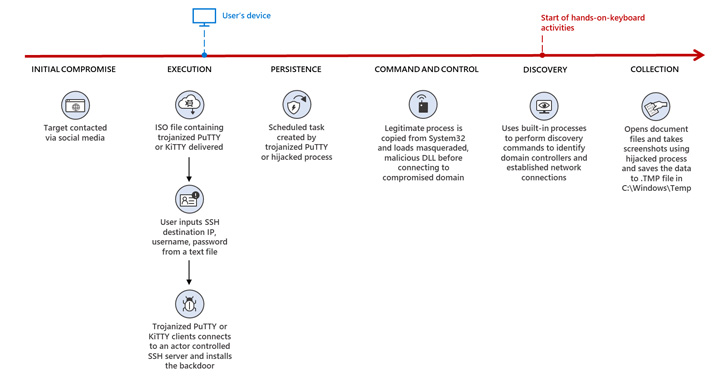
A “extremely operational, harmful, and complicated nation-state exercise group” with ties to North Korea has been weaponizing open supply software program of their social engineering campaigns aimed toward corporations all over the world since June 2022.
Microsoft’s risk intelligence groups, alongside LinkedIn Risk Prevention and Protection, attributed the intrusions with excessive confidence to Zinc, which can also be tracked below the names Labyrinth Chollima.
Assaults focused staff in organizations throughout a number of industries, together with media, protection and aerospace, and IT companies within the U.S., the U.Okay., India, and Russia.
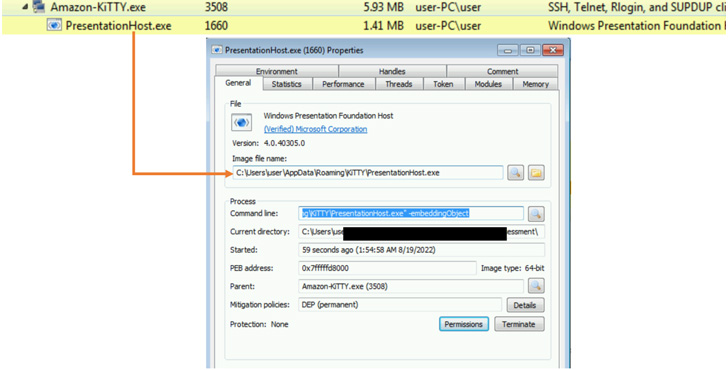
The tech big stated it noticed Zinc leveraging a “wide selection of open-source software program together with PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and muPDF/Subliminal Recording software program installer for these assaults.”
In accordance with CrowdStrike, Zinc “has been lively since 2009 in operations aimed toward amassing political, navy, and financial intelligence on North Korea’s international adversaries and conducting foreign money era campaigns.”
The newest findings dovetail with a latest report from Google-owned Mandiant, which uncovered the adversary’s use of PuTTY through fraudulent job lures shared with potential targets on LinkedIn as a part of a marketing campaign dubbed Operation Dream Job.
This entails establishing preliminary connections with people by posing as recruitment professionals as a trust-building train, earlier than transferring the dialog to WhatsApp, the place a tailor-made lure doc or seemingly benign software program is shared, successfully activating the an infection sequence.
A profitable compromise is adopted by the risk actor transferring laterally throughout the community and exfiltrating collected info of curiosity by deploying a backdoor known as ZetaNile (aka BLINDINGCAN OR AIRDRY).
However in a bid to evade safety defenses and keep away from elevating crimson flags, the implant is downloaded solely when the sufferer makes use of the SSH purchasers to hook up with a specific IP tackle by way of the credentials laid out in a separate textual content file.
Likewise, assaults using the trojanized model of TightVNC Viewer are configured to put in the backdoor solely when the person selects a specific distant host from the choices supplied.
“Zinc assaults look like motivated by conventional cyberespionage, theft of non-public and company information, monetary acquire, and company community destruction,” the corporate stated.
“Zinc assaults bear many hallmarks of state-sponsored actions, equivalent to heightened operational safety, subtle malware that evolves over time, and politically motivated focusing on.”