Researchers have recognized useful similarities between a malicious part used within the Raspberry Robin an infection chain and a Dridex malware loader, additional strengthening the operators’ connections to the Russia-based Evil Corp group.
The findings recommend that “Evil Corp is probably going utilizing Raspberry Robin infrastructure to hold out its assaults,” IBM Safety X-Drive researcher Kevin Henson mentioned in a Thursday evaluation.
Raspberry Robin (aka QNAP Worm), first found by cybersecurity firm Crimson Canary in September 2021, has remained one thing of a thriller for almost a 12 months, partly owing to the noticeable lack of post-exploitation actions within the wild.
That modified in July 2022 when Microsoft revealed that it noticed the FakeUpdates (aka SocGholish) malware being delivered by way of current Raspberry Robin infections, with potential connections recognized between DEV-0206 and DEV-0243 (aka Evil Corp).
The malware is thought to be delivered from a compromised system by way of contaminated USB gadgets containing a malicious .LNK file to different gadgets within the goal community. The Home windows Shortcut information are designed to retrieve a malicious DLL from a distant server.
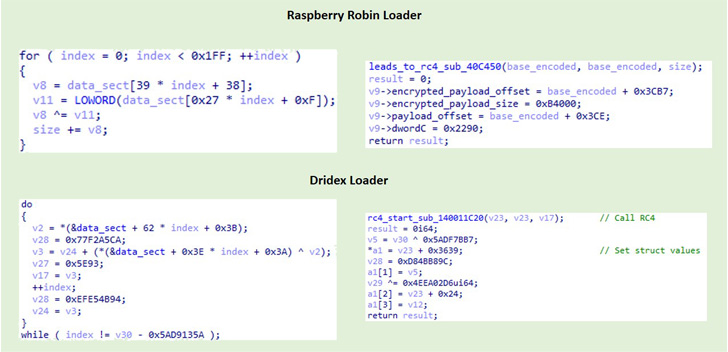
“The Raspberry Robin loaders are DLLs that decode and execute an intermediate loader,” Henson mentioned. “The intermediate loader performs hook detection as an anti-analysis method, decodes its strings at runtime after which decodes a extremely obfuscated DLL whose objective has not been decided.”
Moreover, IBM Safety X-Drive’s comparative evaluation of a 32-bit Raspberry Robin loader and a 64-bit Dridex loader uncovered overlaps in performance and construction, with each elements incorporating related anti-analysis code and decoding the ultimate payload in an identical method.
Dridex (aka Bugat or Cridex) is the handiwork of Evil Corp and refers to a banking trojan with capabilities to steal info, deploy extra malware similar to ransomware, and enslave compromised Home windows machines right into a botnet.
To mitigate Raspberry Robin infections, it is really useful that organizations monitor USB gadget connections and disable the AutoRun function within the Home windows working system settings.