An rising risk cluster originating from North Korea has been linked to growing and utilizing ransomware in cyberattacks focusing on small companies since September 2021.
The group, which calls itself H0lyGh0st after the ransomware payload of the identical title, is being tracked by the Microsoft Risk Intelligence Heart underneath the moniker DEV-0530, a designation assigned for unknown, rising, or a growing group of risk exercise.
Focused entities primarily embrace small-to-midsize companies equivalent to manufacturing organizations, banks, faculties, and occasion and assembly planning firms.
“Together with their H0lyGh0st payload, DEV-0530 maintains an .onion website that the group makes use of to work together with their victims,” the researchers stated in a Thursday evaluation.
“The group’s normal methodology is to encrypt all information on the goal system and use the file extension .h0lyenc, ship the sufferer a pattern of the information as proof, after which demand fee in Bitcoin in alternate for restoring entry to the information.”
Ransom quantities demanded by DEV-0530 vary anyplace between 1.2 and 5 bitcoins, though an evaluation of the attacker’s cryptocurrency pockets reveals no profitable ransom funds from its victims as of early July 2022.
DEV-0530 is believed to have connections with one other North Korean-based group often known as Plutonium (aka DarkSeoul or Andariel), a sub-group working underneath the Lazarus umbrella (aka Zinc or Hidden Cobra).
The illicit scheme adopted by the risk actor can also be recognized to take a leaf from the ransomware panorama, leveraging extortion ways to use stress on victims into paying up or danger getting their data printed on social media.
DEV-0530’s darkish net portal claims it goals to “shut the hole between the wealthy and poor” and “assist the poor and ravenous folks,” in a tactic that mirrors one other ransomware household known as GoodWill that compels victims into donating to social causes and offering monetary help to folks in want.
The technical breadcrumbs that tie the group to Andariel stem from overlaps within the infrastructure set in addition to based mostly on communications between e-mail accounts managed by the 2 attacker collectives, with DEV-0530 exercise persistently noticed throughout Korea Customary Time (UTC+09:00).
“Regardless of these similarities, variations in operational tempo, focusing on, and tradecraft recommend DEV-0530 and Plutonium are distinct teams,” the researchers identified.
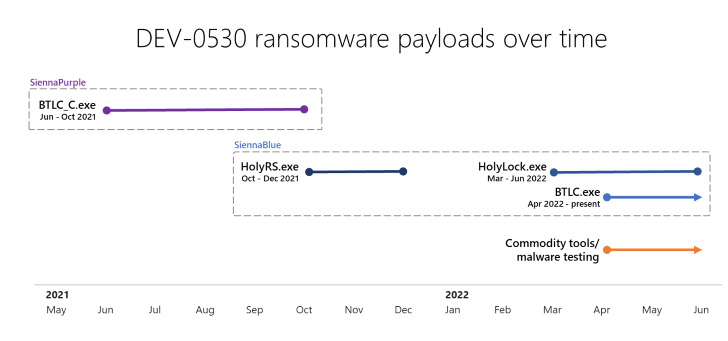
In an indication that implies energetic growth, 4 totally different variants of the H0lyGh0st ransomware had been churned out between June 2021 and Might 2022 to focus on Home windows techniques: BTLC_C.exe, HolyRS.exe, HolyLock.exe, and BLTC.exe.
Whereas BTLC_C.exe (dubbed SiennaPurple) is written in C++, the opposite three variations (codenamed SiennaBlue) are programmed in Go, suggesting an try on the a part of the adversary to develop cross-platform malware.
The newer strains additionally include enhancements to their core performance, together with string obfuscation and talents to delete scheduled duties and take away themselves from the contaminated machines.
The intrusions are stated to have been facilitated by means of the exploitation of unpatched vulnerabilities in public-facing net functions and content material administration techniques (e.g., CVE-2022-26352), leveraging the acquisition to drop the ransomware payloads and exfiltrate delicate information previous to encrypting the information.
The findings come per week after the U.S. cybersecurity, and intelligence businesses warned about using Maui ransomware by North Korean government-backed hackers to focus on the healthcare sector since not less than Might 2021.
The enlargement from monetary heists to ransomware is being considered as yet one more tactic sponsored by the North Korean authorities to offset losses from sanctions, pure disasters, and different financial setbacks.
However given the slim set of victims than is usually related to state-sponsored exercise towards cryptocurrency organizations, Microsoft theorized the assaults might be a side-hustle for the risk actors concerned.
“It’s equally attainable that the North Korean authorities just isn’t enabling or supporting these ransomware assaults,” the researchers stated. “People with ties to Plutonium infrastructure and instruments might be moonlighting for private achieve. This moonlighting concept would possibly clarify the often-random choice of victims focused by DEV-0530.”
The ransomware risk evolves in a post-Conti world
The event additionally comes because the ransomware panorama is evolving with current and new ransomware teams, particularly LockBit, Hive, Lilith, RedAlert (aka N13V), and 0mega, even because the Conti gang formally shuttered its operations in response to a large leak of its inner chats.
Including gas to the hearth, LockBit’s improved successor additionally comes with a model new information leak website that permits any actor to buy information stolen from victims, to not point out incorporating a search characteristic that makes it simpler to floor delicate data.
Different ransomware households have additionally added related capabilities in an try to create searchable databases of data stolen throughout assaults. Notable amongst this checklist are PYSA, BlackCat (aka ALPHV), and the Conti offshoot often known as Karakurt, in accordance with a report from Bleeping Laptop.
Based mostly on statistics gathered by Digital Shadows, 705 organizations had been named in ransomware information leak web sites within the second quarter of 2022, marking a 21.1% enhance from Q1 2022. The highest ransomware households through the interval included LockBit, Conti, BlackCat, Black Basta, and Vice Society.