A brand new malware software that allows cybercriminal actors to construct malicious Home windows shortcut (.LNK) information has been noticed on the market on cybercrime boards.
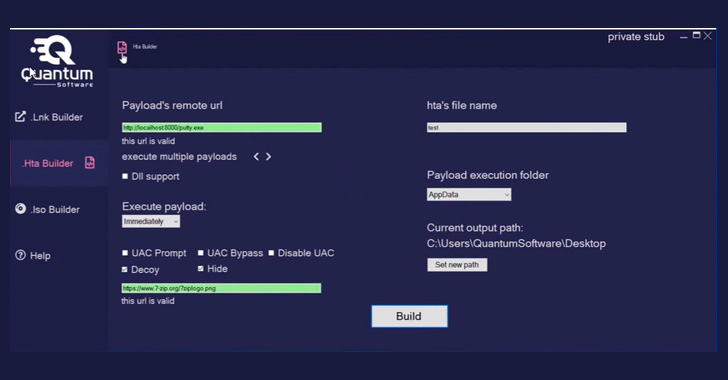
Dubbed Quantum Lnk Builder, the software program makes it potential to spoof any extension and select from over 300 icons, to not point out assist UAC and Home windows SmartScreen bypass in addition to “a number of payloads per .LNK” file. Additionally supplied are capabilities to generate .HTA and disk picture (.ISO) payloads.
Quantum Builder is on the market for lease at totally different value factors: €189 a month, €355 for 2 months, €899 for six months, or as a one-off lifetime buy for €1,500.
“.LNK information are shortcut information that reference different information, folders, or purposes to open them,” Cyble researchers stated in a report. “The [threat actor] leverages the .LNK information and drops malicious payloads utilizing LOLBins [living-off-the-land binaries].”
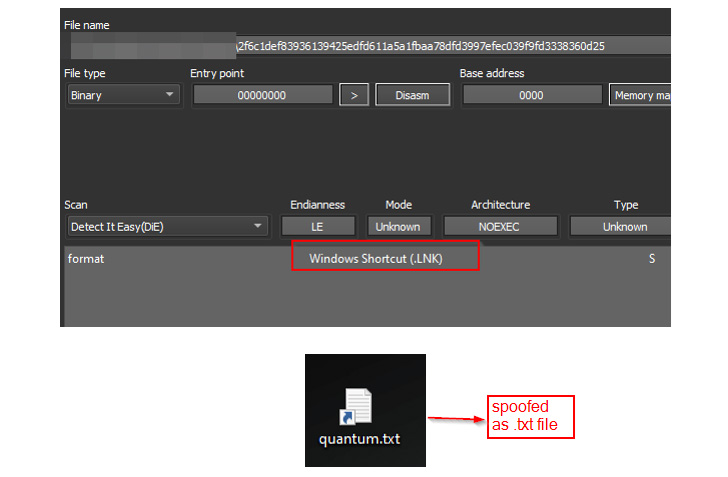
Early proof of malware samples utilizing Quantum Builder within the wild is alleged up to now again to Might 24, masquerading as harmless-looking textual content information (“check.txt.lnk”).
“By default, Home windows hides the .LNK extension, so if a file is called as file_name.txt.lnk, then solely file_name.txt will likely be seen to the person even when the present file extension choice is enabled,” the researchers stated. “For such causes, this is likely to be a beautiful choice for TAs, utilizing the .LNK information as a disguise or smokescreen.”
Launching the .LNK file executes PowerShell code that, in flip, runs a HTML software (“bdg.hta”) file hosted on Quantum’s web site (“quantum-software[.]on-line”) utilizing MSHTA, a official Home windows utility that is used to run HTA information.
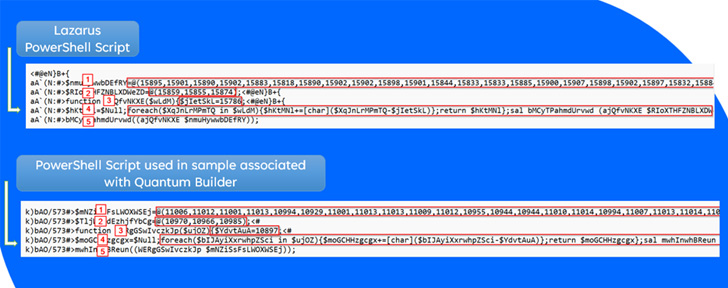
Quantum Builder is alleged to share ties with the North Korean-based Lazarus Group primarily based on supply code-level overlaps within the software and the latter’s modus operandi of leveraging .LNK information for delivering additional stage payloads, indicating its potential use by APT actors of their assaults.
The event comes as operators behind Bumblebee and Emotet are shifting to .LNK information as a conduit to set off the an infection chains following Microsoft’s determination to disable Visible Primary for Purposes (VBA) macros by default throughout its merchandise earlier this 12 months.
Bumblebee, a substitute for BazarLoader malware first noticed in March, capabilities as a backdoor designed to present the attackers persistent entry to compromised programs and a downloader for different malware, together with Cobalt Strike and Sliver.
The malware’s capabilities have additionally made it a software of selection for risk actors, with 413 incidents of Bumblebee an infection reported in Might 2022, up from 41 in April, based on Cyble.
“Bumblebee is a brand new and extremely subtle malware loader that employs in depth evasive maneuvers and anti-analysis tips, together with advanced anti-virtualization methods,” the researchers stated. “It’s prone to change into a well-liked software for ransomware teams to ship their payload.”