Safety researchers have found a brand new vulnerability referred to as ParseThru affecting Golang-based purposes that could possibly be abused to realize unauthorized entry to cloud-based purposes.
“The newly found vulnerability permits a menace actor to bypass validations beneath sure situations, on account of using unsafe URL parsing strategies constructed within the language,” Israeli cybersecurity agency Oxeye mentioned in a report shared with The Hacker Information.
The difficulty, at its core, has to do with inconsistencies stemming from adjustments launched to Golang’s URL parsing logic that is applied within the “internet/url” library.
Whereas variations of the programming language previous to 1.17 handled semicolons as a sound question delimiter (e.g., instance.com?a=1;b=2&c=3), this conduct has since been modified to throw an error upon discovering a question string containing a semicolon.
“The web/url and internet/http packages used to simply accept “;” (semicolon) as a setting separator in URL queries, along with “&” (ampersand),” in line with the launch notes for model 1.17 launched final August.
“Now, settings with non-percent-encoded semicolons are rejected and internet/http servers will log a warning to ‘Server.ErrorLog’ when encountering one in a request URL.”
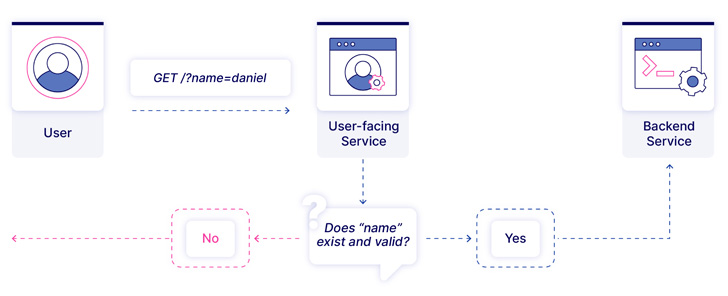
The issue arises when a Golang-based public API constructed upon a model better than 1.17 communicates with an inner service working Golang earlier than 1.17, resulting in a state of affairs the place a malicious actor may smuggle requests incorporating question parameters that might in any other case be rejected.
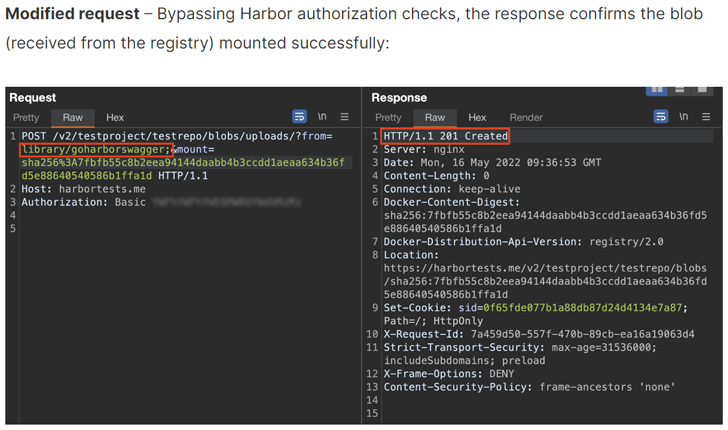
Oxeye mentioned it recognized a number of situations of ParseThru in open-source tasks resembling Harbor, Traefik, and Skipper, which made it potential to bypass validations put in place and perform unauthorized actions.
This isn’t the primary time URL parsing has posed a safety problem. Earlier this January, Claroty and Snyk disclosed as many as eight flaws in third-party libraries written in C, JavaScript, PHP, Python, and Ruby languages that originated on account of confusion in URL parsing.