Cryptocurrency customers are being focused with a brand new clipper malware pressure dubbed Laplas by way of one other malware often called SmokeLoader.
SmokeLoader, which is delivered by way of weaponized paperwork despatched by means of spear-phishing emails, additional acts as a conduit for different commodity trojans like SystemBC and Raccoon Stealer 2.0, in response to an evaluation from Cyble.
Noticed within the wild since circa 2013, SmokeLoader capabilities as a generic loader able to distributing extra payloads onto compromised programs, reminiscent of information-stealing malware and different implants. In July 2022, it was discovered to deploy a backdoor known as Amadey.
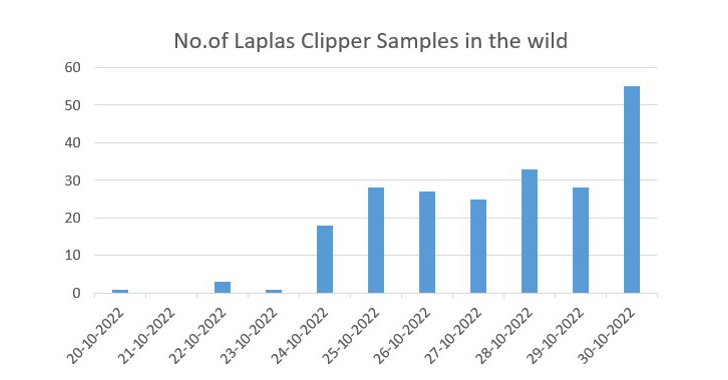
Cyble stated it found over 180 samples of the Laplas since October 24, 2022, suggesting a large deployment.
Clippers, additionally known as ClipBankers, fall below a class of malware that Microsoft calls cryware, that are designed to steal crypto by holding shut tabs on a sufferer’s clipboard exercise and swapping the unique pockets handle, if current, with an attacker-controlled handle.
The objective of clipper malware like Laplas is to hijack a digital foreign money transaction supposed for a professional recipient to that owned by the risk actor.
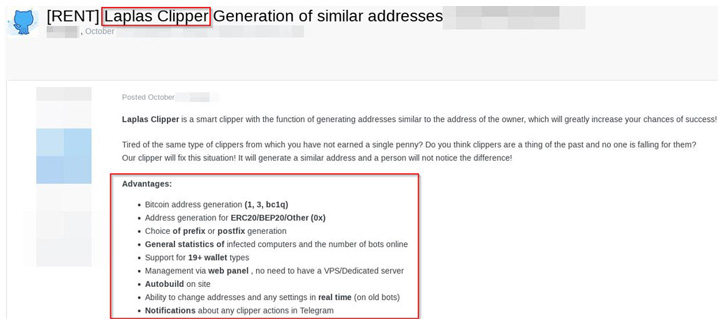
“Laplas is new clipper malware that generates a pockets handle just like the sufferer’s pockets handle,” the researchers identified. “The sufferer is not going to discover the distinction within the handle, which considerably will increase the probabilities of profitable clipper exercise.”
The most recent clipper malware gives help for a wide range of wallets like Bitcoin, Ethereum, Bitcoin Money, Litecoin, Dogecoin, Monero, Ripple, Zcash, Sprint, Ronin, TRON, Cardano, Cosmos, Tezos, Qtum, and Steam Commerce URL. It is priced from $59 a month to $549 a 12 months.
It additionally comes with its personal net panel that permits its purchasers to get details about the variety of contaminated computer systems and the lively pockets addresses operated by the adversary, along with permitting for including new pockets addresses.
“SmokeLoader is a well known, extremely configurable, efficient malware that TAs [threat actors] are actively renovating,” the researchers concluded.
“It’s a modular malware, indicating it will probably get new execution directions from [command-and-control] servers and obtain extra malware for expanded performance. On this case, the TAs use three totally different malware households for monetary acquire and different malicious functions.”