An unknown risk actor has been focusing on Russian entities with a newly found distant entry trojan referred to as Woody RAT for at the least a 12 months as a part of a spear-phishing marketing campaign.
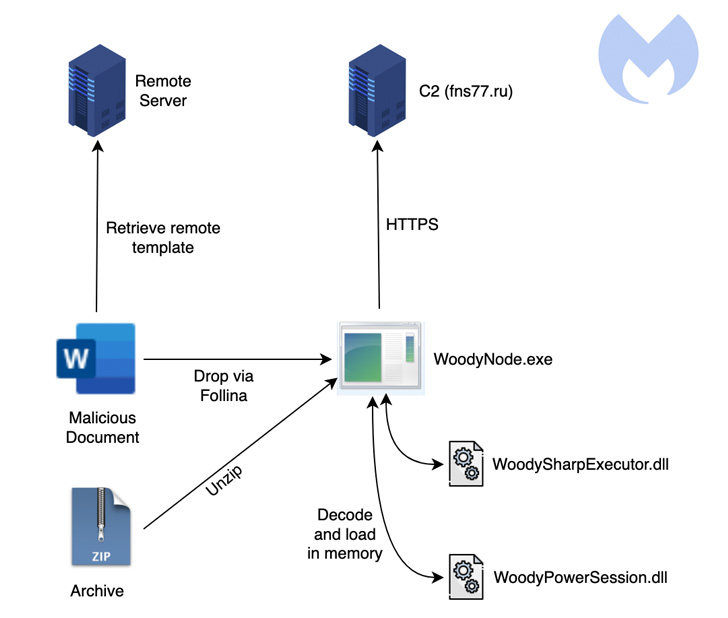
The superior customized backdoor is alleged to be delivered by way of both of two strategies: archive information and Microsoft Workplace paperwork leveraging the now-patched “Follina” assist diagnostic instrument vulnerability (CVE-2022-30190) in Home windows.
Like different implants engineered for espionage-oriented operations, Woody RAT sports activities a variety of options that allows the risk actor to remotely commandeer and steal delicate data from the contaminated methods.
“The earliest variations of this RAT had been sometimes archived right into a ZIP file pretending to be a doc particular to a Russian group,” Malwarebytes researchers Ankur Saini and Hossein Jazi mentioned in a Wednesday report.
“When the Follina vulnerability grew to become recognized to the world, the risk actor switched to it to distribute the payload.”
In a single occasion, the hacking group tried to strike a Russian aerospace and protection entity referred to as OAK primarily based on proof gleaned from a pretend area registered for this function.
Assaults leveraging the Home windows flaw as a part of this marketing campaign first got here to gentle on June 7, 2022, when researchers from the MalwareHunterTeam disclosed the usage of a doc named “Памятка.docx” (which interprets to “Memo.docx”) to ship a CSS payload containing the trojan.
The doc purportedly affords finest safety practices for passwords and confidential data, amongst others, whereas appearing as a decoy for dropping the backdoor.
In addition to encrypting its communications with a distant server, Woody RAT is provided with capabilities to jot down arbitrary information to the machine, execute extra malware, delete information, enumerate directories, seize screenshots, and collect an inventory of working processes.
Additionally embedded throughout the malware are two .NET-based libraries named WoodySharpExecutor and WoodyPowerSession that can be utilized to run .NET code and PowerShell instructions acquired from the server, respectively.
Moreover, the malware makes use of the course of hollowing approach to inject itself right into a suspended Notepad course of and deletes itself from the disk to evade detection from safety software program put in on the compromised host.
Malwarebytes has but to attribute the assaults to a particular risk actor, citing a scarcity of stable indicators linking the marketing campaign to a beforehand recognized group, though Chinese language and North Korean nation-state collectives have focused Russia prior to now.