A novel timing assault found towards the npm’s registry API might be exploited to doubtlessly disclose personal packages utilized by organizations, placing builders prone to provide chain threats.
“By creating a listing of doable bundle names, menace actors can detect organizations’ scoped personal packages after which masquerade public packages, tricking staff and customers into downloading them,” Aqua Safety researcher Yakir Kadkoda mentioned.
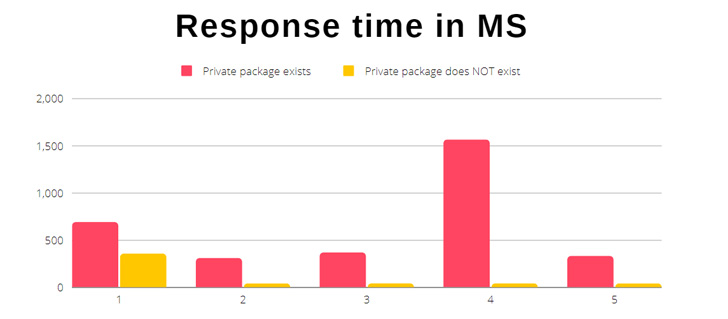
The Scoped Confusion assault banks on analyzing the time it takes for the npm API (registry.npmjs[.]org) to return an HTTP 404 error message when querying for a personal bundle, and measuring it towards the response time for a non-existing module.
“It takes on common much less time to get a reply for a personal bundle that doesn’t exist in comparison with a personal bundle that does,” Kadkoda defined.
The concept, finally, is to establish packages internally utilized by corporations, which may then be utilized by menace actors to create public variations of the identical packages in an try and poison the software program provide chain.
The newest findings are additionally totally different from dependency confusion assaults in that it requires the adversary to first guess the personal packages utilized by a company after which publish phony packages with the identical identify underneath the general public scope.
Dependency confusion (aka namespace confusion), in distinction, depends on the truth that bundle managers verify public code registries for a bundle earlier than personal registries, ensuing within the retrieval of a malicious larger model bundle from the general public repository.
Aqua Safety mentioned it disclosed the bug to GitHub on March 8, 2022, prompting the Microsoft-owned subsidiary to problem a response that the timing assault is not going to be fastened as a result of architectural limitations.
As preventive measures, it is advisable that organizations routinely scan npm and different bundle administration platforms for lookalike or spoofed packages that masquerade as the interior counterparts.
“If you happen to do not discover public packages much like your inside packages, take into account creating public packages as placeholders to forestall such assaults,” Kadkoda mentioned.