 Beneath the guise of figuring out applicant eligibility for a U.S. federal authorities job, this newest phishing assault vegetation the seed for a future assault on the sufferer group.
Beneath the guise of figuring out applicant eligibility for a U.S. federal authorities job, this newest phishing assault vegetation the seed for a future assault on the sufferer group.
We’ve coated loads of cyberattacks right here that leverage a leaked model of Cobalt Strike Beacon to executes PowerShell scripts, log keystrokes, take screenshots, obtain information, and spawn different payloads. However usually, using Cobalt Strike Beacon has been coated along side a accomplished (and profitable) assault on a company.
However safety researchers at Cisco Talos have recognized an assault the place the purpose is just to ship Cobalt Strike Beacon – more likely to utilized by one other risk actor who has bought the entry on the Darkish Internet. Focusing on U.S. and New Zealand victims, the campaigns pose as authorities businesses or commerce unions providing the sufferer help in acquiring a job.
In a single variant of the assault, the malicious Phrase paperwork pull a primary stage VB dropper from bitbucket[.]com which decodes a part of its contents to a second VB dropper, which – in flip – decodes it contents to PowerShell script (this occurs twice, much like the VB droppers), when – lastly – the Cobalt Strike Beacon is downloaded from bitbucket.
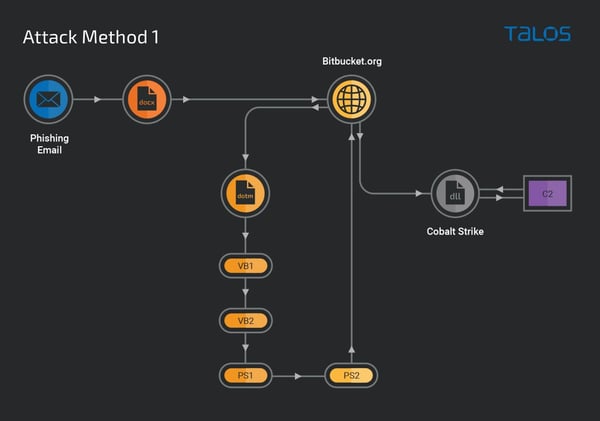
Supply: Cisco Talos
The obfuscation and evasion methods used within the type of repeatedly encoding content material and utilizing two totally different scripting languages demonstrates the lengths attackers will go to as a way to keep away from detection. And the Beacon payload makes this assault much more harmful – because the sufferer organizations at the moment are vulnerable to additional assault.
The inflection level on this assault lies with the sufferer person, who’s most positively not fascinated by whether or not the help e mail (and its’ Phrase doc attachment) are malicious in nature or not. However with correct Safety Consciousness Coaching, customers may be taught to see by means of paperwork that “require” macros be turned on, and so on. for what they are surely: the beginnings of a cyber assault.


