A newly found malware has been put to make use of within the wild not less than since March 2021 to backdoor Microsoft Alternate servers belonging to a variety of entities worldwide, with infections lingering in 20 organizations as of June 2022.
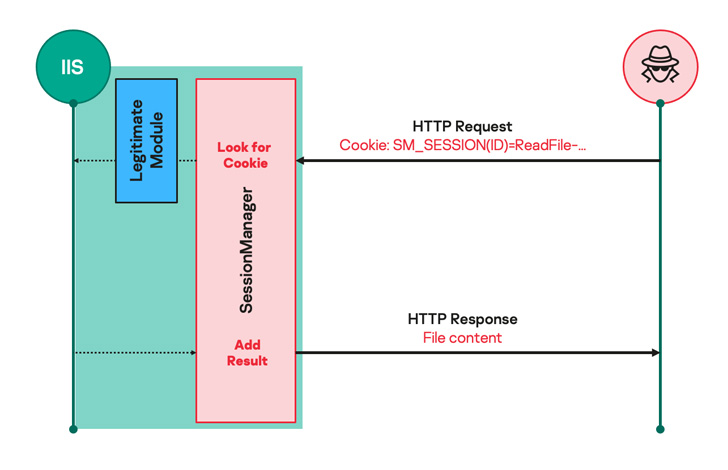
Dubbed SessionManager, the malicious software masquerades as a module for Web Data Providers (IIS), an internet server software program for Home windows techniques, after exploiting one of many ProxyLogon flaws inside Alternate servers.
Targets included 24 distinct NGOs, authorities, navy, and industrial organizations spanning Africa, South America, Asia, Europe, Russia and the Center East. A complete of 34 servers have been compromised by a SessionManager variant so far.
That is removed from the primary time the method has been noticed in real-world assaults. Using a rogue IIS module as a way to distribute stealthy implants mirrors the techniques of a credential stealer known as Owowa that got here to gentle in December 2021.
“Dropping an IIS module as a backdoor permits risk actors to take care of persistent, update-resistant and comparatively stealthy entry to the IT infrastructure of a focused group; be it to gather emails, replace additional malicious entry, or clandestinely handle compromised servers that may be leveraged as malicious infrastructure,” Kaspersky researcher Pierre Delcher stated.
The Russian cybersecurity agency attributed the intrusions with medium-to-high confidence to an adversary tracked as Gelsemium, citing overlaps within the malware samples linked to the 2 teams and victims focused.
ProxyLogon, since its disclosure in March 2021, has attracted the repeated consideration of a number of risk actors, and the most recent assault chain is not any exception, with the Gelsemium crew exploiting the issues to drop SessionManager, a backdoor coded in C++ and is engineered to course of HTTP requests despatched to the server.
“Such malicious modules often count on seemingly reliable however particularly crafted HTTP requests from their operators, set off actions primarily based on the operators’ hidden directions if any, then transparently move the request to the server for it to be processed identical to some other request,” Delcher defined.
Mentioned to be a “light-weight persistent preliminary entry backdoor,” SessionManager comes with capabilities to learn, write, and delete arbitrary recordsdata; execute binaries from the server; and set up communications with different endpoints within the community.
The malware additional acts as a covert channel to conduct reconnaissance, collect in-memory passwords, and ship extra instruments comparable to Mimikatz in addition to a reminiscence dump utility from Avast.
The findings come because the U.S. Cybersecurity and Infrastructure Safety Company (CISA) urged authorities companies and personal sector entities utilizing the Alternate platform to change from the legacy Fundamental Authentication methodology to Trendy Authentication options previous to its deprecation on October 1, 2022.