The North Korea-linked ScarCruft group has been attributed to a beforehand undocumented backdoor referred to as Dolphin that the risk actor has used towards targets situated in its southern counterpart.
“The backdoor […] has a variety of spying capabilities, together with monitoring drives and moveable units and exfiltrating information of curiosity, keylogging and taking screenshots, and stealing credentials from browsers,” ESET researcher Filip Jurčacko stated in a brand new report revealed immediately.
Dolphin is alleged to be selectively deployed, with the malware utilizing cloud companies like Google Drive for knowledge exfiltration in addition to command-and-control.
The Slovak cybersecurity firm stated it discovered the implant deployed as a final-stage payload as a part of a watering gap assault in early 2021 directed towards a South Korean digital newspaper.
The marketing campaign, first uncovered by Kaspersky and Volexity final 12 months, entailed the weaponization of two Web Explorer flaws (CVE-2020-1380 and CVE-2021-26411) to drop a backdoor named BLUELIGHT.
ScarCruft, additionally referred to as APT37, InkySquid, Reaper, and Ricochet Chollima, is a geo-political motivated APT group that has a observe document of attacking authorities entities, diplomats, and information organizations related to North Korean affairs. It has been recognized to be energetic since a minimum of 2012.
Earlier this April, cybersecurity agency Stairwell disclosed particulars of a spear-phishing assault focusing on journalists protecting the nation with the last word purpose of deploying a malware dubbed GOLDBACKDOOR that shares overlaps with one other ScarCruft backdoor named BLUELIGHT.
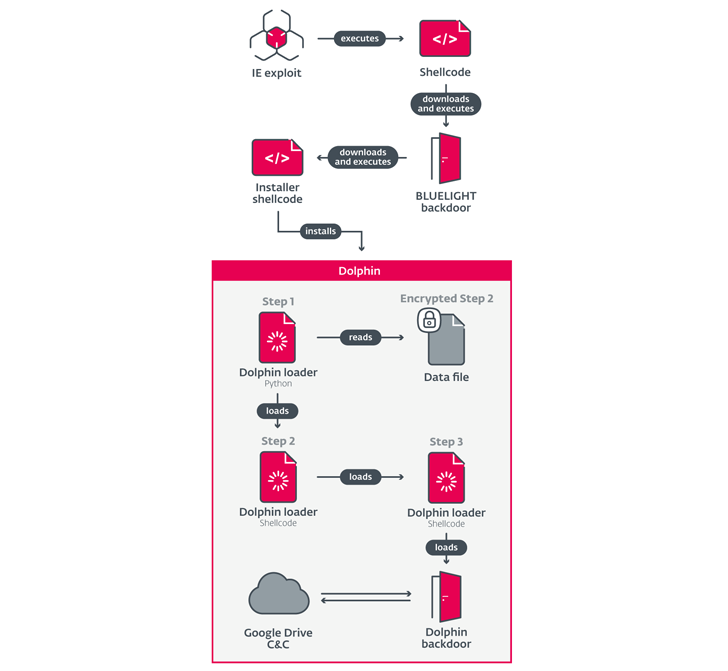
The most recent findings from ESET make clear a second, extra subtle backdoor delivered to a small pool of victims by way of BLUELIGHT, indicative of a highly-targeted espionage operation.
This, in flip, is achieved by executing an installer shellcode that prompts a loader comprising a Python and shellcode element, the latter of which runs one other shellcode loader to drop the backdoor.
“Whereas the BLUELIGHT backdoor performs primary reconnaissance and analysis of the compromised machine after exploitation, Dolphin is extra subtle and manually deployed solely towards chosen victims,” Jurčacko defined.
What makes Dolphin much more potent than BLUELIGHT is its potential to go looking detachable units and exfiltrate information of curiosity, similar to media, paperwork, emails, and certificates.
The backdoor, since its unique discovery in April 2021, is alleged to have undergone three successive iterations that include its personal set of function enhancements and grant it extra detection evasion capabilities.
“Dolphin is one other addition to ScarCruft’s intensive arsenal of backdoors abusing cloud storage companies,” Jurčacko stated. “One uncommon functionality present in prior variations of the backdoor is the flexibility to change the settings of victims’ Google and Gmail accounts to decrease their safety, presumably to be able to preserve account entry for the risk actors.”