Testing entry to a bucket with a cross-account KMS key.
I wrote about an entry denied message associated to PutObject on an S3 bucket. Because it turned out and I demonstrated in my final publish the error was on account of encryption. After I turned doff encryption, no drawback. Now I need to work out precisely what coverage I want.
I already confirmed that I checked the Key Coverage in that final publish and my account (together with the position in it that I’m assuming) has full entry to the important thing used to encrypt the information within the bucket.
Hazard — KMS.*
As earlier than to get this working I added KMS * to my IAM Coverage as I did with S3 and added the KMS key again to the S3 bucket. That labored. However we’re not accomplished right here! As earlier than we need to create a zero-trust coverage so let’s see what permissions we actually want.
Let’s evaluation IAM Entry Analyzer once more. Nicely, this isn’t useful. It simply exhibits that KMS was accessed however not which actions.
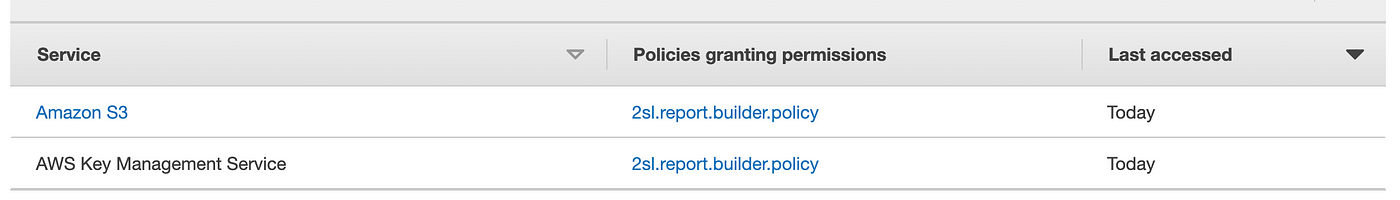
Repair: ^^^ Present which particular actions on KMS this position used so we will create an acceptable coverage.
Nicely, we will have a look at CloudTrail once more. The query is, will the encryption motion be within the native or distant account? Possibly it’s within the distant account and that’s why there’s no hyperlink above. However for the reason that position doesn’t exist within the different account we will’t use IAM Entry Analyzer over there.
Repair: ^^^ Present the actions taken in different accounts with IAM entry analyzer.
Nicely, after I look within the CloudTrail logs within the different account for something with that key ID I solely discover the important thing creation document and no entry failure.
After I look within the CloudTrail logs within the account the place I’m utilizing the important thing, I discover nothing.
I turned on S3 occasion logs as famous in my final publish.
These don’t present any KMS actions both, sadly.
Repair: Higher documentation or logging for cross-account KMS actions.
I suppose I want to determine by trial and error, the minimal actions I want so as to add to my coverage to make use of the important thing.
Am I wanting within the improper place, are the logs not there but, or do they merely not exist? If the logs merely don’t exist for this situation, that’s a bug.
I’m going to maintain in search of these logs however that’s it for now.
Teri Radichel — Comply with me @teriradichel on Twitter
© 2nd Sight Lab 2022
____________________________________________
About this weblog:
Need to study extra about Cybersecurity and Cloud Safety? Take a look at: Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts



