A sophisticated persistent risk (APT) actor codenamed ToddyCat has been linked to a string of assaults geared toward high-profile entities in Europe and Asia since not less than December 2020.
The comparatively new adversarial collective is claimed to have commenced its operations by concentrating on Microsoft Trade servers in Taiwan and Vietnam utilizing an unknown exploit to deploy the China Chopper internet shell and activate a multi-stage an infection chain.
Different outstanding international locations focused embody Afghanistan, India, Indonesia, Iran, Kyrgyzstan, Malaysia, Pakistan, Russia, Slovakia, Thailand, the U.Okay., and Uzbekistan, simply because the risk actor advanced its toolset over the course of various campaigns.
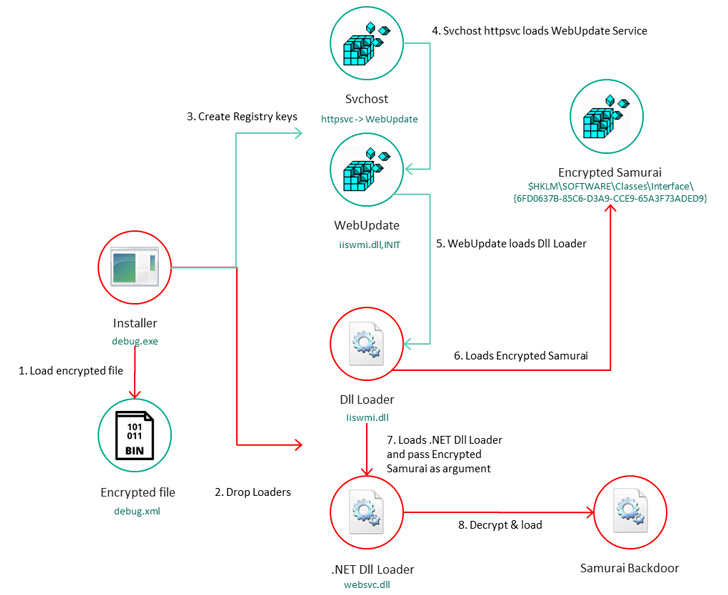
“The primary wave of assaults solely focused Microsoft Trade Servers, which had been compromised with Samurai, a complicated passive backdoor that normally works on ports 80 and 443,” Russian cybersecurity firm Kaspersky mentioned in a report printed right this moment.
“The malware permits arbitrary C# code execution and is used with a number of modules that enable the attacker to administrate the distant system and transfer laterally contained in the focused community.”
ToddyCat, additionally tracked beneath the moniker Websiic by Slovak cybersecurity agency ESET, first got here to gentle in March 2021 for its exploitation of ProxyLogon Trade flaws to focus on e mail servers belonging to personal firms in Asia and a governmental physique in Europe.
The assault sequence put up the deployment of the China Chopper internet shell results in the execution of a dropper that, in flip, is used to make Home windows Registry modifications to launch a second-stage loader, which, for its half, is designed to set off a third-stage .NET loader that is liable for operating Samurai.
The backdoor, moreover utilizing strategies like obfuscation and management stream flattening to make it immune to reverse engineering, is modular in that it the elements make it potential to execute arbitrary instructions and exfiltrate information of curiosity from the compromised host.
Additionally noticed in particular incidents is a complicated instrument named Ninja that is spawned by the Samurai implant and sure features as a collaborative instrument permitting a number of operators to work on the identical machine concurrently.
Its function similarities to different post-exploitation toolkits like Cobalt Strike however, the malware permits the attacker to “management distant methods, keep away from detection, and penetrate deep inside a focused community.”
Even though ToddyCat victims are associated to international locations and sectors historically focused by Chinese language-speaking teams, there isn’t any proof tying the modus operandi to a recognized risk actor.
“ToddyCat is a complicated APT group that makes use of a number of strategies to keep away from detection and thereby retains a low profile,” Kaspersky safety researcher Giampaolo Dedola mentioned.
“The affected organizations, each governmental and navy, present that this group is targeted on very high-profile targets and might be used to attain vital objectives, probably associated to geopolitical pursuits.”