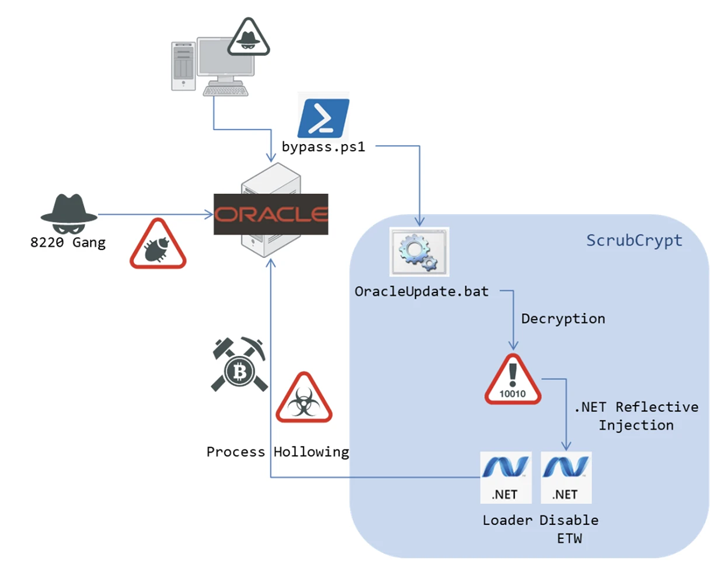
The notorious cryptocurrency miner group referred to as 8220 Gang has been noticed utilizing a brand new crypter referred to as ScrubCrypt to hold out cryptojacking operations.
Based on Fortinet FortiGuard Labs, the assault chain commences with profitable exploitation of prone Oracle WebLogic servers to obtain a PowerShell script that accommodates ScrubCrypt.
Crypters are a sort of software program that may encrypt, obfuscate, and manipulate malware with the objective of evading detection by safety packages.
ScrubCrypt, which is marketed on the market by its writer, comes with options to bypass Home windows Defender protections in addition to verify for the presence of debugging and digital machine environments.
“ScrubCrypt is a crypter used to safe purposes with a singular BAT packing methodology,” safety researcher Cara Lin mentioned in a technical report. “The encrypted knowledge on the prime will be cut up into 4 elements utilizing backslash ‘.'”
The crypter, within the last stage, decodes and masses the miner payload in reminiscence, thereby launching the miner course of.
The risk actor has a monitor document of making the most of publicly disclosed vulnerabilities to infiltrate targets, and the newest findings aren’t any completely different.
Uncover the Hidden Risks of Third-Celebration SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to study in regards to the sorts of permissions being granted and how one can reduce threat.
The event additionally comes as Sydig detailed assaults mounted by the 8220 Gang between November 2022 and January 2023 that intention to breach susceptible Oracle WebLogic and Apache internet servers to drop the XMRig miner.
In late January 2023, Fortinet additionally uncovered cryptojacking assaults that make use of Microsoft Excel paperwork containing malicious VBA macros which might be configured to obtain an executable to mine Monero (XMR) on contaminated methods.