A brand new ransomware marketing campaign focused the transportation and logistics sectors in Ukraine and Poland on October 11 with a beforehand unknown payload dubbed Status.
“The exercise shares victimology with latest Russian state-aligned exercise, particularly on affected geographies and nations, and overlaps with earlier victims of the FoxBlade malware (also called HermeticWiper),” the Microsoft Risk Intelligence Middle (MSTIC) stated.
The tech large remarked the intrusions occurred inside an hour of one another throughout all victims, attributing the infections to an unnamed cluster referred to as DEV-0960. It didn’t disclose the dimensions of the assaults, however acknowledged it is notifying all affected clients.
The marketing campaign can also be believed to be distinct from different latest harmful assaults which have concerned using HermeticWiper and CaddyWiper, the latter of which is launched by a malware loader referred to as ArguePatch (aka AprilAxe).
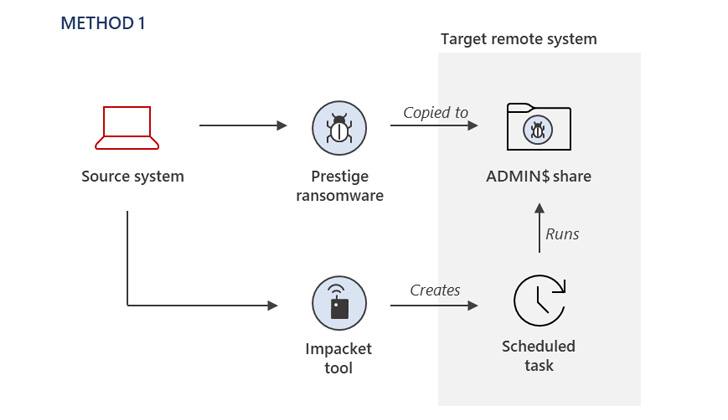
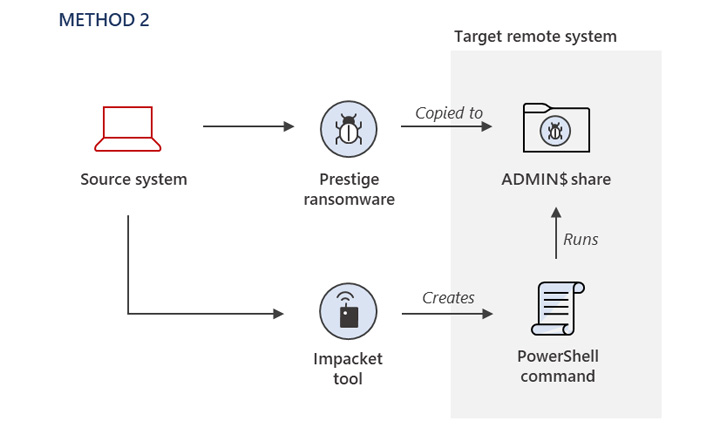
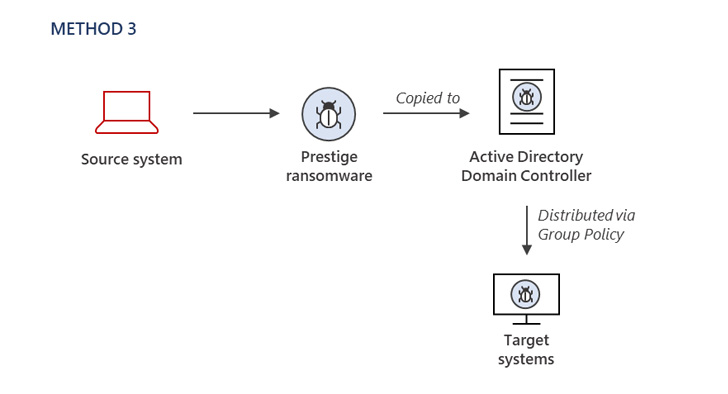
The tactic of preliminary entry stays unknown, with Microsoft noting that the menace actor had already obtained privileged entry to the compromised atmosphere to deploy the ransomware utilizing three totally different strategies.
In a associated growth, Fortinet FortiGuard Labs took the wraps off a multi-stage assault chain that leverages a weaponized Microsoft Excel doc, which masquerades as a spreadsheet for producing salaries for Ukrainian navy personnel to drop Cobalt Strike Beacon.
“The menace panorama in Ukraine continues to evolve, and wipers and harmful assaults have been a constant theme,” Redmond famous. “Ransomware and wiper assaults depend on lots of the similar safety weaknesses to succeed.”
The findings come amid an explosion of comparatively new ransomware strains which were gaining traction on the menace panorama, together with that of Bisamware, Chile Locker, Royal, and Ransom Cartel, over the previous few months.
Ransom Cartel, which surfaced in mid-December 2021, can also be notable for sharing technical overlaps with REvil ransomware, which shut store in October 2021 following immense legislation enforcement scrutiny into its operations after a string of high-profile assaults on JBS and Kaseya.
It is suspected that “Ransom Cartel operators had entry to earlier variations of REvil ransomware supply code,” Palo Alto Networks Unit 42 noticed on October 14, stating that “there was a relationship between the teams in some unspecified time in the future, although it could not have been latest.”
REvil, earlier this January, suffered additional setback when Russian authorities arrested a number of members, however there are indications that the infamous cybercrime cartel could have staged a return in some kind.
Cybersecurity agency Trellix, in late September, additionally revealed how a “disgruntled inside supply” from the group shared particulars in regards to the adversary’s Techniques, Strategies and Procedures (TTPs), lending an important perception into the “relationships and internal workings of REvil and its members.”
It isn’t simply REvil that is again on the ransomware radar. HP Wolf Safety final week stated it remoted a Magniber marketing campaign that has been discovered concentrating on Home windows residence customers with pretend safety updates which make use of a JavaScript file to proliferate the file-encrypting malware.
“The attackers used intelligent methods to evade safety and detection mechanisms,” malware analyst Patrick Schläpfer identified. “A lot of the an infection chain is ‘fileless,’ that means the malware solely resides in reminiscence, decreasing the possibilities of it being detected.”