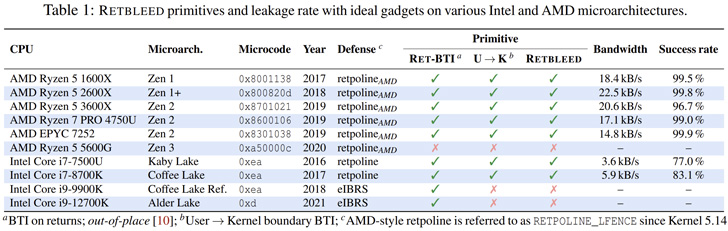
Safety researchers have uncovered one more vulnerability affecting quite a few older AMD and Intel microprocessors that would bypass present defenses and end in Spectre-based speculative-execution assaults.
Dubbed Retbleed by ETH Zurich researchers Johannes Wikner and Kaveh Razavi, the problems are tracked as CVE-2022-29900 (AMD) and CVE-2022-29901 (Intel), with the chipmakers releasing software program mitigations as a part of a coordinated disclosure course of.
Retbleed can be the newest addition to a category of Spectre assaults often known as Spectre-BTI (CVE-2017-5715 or Spectre-V2), which exploit the unwanted side effects of an optimization approach referred to as speculative execution via a timing aspect channel to trick a program into accessing arbitrary places in its reminiscence house and leak personal info.
Speculative execution makes an attempt to fill the instruction pipeline of a program by predicting which instruction can be executed subsequent as a way to acquire a efficiency enhance, whereas additionally undoing the outcomes of the execution ought to the guess become unsuitable.
Assaults like Spectre reap the benefits of the truth that these erroneously executed directions — a results of the misprediction — are certain to go away traces of the execution within the cache, leading to a state of affairs the place a rogue program can trick the processor into executing incorrect code paths and infer secret knowledge pertaining to the sufferer.
Put in a different way, Spectre is an occasion of transient execution assault, which depends on {hardware} design flaws to “affect” which instruction sequences are speculatively executed and leak encryption keys or passwords from inside the sufferer’s reminiscence handle house.
This, in flip, is achieved by microarchitectural aspect channels like Flush+Reload that measures the time taken to carry out reminiscence reads from the cache that is shared with the sufferer, however not earlier than flushing a few of the shared reminiscence, leading to both quick or sluggish reads relying on whether or not the sufferer accessed the monitored cache line because it was evicted.
Whereas safeguards like Retpoline (aka “return trampoline”) have been devised to stop department goal injection (BTI), Retbleed is designed to get round this countermeasure and obtain speculative code execution.
“Retpolines work by changing oblique jumps [branches where the branch target is determined at runtime] and calls with returns,” the researchers defined.
“Retbleed goals to hijack a return instruction within the kernel to realize arbitrary speculative code execution within the kernel context. With adequate management over registers and/or reminiscence on the sufferer return instruction, the attacker can leak arbitrary kernel knowledge.”
The core thought, in a nutshell, is to deal with return directions as an assault vector for hypothesis execution and pressure the returns to be predicted like oblique branches, successfully undoing protections provided by Retpoline.
As a brand new line of protection, AMD has launched what’s known as Jmp2Ret, whereas Intel has advisable utilizing enhanced Oblique Department Restricted Hypothesis (eIBRS) to deal with the potential vulnerability even when Retpoline mitigations are in place.
“Home windows working system makes use of IBRS by default, so no replace is required,” Intel mentioned in an advisory, noting it labored with the Linux group to make obtainable software program updates for the shortcoming.