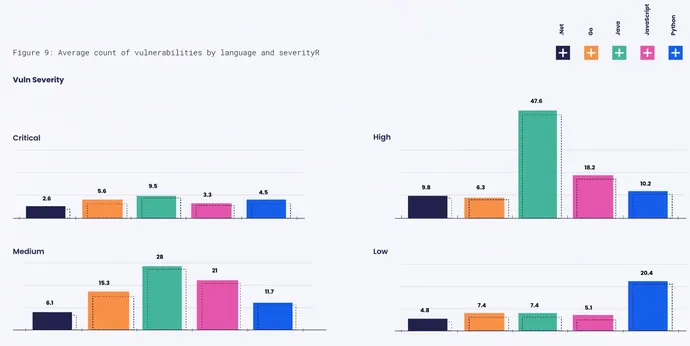
Totally different programming languages additionally introduced totally different safety concerns, based on the research. Purposes written in .NET, for instance, had the longest common time to repair flaws at 148 days, adopted by JavaScript, In the meantime, these written in Go had the speediest time-to-patch, and have been sometimes fastened in a 3rd of that point, or 49 days.
JavaScript Dependencies Abound
JavaScript software have essentially the most dependencies — a median of 174 per mission, based on Snyk — or about seven instances the language with the fewest dependencies, Python, which averages 25 per mission.
Whereas giant transitive dependency timber may end up in circuitous paths to repair vulnerabilities, having numerous dependencies will not be essentially an obstacle, if a company has methods to trace the relationships between initiatives, says Jarvis.
“JavaScript packages are likely to have a smaller scope than different ecosystems, so while there are extra of them, there could also be much less code to audit for potential weaknesses,” he says. “Crucial difficulty is to know the dependencies which you might be utilizing, significantly the transitive ones introduced in as dependencies of dependencies, and that comes all the way down to utilizing the suitable safety tooling to scan issues.”
Nonetheless, the information additionally reveals that totally different languages tended to have totally different severities of flaws. The common mission written in Java, for instance, had greater than 47 high-severity vulnerabilities and 28 medium-severity vulnerabilities, a lot greater than the second-ranked JavaScript, which had a median of 18 and 21 vulnerabilities, respectively. Nonetheless, Python had essentially the most low-severity vulnerabilities, a median of 20 per mission.
“There are a variety of elements at play within the information — the complexity of initiatives, the variety of builders, and the recognition will all have an effect on the quantity and forms of vulnerabilities,” Jarvis says. “Many developer eyes on initiatives which are extraordinarily in style are prone to floor extra bugs.”
Automation = Safety Maturity
Regardless of the significance of figuring out vulnerabilities in dependencies, most security-mature firms — these with OSS safety insurance policies — depend on business vulnerability advisories (60%), automated monitoring of packages for bugs (60%), and notifications from bundle maintainers (49%), based on the survey.
Automated monitoring represents essentially the most important hole between security-mature companies and people companies with no coverage, with solely 38% of firms that wouldn’t have a coverage utilizing some type of automated monitoring, in contrast with the 60% of mature companies.
Firms ought to add an OSS safety coverage if they do not have one, as a strategy to harden their growth safety, says Snyk’s Jarvis. Even a light-weight coverage is an efficient begin, he says.
“There’s a correlation between having a coverage and the sentiment of stating that growth is considerably safe,” he says. “We expect having a coverage in place is an affordable start line for safety maturity, because it signifies the group is conscious of the potential points and has began that journey.”


