 Delivering an equally new Royal ransomware, this menace group monitored by Microsoft Safety Menace Intelligence has already proven indicators of spectacular innovation to trick victims.
Delivering an equally new Royal ransomware, this menace group monitored by Microsoft Safety Menace Intelligence has already proven indicators of spectacular innovation to trick victims.
Microsoft retains monitor of recent menace teams, giving them a DEV-#### designation to trace them till there’s confidence round who’s behind the group. Within the case of DEV-0569, this menace group makes use of malvertising, and malicious phishing hyperlinks that time to a malware downloader below the guise of being a reliable software program installers or software program replace, utilizing spam emails, faux discussion board pages, and weblog feedback as preliminary contact factors with potential victims.
In response to Microsoft, the group has expanded its social engineering strategies to enhance their supply of malware, together with delivering phishing hyperlinks by way of contact kinds on the focused organizations’ web site and internet hosting faux installer information on legitimate-looking software program obtain websites and bonafide repositories to make malicious downloads look genuine to their targets.
Take the instance under, the place the menace group hosted their malicious downloader, often called BATLOADER, on a web site that seems to be a TeamViewer obtain web site.
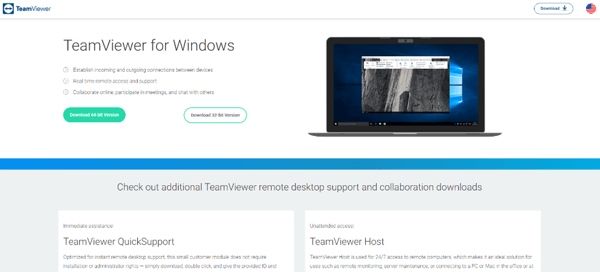
Supply: Microsoft
Microsoft have additionally famous the growth of their malvertising approach to incorporate Google Advertisements in certainly one of their campaigns, establishing legitimacy and mixing in with regular advert site visitors.
This degree of innovation reveals that menace actors are stepping up their recreation to determine legitimacy in any approach potential – together with paying for advertisements – in order that sufferer’s defenses are down. It’s all of the extra motive for organizations to coach their customers via Safety Consciousness Coaching to at all times be watchful, even in conditions the place every little thing appears “regular”; as that reliable search question on Google might lead to enabling malicious exercise.


