A PHP model of an information-stealing malware referred to as Ducktail has been found within the wild being distributed within the type of cracked installers for respectable apps and video games, in response to the newest findings from Zscaler.
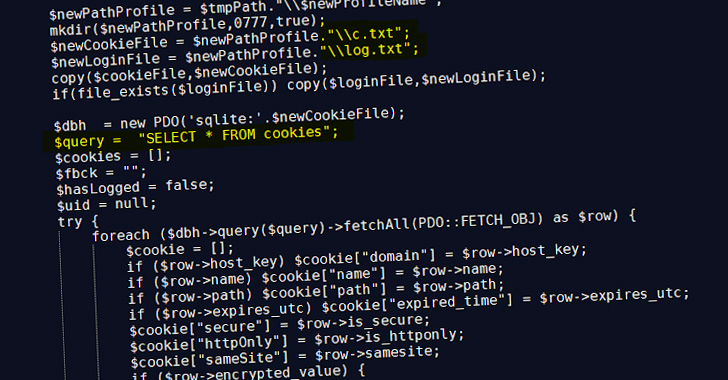
“Like older variations (.NetCore), the newest model (PHP) additionally goals to exfiltrate delicate data associated to saved browser credentials, Fb account data, and so on.,” Zscaler ThreatLabz researchers Tarun Dewan and Stuti Chaturvedi mentioned.
Ducktail, which emerged on the risk panorama in late 2021, is attributed to an unnamed Vietnamese risk actor, with the malware primarily designed to hijack Fb enterprise and promoting accounts.
The financially motivated cybercriminal operation was first documented by Finnish cybersecurity firm WithSecure (previously F-Safe) in late July 2022.
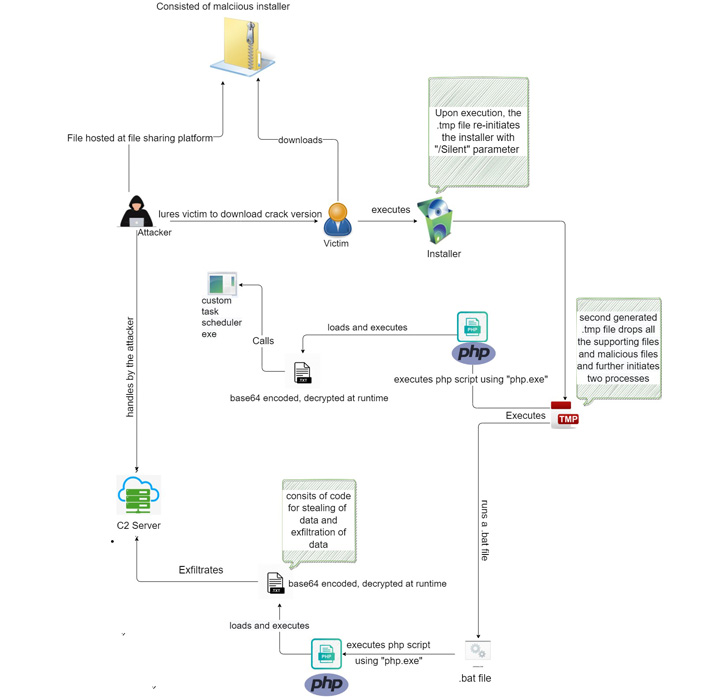
Whereas earlier variations of the malware had been discovered to make use of Telegram as a command-and-control (C2) channel to exfiltrate data, the PHP variant noticed in August 2022 establishes connections to a newly hosted web site to retailer the info in JSON format.
Assault chains noticed by Zscaler entail embedding the malware in ZIP archive recordsdata hosted on file-sharing companies like mediafire[.]com, masquerading as cracked variations of Microsoft Workplace, video games, and porn-related recordsdata.
Execution of the installer, in flip, prompts a PHP script that finally launches the code answerable for stealing and exfiltrating knowledge from internet browsers, cryptocurrency wallets, and Fb Enterprise accounts.
“It appears that evidently the risk actors behind the Ducktail stealer marketing campaign are constantly making adjustments or enhancement within the supply mechanisms and method to steal all kinds of delicate consumer and system data concentrating on customers at giant,” the researchers mentioned.