In keeping with a brand new disclosure discover from the Microsoft 365 Defender Analysis Workforce, cybercriminals are more and more focusing on Microsoft Change servers. Their modus operandi includes abusing OAuth purposes.
Spam Campaigns Involving Malicious OAuth Apps Detected
Though this isn’t the primary time that risk actors have focused Change Server, this marketing campaign is exclusive due to abusing OAuth purposes. These purposes are an integral a part of the assault chain on this occasion.
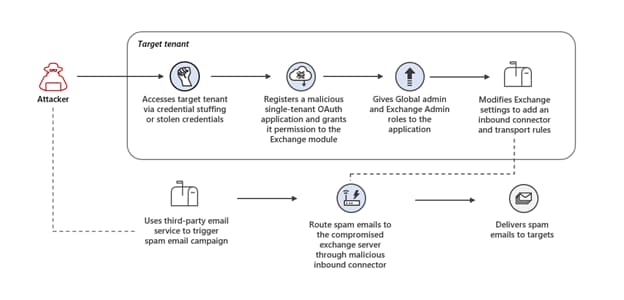
Per MS 365 Defender Analysis, in an incident they analyzed, malicious OAuth purposes had been deployed on compromised cloud tenants, and ultimately, attackers took over Change servers to hold out spam campaigns.
Researchers defined that the risk actor(s) launched a credential-stuffing assault, focusing on high-risk accounts the place customers didn’t allow multifactor authentication. The attacker then leveraged unsecured admin accounts and will achieve preliminary entry.
Afterward, the attacker created a malicious OAuth utility, including an inbound connector to the Change e mail server. Therefore, the actor can ship out spam emails utilizing the goal area.
Beforehand, OAuth purposes had been abused in consent phishing assaults the place attackers attempt to entry cloud providers by tricking customers into permitting permission to malicious OAuth apps. Some state-sponsored actors have additionally abused them for C2 communications, redirections, phishing assaults, and deployment of backdoors.
Marketing campaign Targets Overview
Researchers disclosed of their report that quite a few organizations have been focused in credential stuffing assaults to date. On this marketing campaign, attackers launch assaults towards administrator account that lack MFA and use them to entry the sufferer’s cloud tenant.
This marketing campaign primarily targets shoppers and enterprise tenants, abusing weaknesses within the group’s safety mechanisms and will even result in ransomware and different devastating assaults.
On this assault, in accordance with Microsoft 365 Defender Analysis Workforce report, attackers run spam e mail campaigns, promote for faux sweepstakes by spoofing organizations’ identities, or supply an iPhone as a prize to trick victims into signing up for long-term paid subscriptions.
The marketing campaign makes use of a community of single-tenant apps put in on the compromised group. This helps the attacker achieve an identification platform to launch the assault. As quickly because the marketing campaign was disclosed, all of the malicious OAuth apps had been eliminated. Organizations should implement stringent safety practices to stop such scams. Enabling MFA ought to be the primary line of protection towards such threats.
Associated Information
- Hackers hit Microsoft Change Server to steal e mail information
- European Banking Authority sufferer in Microsoft Change Server hack
- Hackers Utilizing Malicious IIS Extensions to Backdoor Change Servers
- It’s Google.com, not ɢoogle.com; watch out for the pro-Trump spam area
- Spam Campaigns Utilizing Trickbot Banking Trojan In opposition to Cryptocurrencies