A never-before-seen Linux malware has been dubbed a “Swiss Military Knife” for its modular structure and its functionality to put in rootkits.
This beforehand undetected Linux risk, known as Lightning Framework by Intezer, is supplied with a plethora of options, making it some of the intricate frameworks developed for focusing on Linux programs.
“The framework has each passive and energetic capabilities for communication with the risk actor, together with opening up SSH on an contaminated machine, and a polymorphic malleable command and management configuration,” Intezer researcher Ryan Robinson mentioned in a brand new report revealed as we speak.
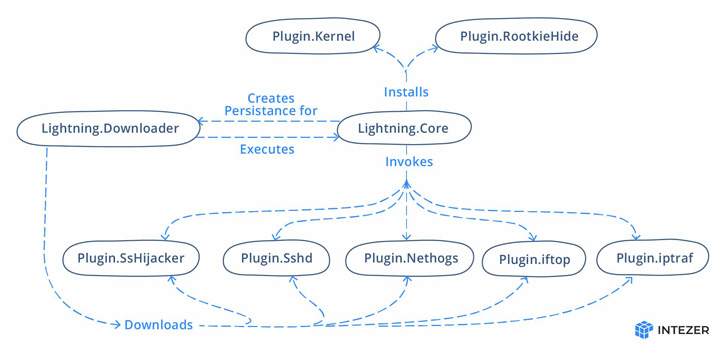
Central to the malware is a downloader (“kbioset”) and a core (“kkdmflush”) module, the previous of which is engineered to retrieve at the least seven totally different plugins from a distant server which can be subsequently invoked by the core part.
As well as, the downloader can also be liable for establishing the persistence of the framework’s major module. “The primary perform of the downloader module is to fetch the opposite parts and execute the core module,” Robinson famous.
The core module, for its half, establishes contact with the command-and-control (C2) server to fetch obligatory instructions required to execute the plugins, whereas additionally taking care to cover its personal presence within the compromised machine.
A few of the notable instructions obtained from the server allow the malware to fingerprint the machine, run shell instructions, add recordsdata to the C2 server, write arbitrary information to file, and even replace and take away itself from the contaminated host.
It additional units up persistence by creating an initialization script that is executed upon system boot, successfully permitting the downloader to be mechanically launched.
“The Lightning Framework is an fascinating malware as it’s not frequent to see such a big framework developed for focusing on Linux,” Robinson identified.
The invention of Lightning Framework makes it the fifth Linux malware pressure to be unearthed in a brief interval of three months after BPFDoor, Symbiote, Syslogk, and OrBit.