A social engineering marketing campaign leveraging job-themed lures is weaponizing a years-old distant code execution flaw in Microsoft Workplace to deploy Cobalt Strike beacons on compromised hosts.
“The payload found is a leaked model of a Cobalt Strike beacon,” Cisco Talos researchers Chetan Raghuprasad and Vanja Svajcer stated in a brand new evaluation printed Wednesday.
“The beacon configuration incorporates instructions to carry out focused course of injection of arbitrary binaries and has a excessive repute area configured, exhibiting the redirection approach to masquerade the beacon’s visitors.”
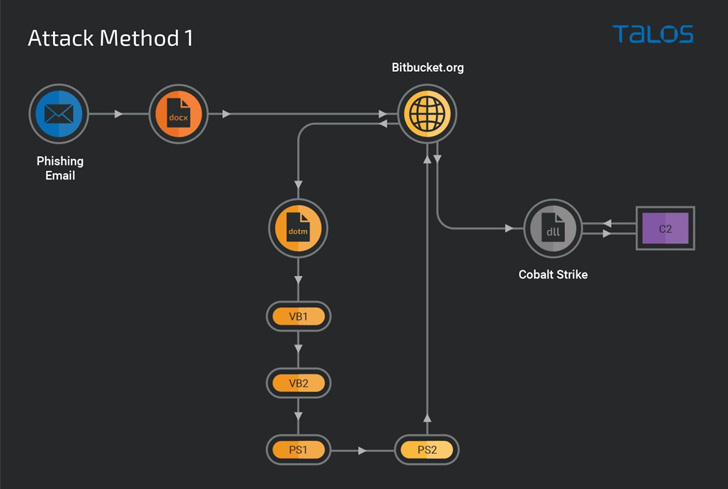
The malicious exercise, found in August 2022, makes an attempt to take advantage of the vulnerability CVE-2017-0199, a distant code execution situation in Microsoft Workplace, that enables an attacker to take management of an affected system.
The entry vector for the assault is a phishing e-mail containing a Microsoft Phrase attachment that employs job-themed lures for roles within the U.S. authorities and Public Service Affiliation, a commerce union primarily based in New Zealand.
Cobalt Strike beacons are removed from the one malware samples deployed, for Cisco Talos stated it has additionally noticed the utilization of the Redline Stealer and Amadey botnet executables as payloads on the different finish of the assault chain.
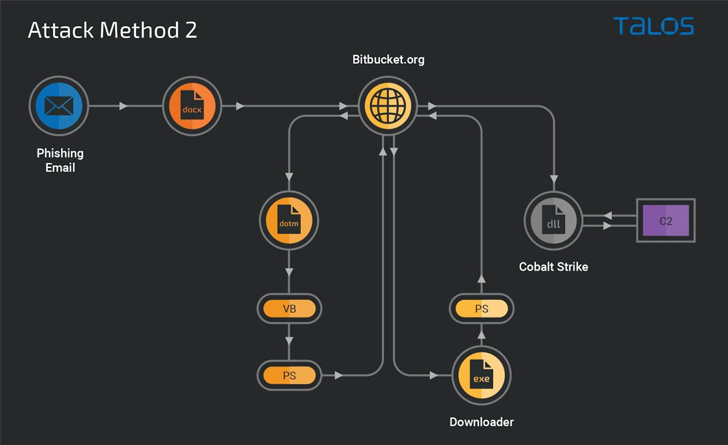
Calling the assault methodology “extremely modularized,” the cybersecurity firm stated the assault additionally stands out for its use of Bitbucket repositories to host malicious content material that serves as a place to begin for downloading a Home windows executable answerable for deploying the Cobalt Strike DLL beacon.
In an alternate assault sequence, the Bitbucket repository features as a conduit to ship obfuscated VB and PowerShell downloader scripts to put in the beacon hosted on a special Bitbucket account.
“This marketing campaign is a typical instance of a menace actor utilizing the strategy of producing and executing malicious scripts within the sufferer’s system reminiscence,” the researchers stated.
“Organizations ought to be consistently vigilant on the Cobalt Strike beacons and implement layered protection capabilities to thwart the attacker’s makes an attempt within the earlier stage of the assault’s an infection chain.”