With speculative execution assaults remaining a stubbornly persistent vulnerability ailing trendy processors, new analysis has highlighted an “{industry} failure” to adopting mitigations launched by AMD and Intel, posing a firmware provide chain risk.
Dubbed FirmwareBleed by Binarly, the data leaking assaults stem from the continued publicity of microarchitectural assault surfaces on the a part of enterprise distributors both because of not accurately incorporating the fixes or solely utilizing them partially.
“The affect of such assaults is targeted on disclosing the content material from privileged reminiscence (together with protected by virtualization applied sciences) to acquire delicate information from processes working on the identical processor (CPU),” the firmware safety agency mentioned in a report shared with The Hacker Information.
“Cloud environments can have a better affect when a bodily server may be shared by a number of customers or authorized entities.”
Lately, implementations of speculative execution, an optimization method that predicts the end result and goal of department directions in a program’s execution pipeline, have been deemed vulnerable to Spectre-like assaults on processor architectures, doubtlessly enabling a risk actor to leak cryptographic keys and different secrets and techniques.
This works by tricking the CPU into executing an instruction that accesses delicate information in reminiscence that may usually be off-limits to an unprivileged utility after which extracting the info after the operation is undone following a misprediction.
A key countermeasure to stop the dangerous results of speculative execution is a software program protection generally known as retpoline (aka “Return Trampoline”), which was launched in 2018.
Though latest findings corresponding to Retbleed have conclusively proven that retpoline by itself is inadequate in opposition to stopping such assaults in sure eventualities, the newest evaluation reveals a scarcity of consistency in even making use of these mitigations within the first place.
Particularly, it takes intention at a finest follow known as Return Stack Buffer (RSB) stuffing launched by Intel to keep away from underflows when utilizing retpoline. RSBs are handle predictors for return (aka RET) directions.
“Sure processors could use department predictors aside from the Return Stack Buffer (RSB) when the RSB underflows,” Intel notes in its documentation. “This may affect software program utilizing the retpoline mitigation technique on such processors.”
“On processors with totally different empty RSB habits, [System Management Mode] code ought to stuff the RSB with CALL directions earlier than coming back from SMM to keep away from interfering with non-SMM utilization of the retpoline method.”
Intel can be recommending RSB stuffing as a mechanism to thwart buffer underflow assaults like Retbleed, alternatively urging distributors to “set [Indirect Branch Restricted Speculation] earlier than RET directions liable to underflow as a consequence of deep name stacks.”
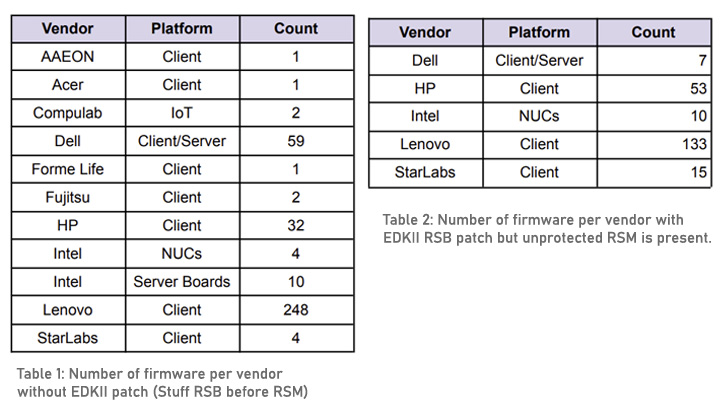
The Binarly analysis, nevertheless, has recognized as many as 32 firmware from HP, 59 from Dell, and 248 from Lenovo as having not included the RSB stuffing patches, underscoring a “failure within the firmware provide chain.”
What’s extra, the deep code evaluation has unearthed cases whereby mitigation was current within the firmware, however contained implementation errors that spawned safety problems with its personal, even in updates launched in 2022 and for units that includes the latest era of {hardware}.
“Firmware provide chain ecosystems are fairly complicated and sometimes include repeatable failures relating to making use of new industry-wide mitigations or fixing reference code vulnerabilities,” the researchers mentioned. “Even when a mitigation is current within the firmware, it does not imply it’s utilized accurately with out creating safety holes.”