Researchers have disclosed particulars a couple of safety vulnerability within the Netwrix Auditor utility that, if efficiently exploited, might result in arbitrary code execution on affected units.
“Since this service is usually executed with in depth privileges in an Energetic Listing surroundings, the attacker would possible be capable to compromise the Energetic Listing area,” Bishop Fox stated in an advisory printed this week.
Auditor is an auditing and visibility platform that permits organizations to have a consolidated view of their IT environments, together with Energetic Listing, Alternate, file servers, SharePoint, VMware, and different programs—all from a single console.
Netwrix, the corporate behind the software program, claims greater than 11,500 clients throughout over 100 international locations, reminiscent of Airbus, Virgin, King’s Faculty Hospital, and Credissimo, amongst others.
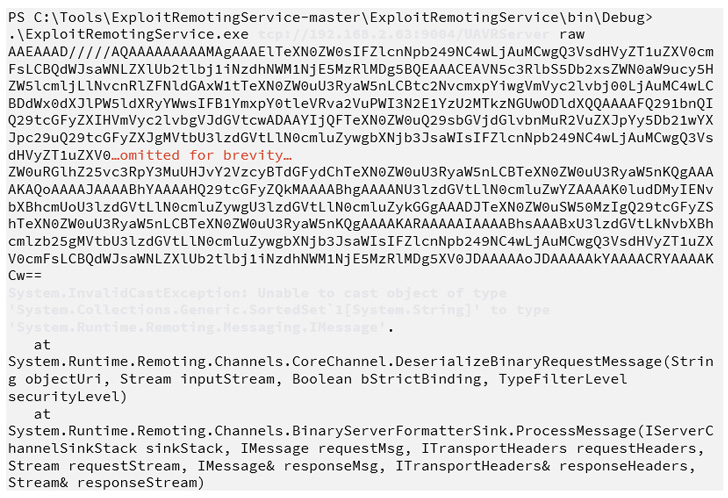
The flaw, which impacts all supported variations previous to 10.5, has been described as an insecure object deserialization, which happens when untrusted user-controllable information is parsed to inflict distant code execution assaults.
The foundation explanation for the bug is an unsecured .NET remoting service that is accessible on TCP port 9004 on the Netwrix server, enabling an actor to execute arbitrary instructions on the server.
“For the reason that command was executed with NT AUTHORITYSYSTEM privileges, exploiting this problem would permit an attacker to completely compromise the Netwrix server,” Bishop Fox’s Jordan Parkin stated.
Organizations counting on Auditor are really useful to replace the software program to the newest model, 10.5, launched on June 6, to thwart any potential dangers.