Risk actors related to the infamous Emotet malware are frequently shifting their techniques and command-and-control (C2) infrastructure to flee detection, based on new analysis from VMware.
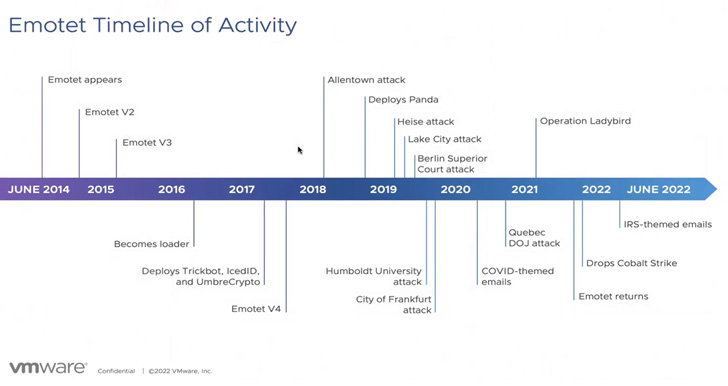
Emotet is the work of a risk actor tracked as Mummy Spider (aka TA542), rising in June 2014 as a banking trojan earlier than morphing into an all-purpose loader in 2016 that is able to delivering second-stage payloads comparable to ransomware.
Whereas the botnet’s infrastructure was taken down as a part of a coordinated legislation enforcement operation in January 2021, Emotet bounced again in November 2021 by means of one other malware often known as TrickBot.
Emotet’s resurrection, orchestrated by the now-defunct Conti workforce, has since paved the best way for Cobalt Strike infections and, extra not too long ago, ransomware assaults involving Quantum and BlackCat.
“The continuing adaptation of Emotet’s execution chain is one motive the malware has been profitable for thus lengthy,” researchers from VMware’s Risk Evaluation Unit (TAU) mentioned in a report shared with The Hacker Information.
Emotet assault flows are additionally characterised by way of totally different assault vectors in an try to remain covert for prolonged intervals of time.
These intrusions usually depend on waves of spam messages that ship malware-laced paperwork or embedded URLs, which, when opened or clicked, result in the deployment of the malware.
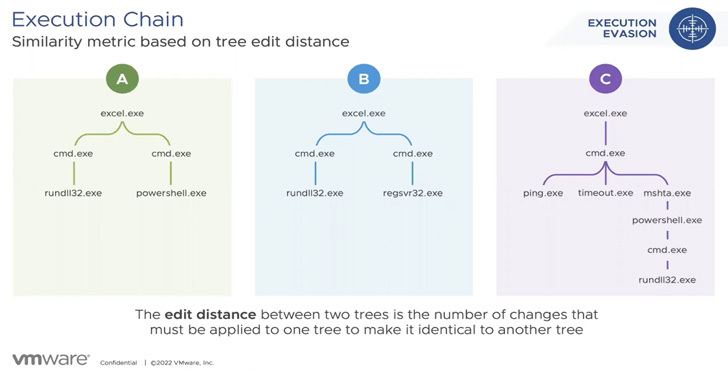
In January 2022 alone, VMware mentioned it noticed three totally different units of assaults by which the Emotet payload was delivered by way of an Excel 4.0 (XL4) macro, an XL4 macro with PowerShell, and a Visible Primary Software (VBA) macro with PowerShell.
A few of these an infection lifecycles had been additionally notable for the abuse of a authentic executable referred to as mshta.exe to launch a malicious HTA file after which drop the Emotet malware.
“Instruments comparable to mshta and PowerShell, that are generally known as living-off-the-land binaries (LOLBINs), are very talked-about amongst risk actors as a result of they’re signed by Microsoft and trusted by Home windows,” the researchers mentioned.
“This permits the attacker to carry out a confused deputy assault, by which authentic instruments are fooled into executing malicious actions.”
Additional evaluation of practically 25,000 distinctive Emotet DLL artifacts exhibits that 26.7% of these had been dropped by Excel paperwork. As many as 139 distinctive program chains have been recognized.
Emotet’s re-emergence has additionally been marked by a change in C2 infrastructure, with the risk actor working two new botnet clusters dubbed Epochs 4 and 5. Previous to the takedown, the Emotet operation ran atop three separate botnets known as Epochs 1, 2, and three.
On prime of that, 10,235 Emotet payloads detected within the wild between March 15, 2022, and June 18, 2022, reused C2 servers belonging to Epoch 5.
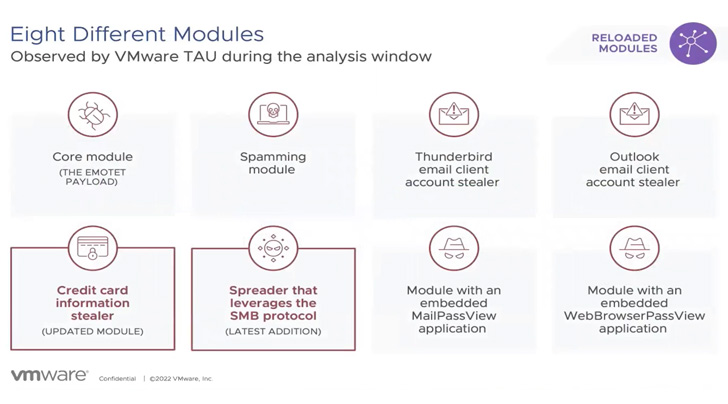
The modifications to each the execution chains and C2 IP addresses apart, Emotet has additionally been noticed distributing two new plugins, one which is designed to seize bank card information from Google Chrome browser, and a spreader module that makes use of the SMB protocol for lateral motion.
Different vital parts embrace a spamming module and account stealers for Microsoft Outlook and Thunderbird e-mail purchasers.
A majority of the IP addresses used to host the servers had been within the U.S., Germany, and France. In distinction, a lot of the Emotet modules had been hosted in India, Korea, Thailand, Ghana, France, and Singapore.
To guard towards threats like Emotet, it is really useful to implement community segmentation, implement a Zero Belief mannequin, and substitute default authentication mechanisms in favor of stronger options.