Cybersecurity researchers have found a brand new info stealer dubbed SYS01stealer concentrating on vital authorities infrastructure workers, manufacturing firms, and different sectors.
“The menace actors behind the marketing campaign are concentrating on Fb enterprise accounts by utilizing Google adverts and pretend Fb profiles that promote issues like video games, grownup content material, and cracked software program, and so forth. to lure victims into downloading a malicious file,” Morphisec stated in a report shared with The Hacker Information.
“The assault is designed to steal delicate info, together with login information, cookies, and Fb advert and enterprise account info.”
The Israeli cybersecurity firm stated the marketing campaign was initially tied to a financially motivated cybercriminal operation dubbed Ducktail by Zscaler.
Nevertheless, WithSecure, which first documented the Ducktail exercise cluster in July 2022, stated the two intrusion units are completely different from each other, indicating how the menace actors managed to confuse attribution efforts and evade detection.
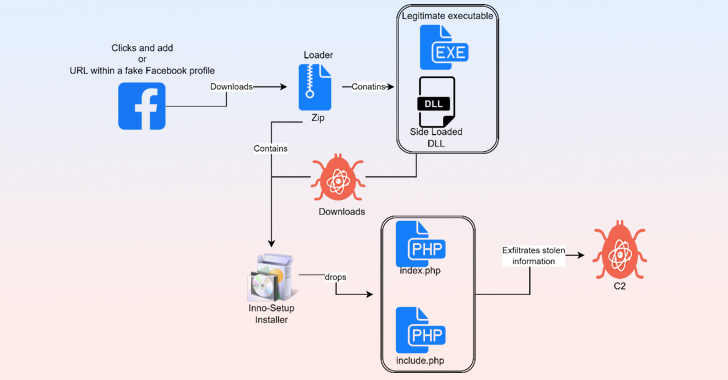
The assault chain, per Morphisec, commences when a sufferer is efficiently lured into clicking on a URL from a faux Fb profile or commercial to obtain a ZIP archive that purports to be cracked software program or adult-themed content material.
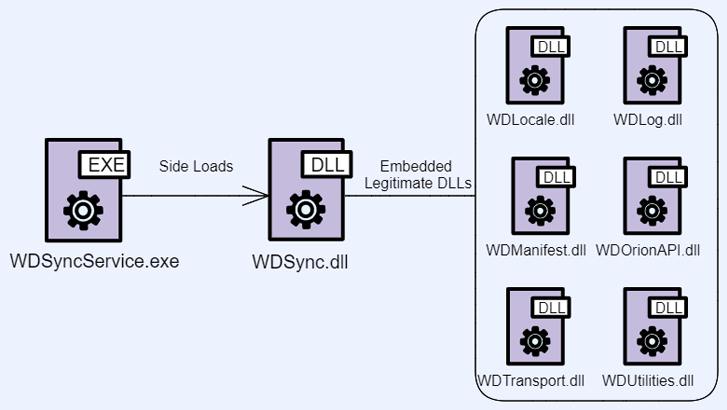
Opening the ZIP file launches a based mostly loader – usually a professional C# software – that is susceptible to DLL side-loading, thereby making it potential to load a malicious dynamic hyperlink library (DLL) file alongside the app.
A few of the functions abused to side-load the rogue DLL are Western Digital’s WDSyncService.exe and Garmin’s ElevatedInstaller.exe. In some cases, the side-loaded DLL acts as a method to deploy Python and Rust-based intermediate executables.
Regardless of the strategy employed, all roads result in the supply of an installer that drops and executes the PHP-based SYS01stealer malware.
The stealer is engineered to reap Fb cookies from Chromium-based internet browsers (e.g., Google Chrome, Microsoft Edge, Courageous, Opera, and Vivaldi), exfiltrate the sufferer’s Fb info to a distant server, and obtain and run arbitrary information.
Uncover the Newest Malware Evasion Techniques and Prevention Methods
Able to bust the 9 most harmful myths about file-based assaults? Be a part of our upcoming webinar and grow to be a hero within the combat in opposition to affected person zero infections and zero-day safety occasions!
It is also geared up to add information from the contaminated host to the command-and-control (C2) server, run instructions despatched by the server, and replace itself when a brand new model is offered.
The event comes as Bitdefender revealed the same stealer marketing campaign often called S1deload that is designed to hijack customers’ Fb and YouTube accounts and leverage the compromised methods to mine cryptocurrency.
“DLL side-loading is a extremely efficient method for tricking Home windows methods into loading malicious code,” Morphisec stated.
“When an software hundreds in reminiscence and search order is just not enforced, the applying hundreds the malicious file as a substitute of the professional one, permitting menace actors to hijack professional, trusted, and even signed functions to load and execute malicious payloads.”